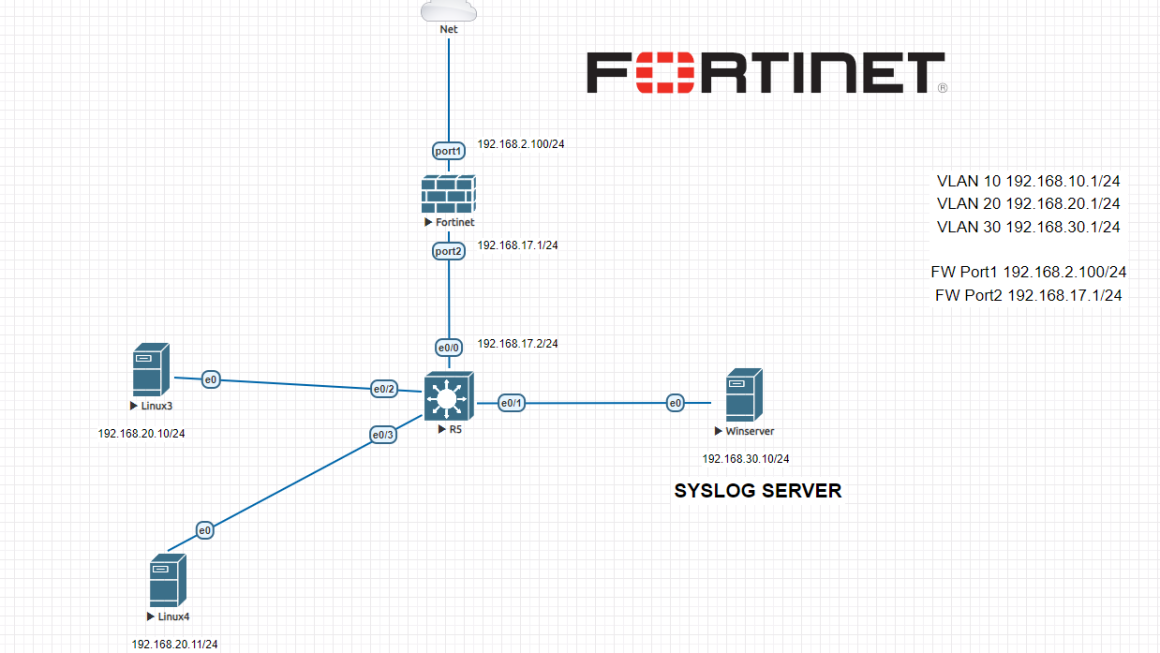
Syslog Integration With Fortigate Firewall
In this lab, we will configure Windows OS based Kiwi Syslog with Fortigate firewall. There are already some enterprise level solutions from Fortigate but this lab is prepared for those who wants to keep their external syslog server on Windows server. There are several syslog application, in this example we choose Kiwi syslog. Also you […]
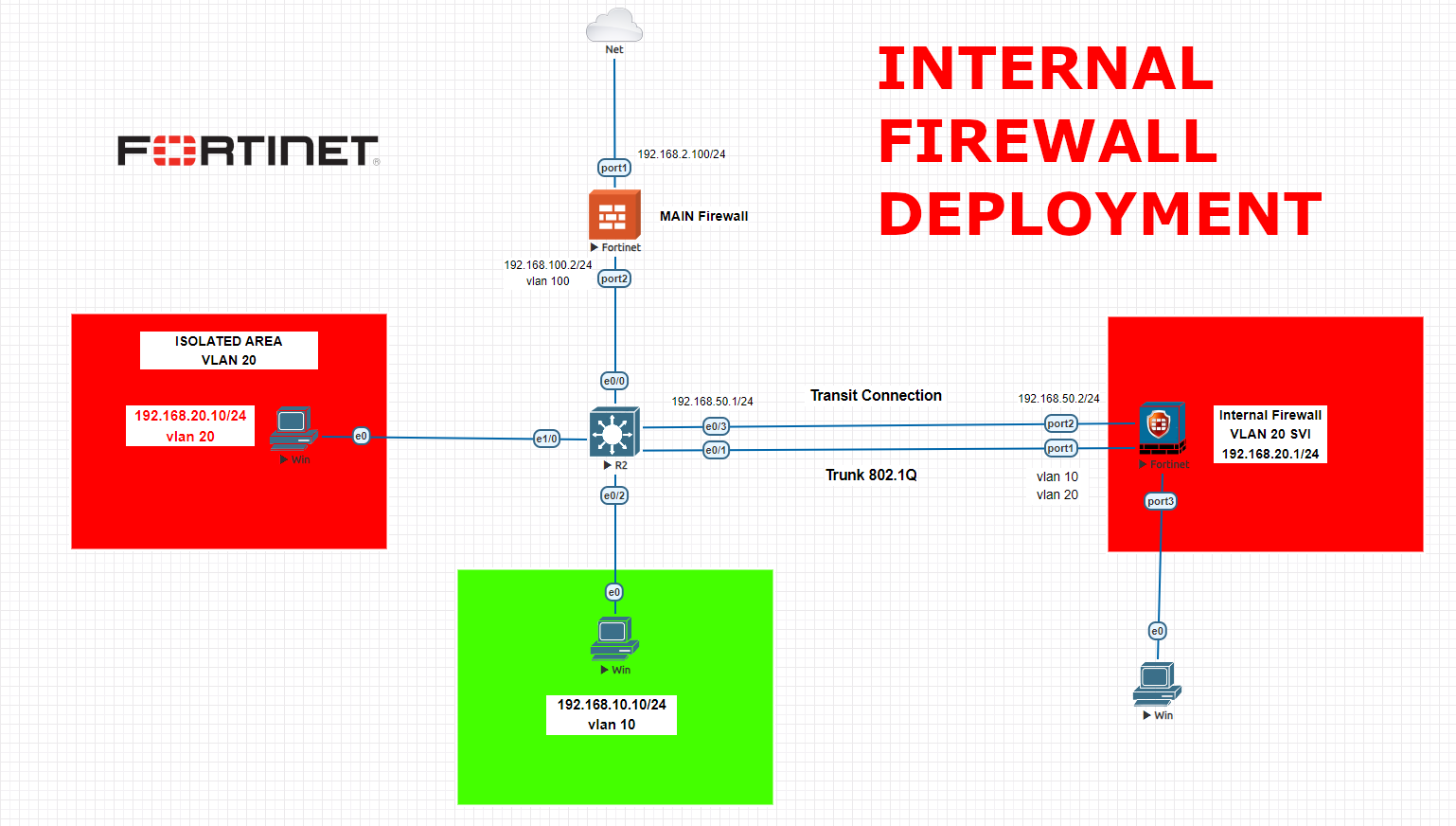
OT/IT Security – Internal Firewall Fortigate Implementation with configurations for your critical networks
An internal firewall, also known as an internal network firewall or a segment firewall, is a security system designed to protect and control traffic between different segments within an organization’s internal network. Unlike a perimeter firewall, which protects the network from external threats, an internal firewall focuses on securing the internal network by regulating the […]
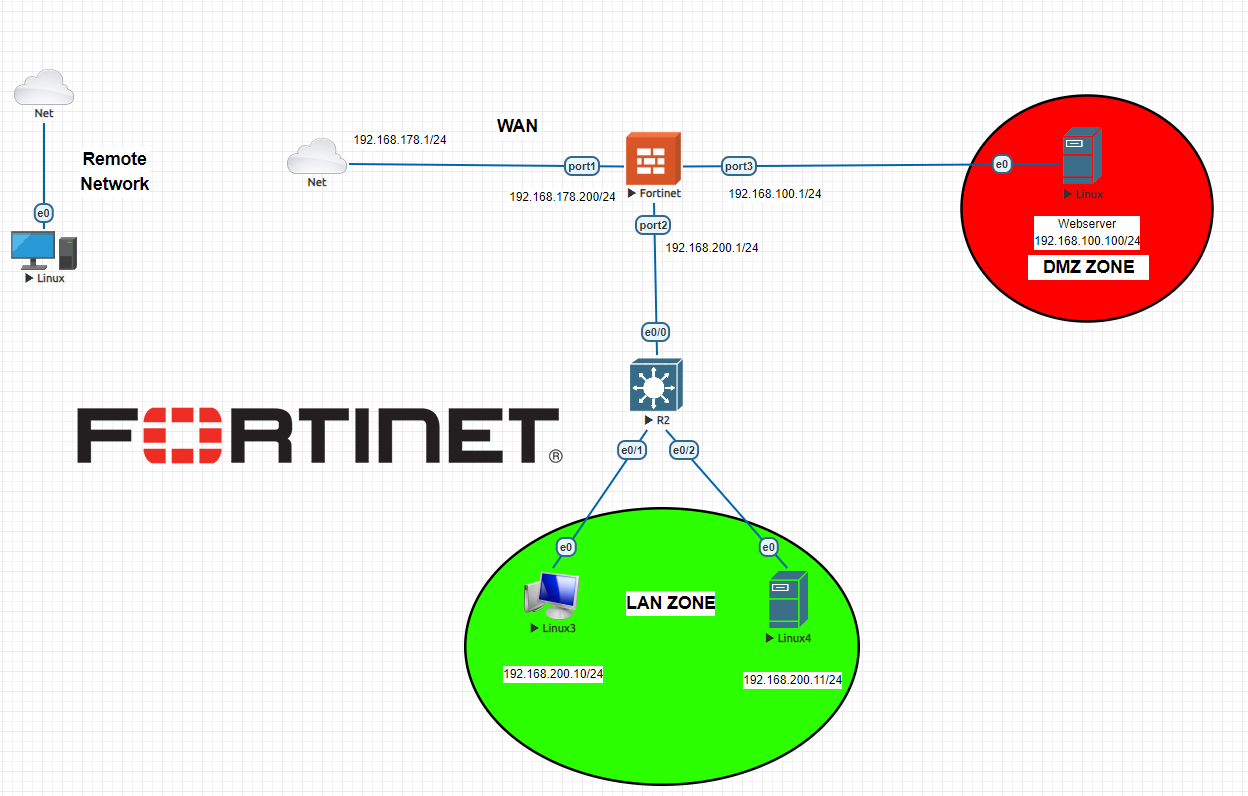
How to create DMZ (Demilitarized Zone) on Fortigate Firewall?
What is DMZ (Demilitarized Zone)? A DMZ (Demilitarized Zone) in computer networking refers to a physical or logical subnetwork that contains and exposes an organization’s external-facing services to an untrusted network, usually the internet. The purpose of a DMZ is to add an additional layer of security to an organization’s local area network (LAN); an […]
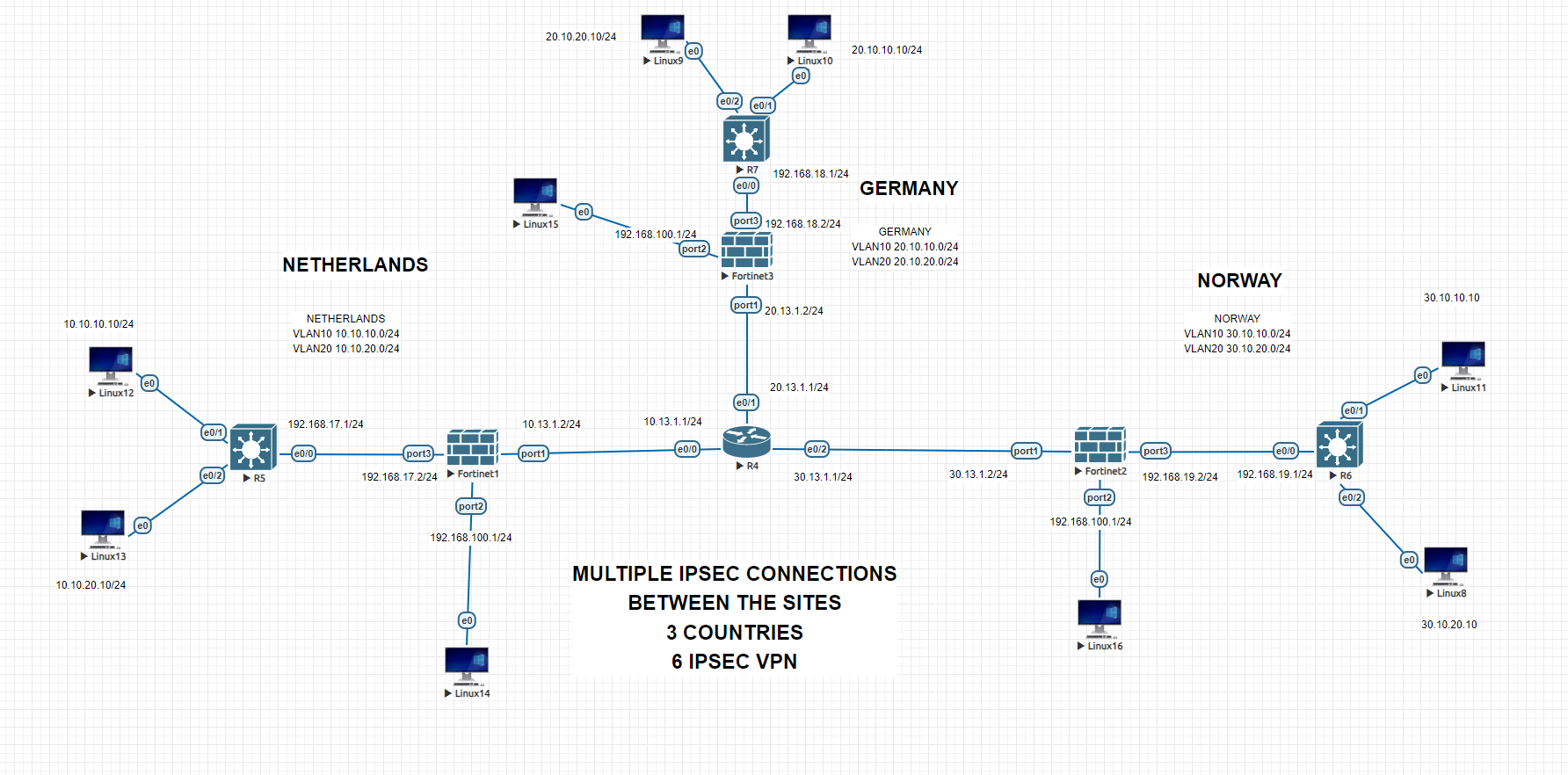
Multiple company-sites IPSEC connection with multiple VLANs
IPsec, short for Internet Protocol Security, is a suite of protocols used to ensure secure communication over IP networks. It provides security services at the IP layer by enabling encryption, authentication, and integrity checking of IP packets. IPsec can be used to establish secure VPN (Virtual Private Network) connections between remote networks or individual devices, […]
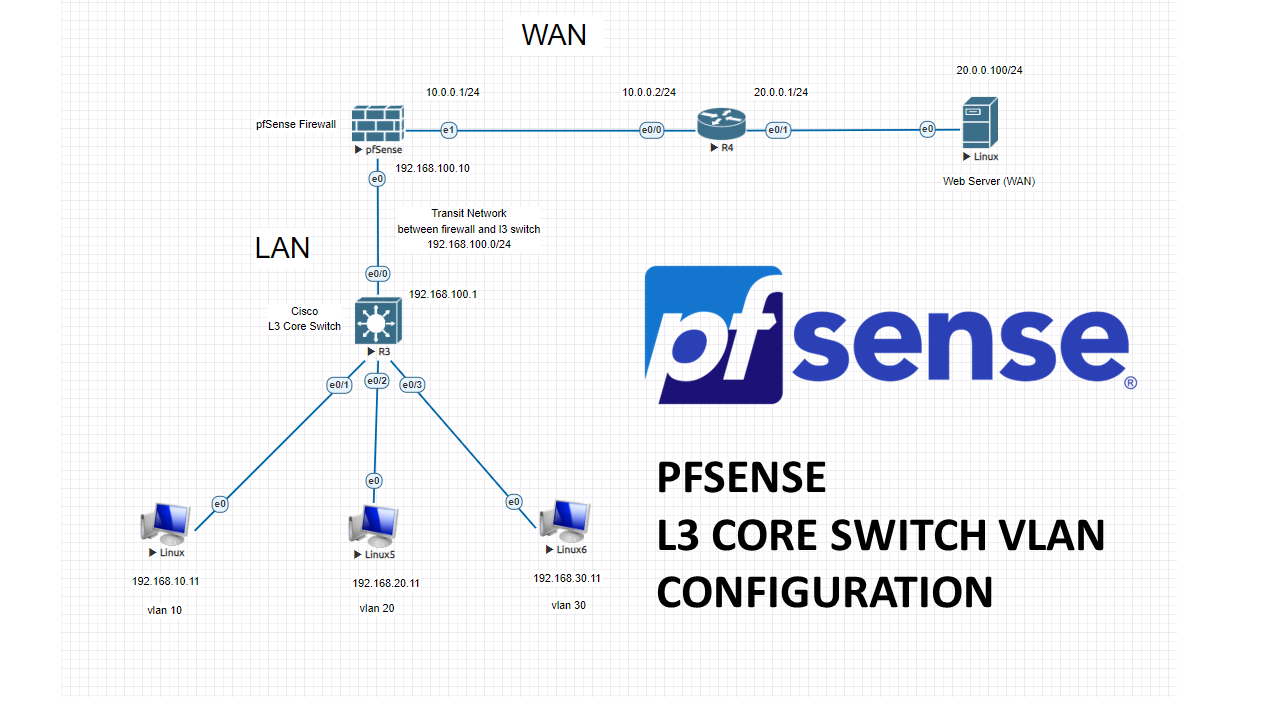
PfSense firewall + L3 Core switch configuration with VLANs
In this lab, we will create 3 vlans and connect our core switch to pfSense firewall with a transit network. Then we will configure our firewall with these vlan subnets. LAN related traffic will not hit the firewall, because SVIs (VLANgateways) will be created on L3 Core switch. All the necessary permissions between vlans will […]
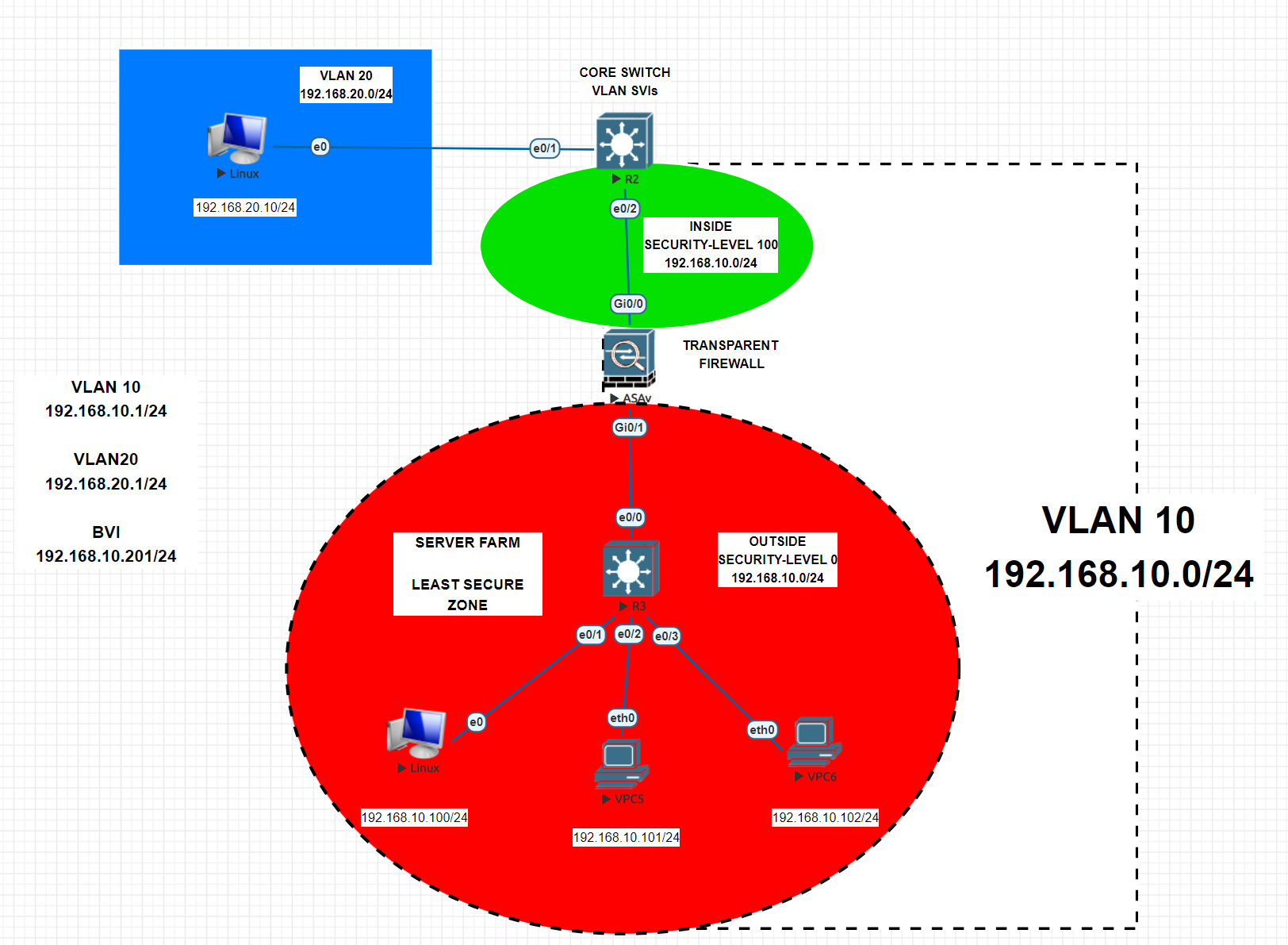
Cisco ASA Transparent Internal Firewall Configuration
Cisco ASA (Adaptive Security Appliance) is a security device that provides firewall, VPN, and other security services for networks. It can operate in multiple modes, including Routed Mode and Transparent Mode. Let’s focus on Cisco ASA Transparent Mode. In Transparent Mode, the Cisco ASA firewall is inserted into a network without requiring any IP address […]
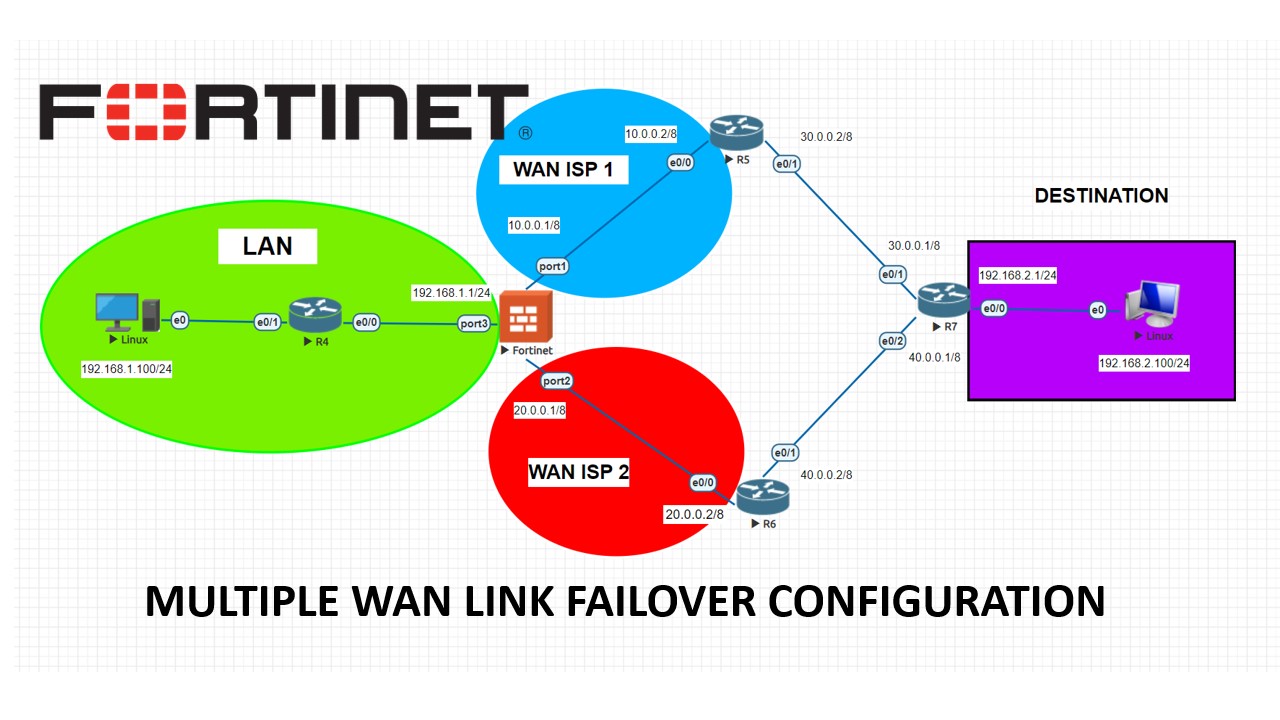
Fortinet Firewall – Multiple WAN ISP Basic Failover
On our topology, we have Fortigate firewall, Cisco routers and 2 ISP provider with 20.0.0.2 and 10.0.0.2 gateways. We would like to setup a basic failover on Fortigate firewall which will allow us to use 2nd ISP link if ISP-1 drops. Basic idea behind this is “administrative distance” on Static routes on the firewall. We […]
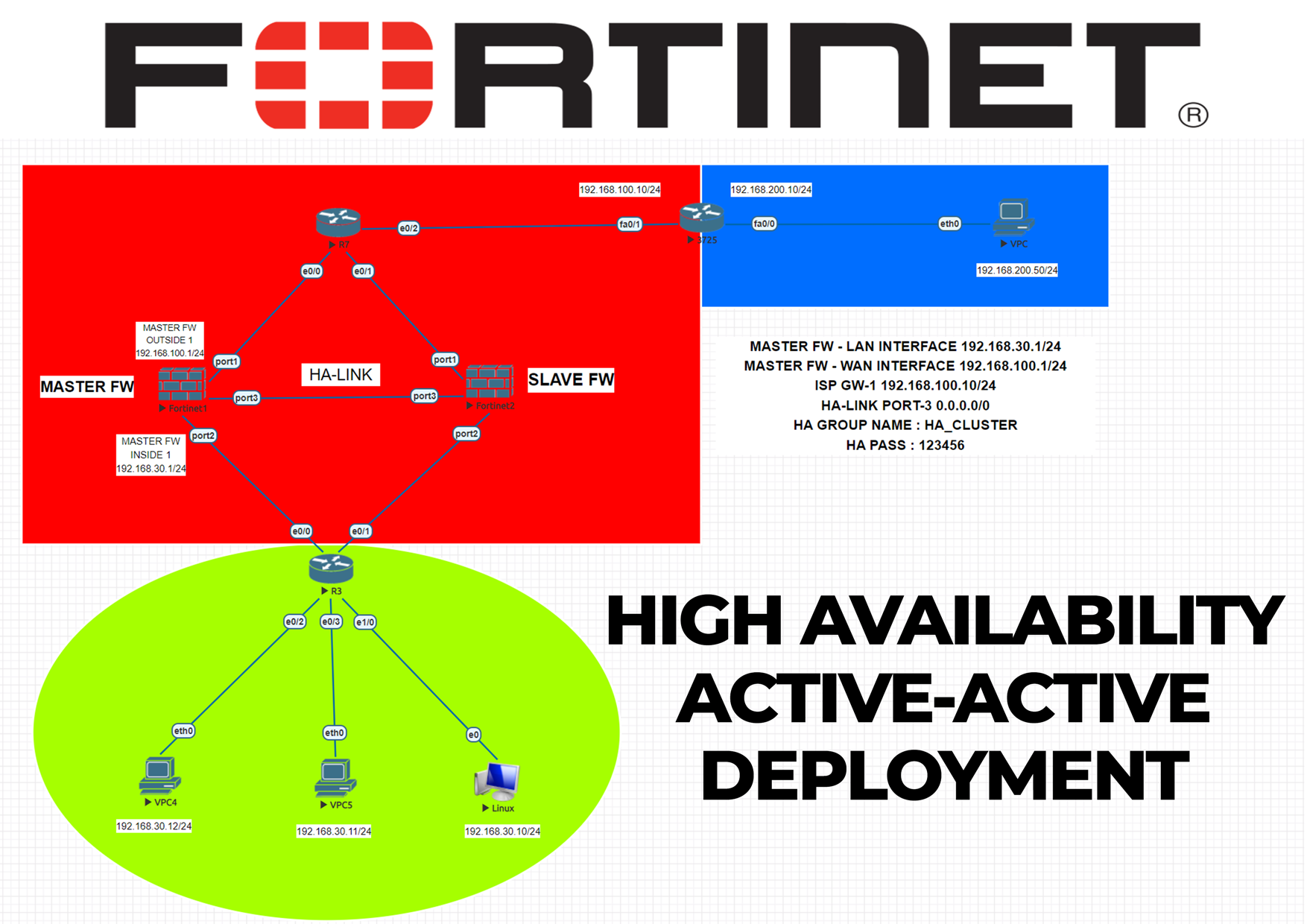
Fortigate Firewall HA (High availability) Deployment
Deploying high availability (HA) on Fortinet FortiGate firewalls offers several benefits, including: On this topology we have two Fortinet Fortigate firewalls, two network switches, one router, four end-users. We will complete all the physical connections between devices, then jump into Fortigate configurations. We will start configuring Master Firewall with 3 interfaces, LAN-WAN-HA LINK. Second firewall […]
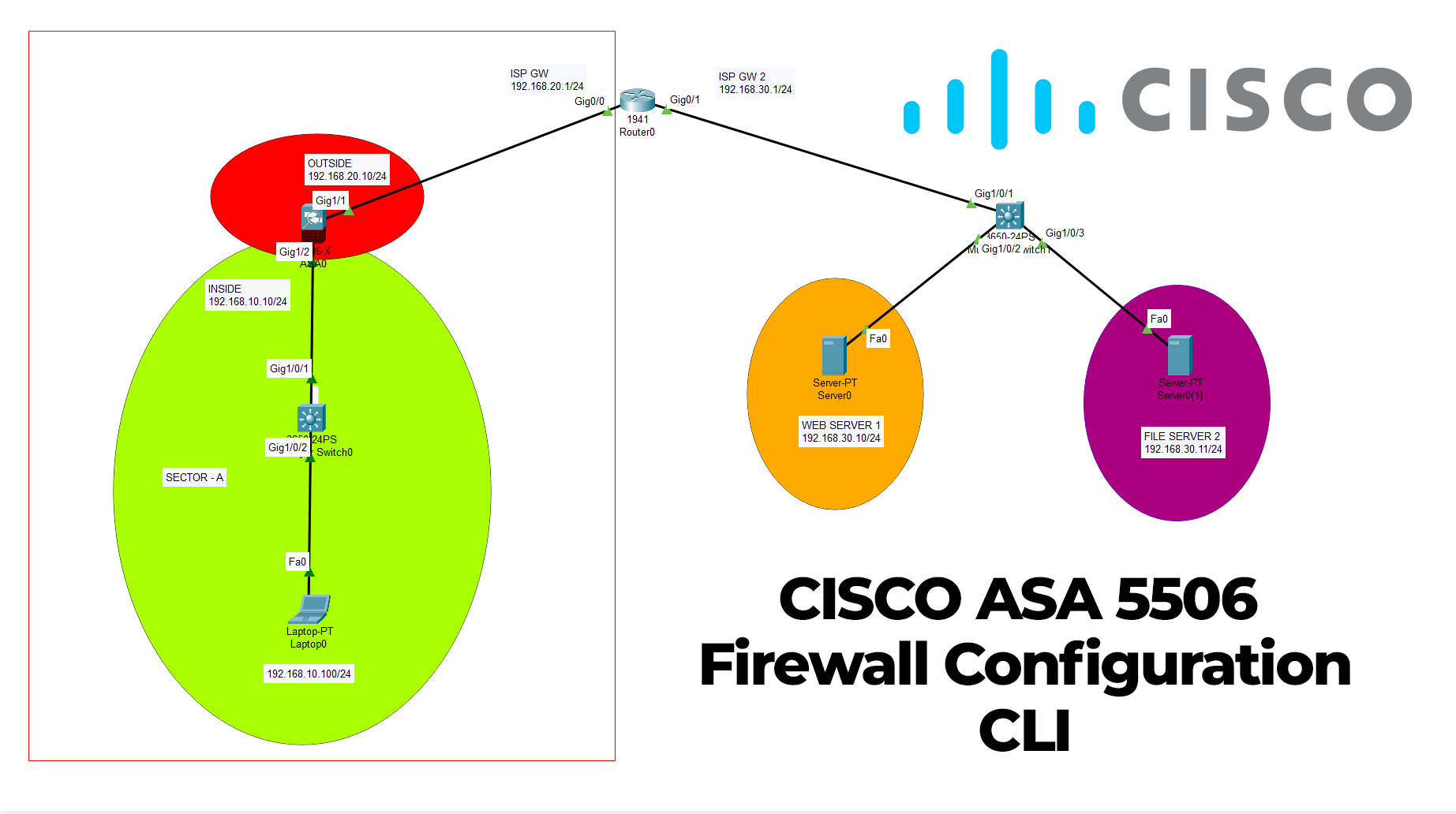
Cisco ASA 5506 firewall initial deployment with CLI
Cisco ASA (Adaptive Security Appliance) is a firewall and network security device produced by Cisco Systems. It provides advanced firewall, VPN (Virtual Private Network), and intrusion prevention capabilities to protect networks from unauthorized access, threats, and attacks. The Cisco ASA firewall offers both hardware and software components, including a dedicated security operating system called Cisco […]
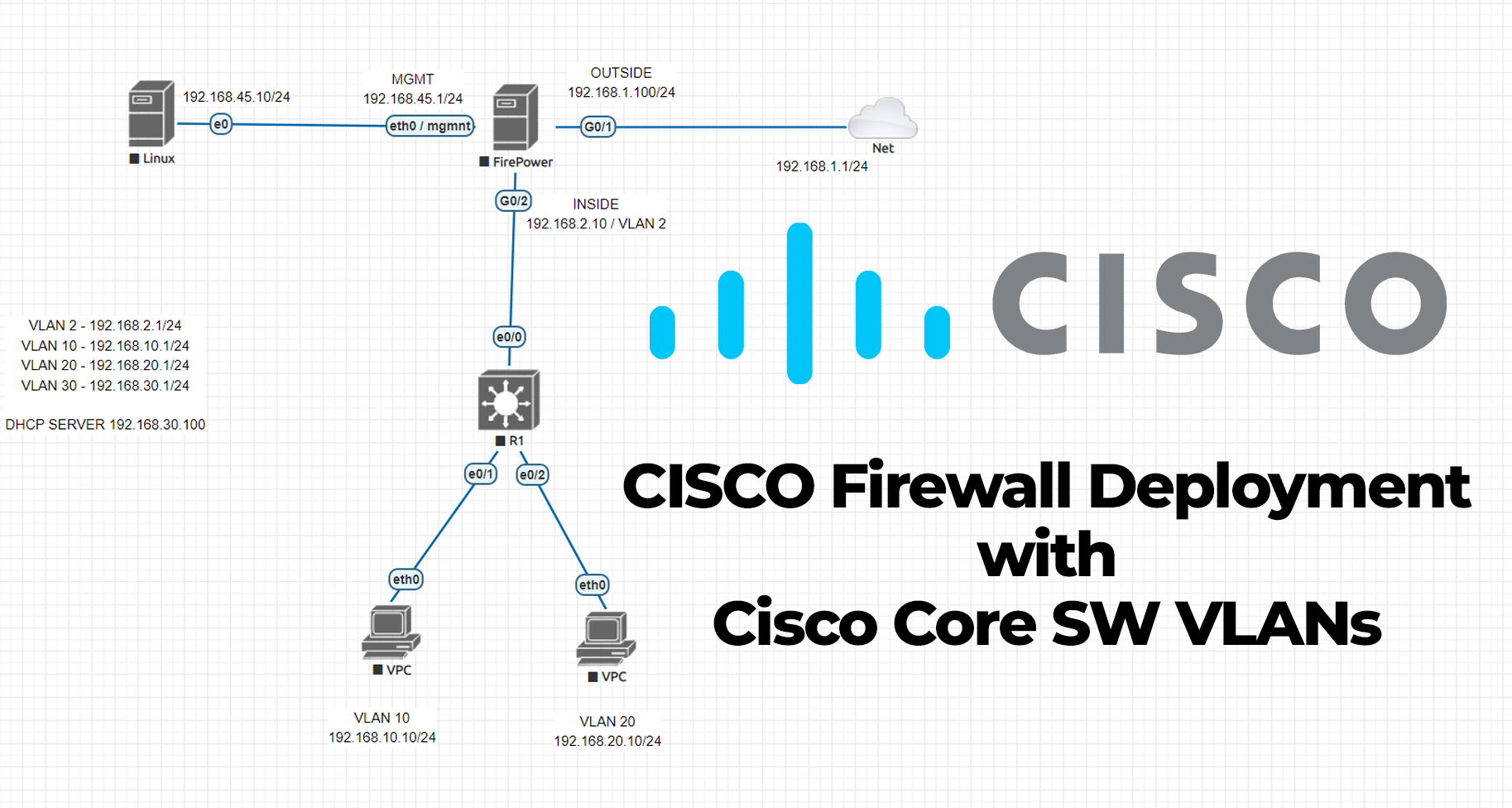
Cisco ASA Firewall deployment via Cisco L3 Switch with VLANs.
In this post, we will be talking about the Cisco firewall installation and integration with VLANs installed Cisco Core L3 switch. I know, probably most of you had some troubles while you were implementing this topology 🙂 I would like to share all the details that I configured on real devices. What do we need […]