Deploying high availability (HA) on Fortinet FortiGate firewalls offers several benefits, including:
- Continuous Uptime: HA ensures uninterrupted network connectivity and minimizes downtime. In the event of a hardware failure, network traffic is automatically redirected to the secondary FortiGate unit, maintaining seamless operation.
- Enhanced Reliability: HA provides redundancy by synchronizing configurations, connections, and sessions between primary and secondary FortiGate units. This redundancy ensures that if one unit fails, the other can seamlessly take over without disrupting network operations.
- Load Balancing: HA enables load balancing, distributing network traffic across multiple FortiGate units. This helps optimize resource utilization, prevents bottlenecks, and ensures optimal performance.
- Faster Failover: In the event of a primary unit failure, failover to the secondary unit occurs swiftly and automatically. This rapid failover minimizes service disruptions and ensures minimal impact on network operations.
- Simplified Maintenance: With HA, you can perform maintenance tasks such as firmware upgrades, software updates, or hardware replacements without interrupting network services. The secondary unit takes over the workload during maintenance, ensuring continuous operations.
- Scalability: High availability allows for easy scalability by adding additional FortiGate units to the HA cluster. As your network requirements grow, you can expand the HA cluster to handle increased traffic and provide greater reliability.
- Centralized Management: Fortinet’s FortiGate devices can be centrally managed using Fortinet’s FortiManager, which simplifies configuration, monitoring, and reporting across multiple FortiGate units in the HA cluster. This centralized management enhances efficiency and reduces administrative overhead.
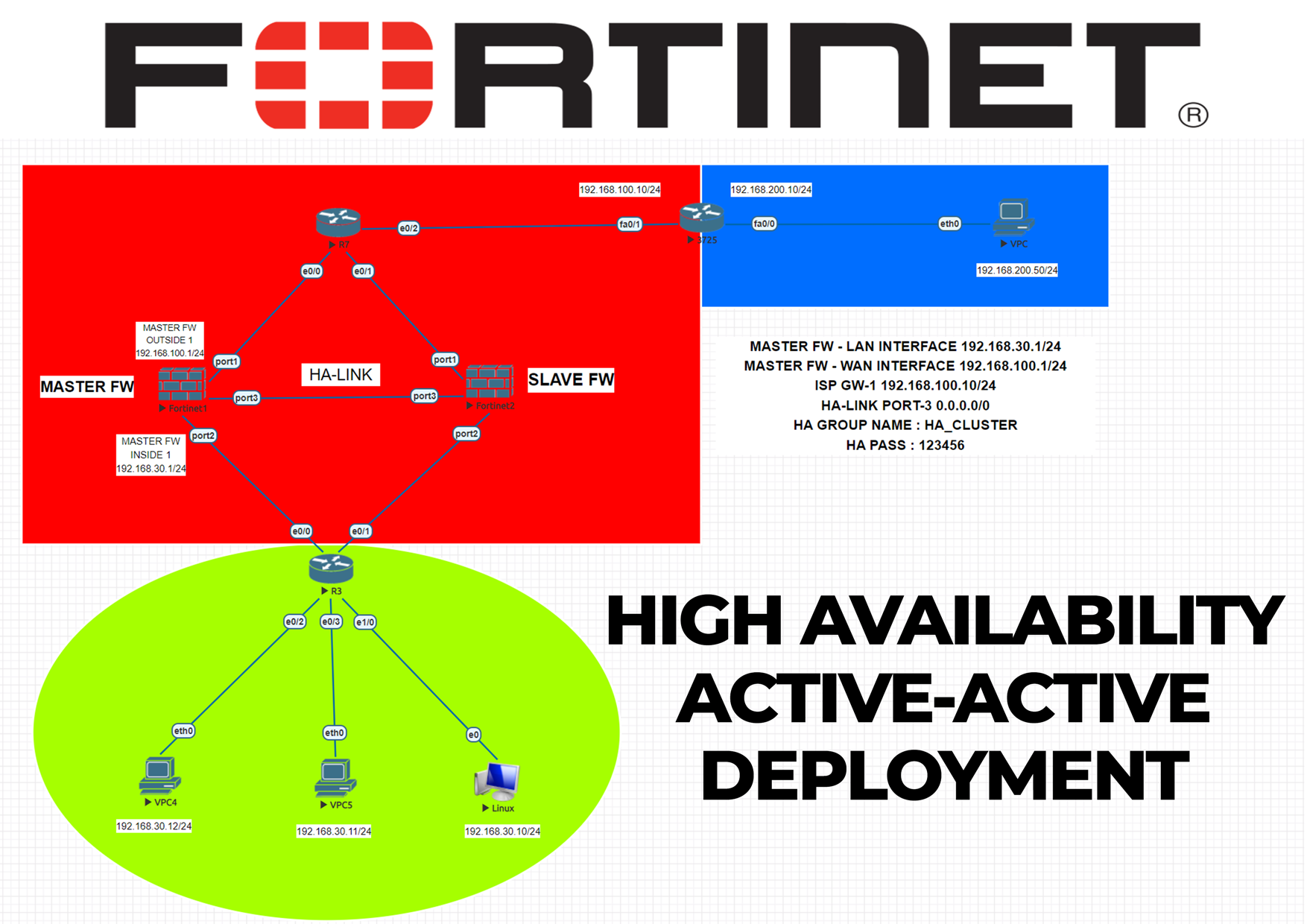
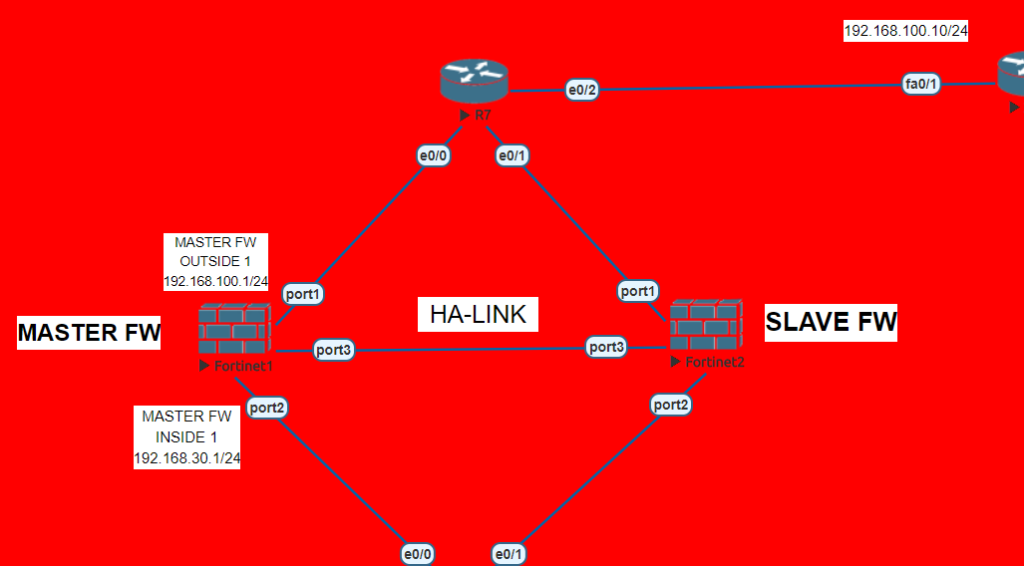
On this topology we have two Fortinet Fortigate firewalls, two network switches, one router, four end-users. We will complete all the physical connections between devices, then jump into Fortigate configurations. We will start configuring Master Firewall with 3 interfaces, LAN-WAN-HA LINK. Second firewall is not needed to be configured as we are going to synchronize settings between firewalls using high availability link. Mode will be “ACTIVE-ACTIVE” and device priority for the master firewall will be “200” so second device will “128” in default. Change firewall hostnames as fortigate1 and fortigate2 for instance. And second firewall’s initial configuration will be through CLI. And then it will automatically synchronize.
HA Configuration Of Master Firewall
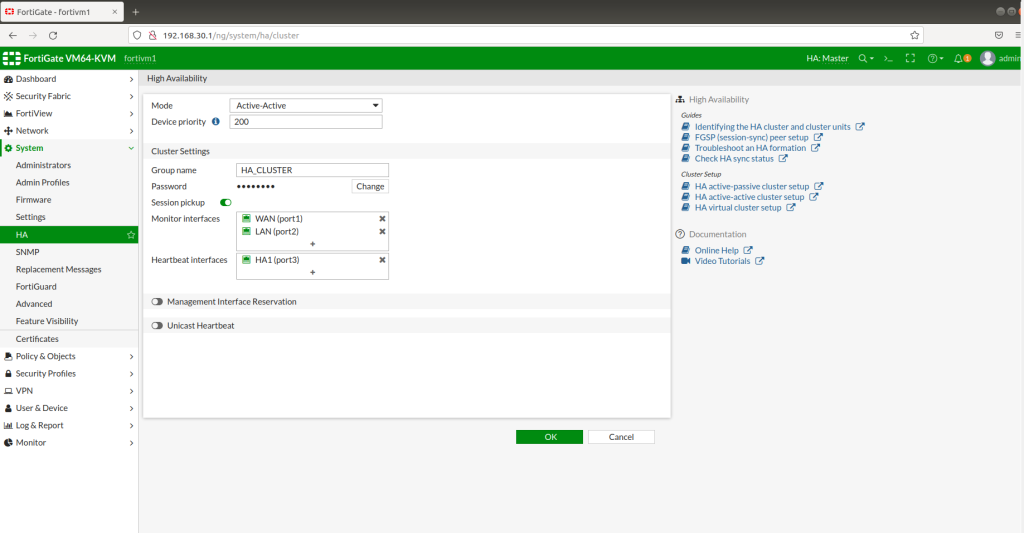
System > HA > Mode : Active-active | Device priority : 200 | Group name : HA_CLUSTER | Password : 123456 | Session pickup : ENABLED | Monitor interfaces : WAN + LAN | Heartbeat interfaces HA1 (port3)
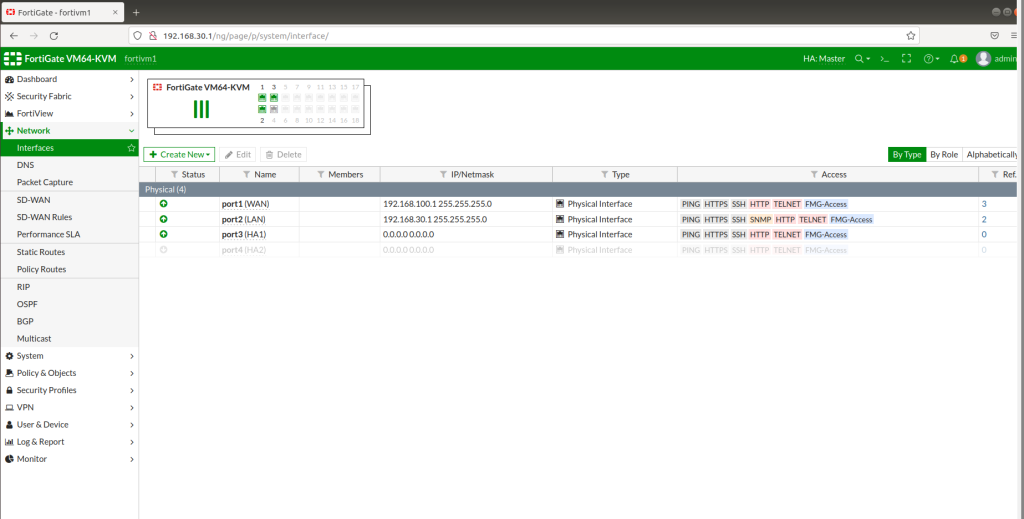
Interfaces
Configuration Of Second Firewall (SLAVE) With CLI
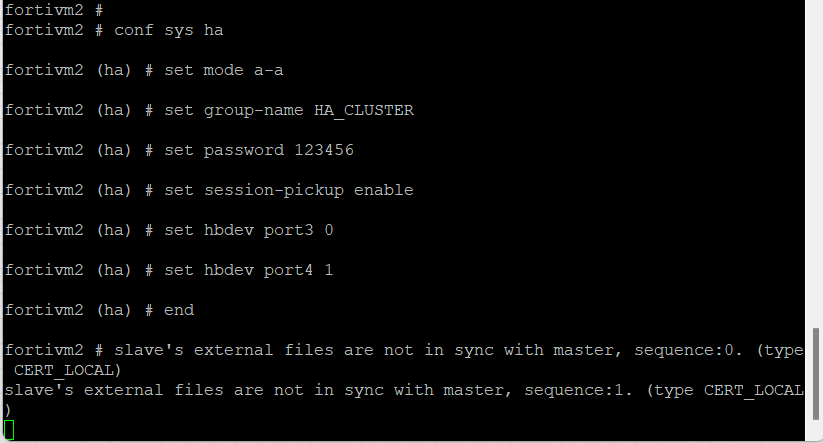
Check HA status on CLI, it will take some time to synchronize both firewalls. Once sync completed you will see green mark on HA status monitor on GUI. And you can test HA configuration via turning off master firewall.
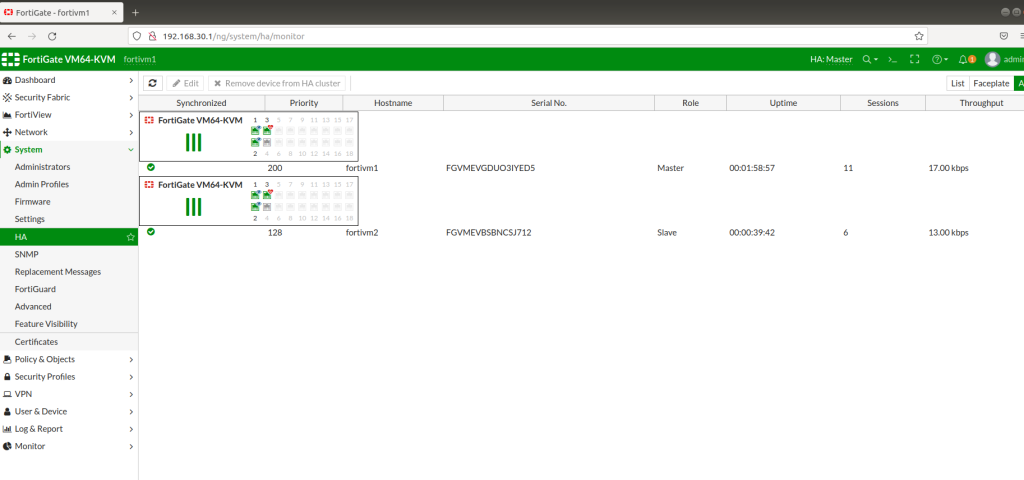
High Availibility has 3 modes: Active-Active , Active-Passive , Standalone mode. On this topology we preferred Active-Active mode. To deploy High Availability successfully, both firewalls should have same version OS and should be even same model. After completion of whole configurations, I strongly suggest you to save all the configurations and reboot all the systems to take effect.
DO NOT USE UNSECURE PASSWORDS ON YOUR REAL ENVIRONMENT. THESE CONFIGURATIONS ARE FOR TRAINING PURPOSES.
Please feel free to contact me regarding your questions.
Happy networking 🙂