Cisco ASA (Adaptive Security Appliance) is a firewall and network security device produced by Cisco Systems. It provides advanced firewall, VPN (Virtual Private Network), and intrusion prevention capabilities to protect networks from unauthorized access, threats, and attacks. The Cisco ASA firewall offers both hardware and software components, including a dedicated security operating system called Cisco ASA Software.
The Cisco ASA firewall offers a range of features that enhance network security and provide robust protection against various threats. Some of the basic features of Cisco ASA firewall are:
- Firewall capabilities: Cisco ASA acts as a stateful firewall, inspecting network traffic at the packet level and making decisions based on configured security policies. It enforces access control rules, allowing or denying traffic based on criteria such as source/destination IP addresses, ports, protocols, and application-layer information.
- VPN (Virtual Private Network): Cisco ASA supports both site-to-site VPN and remote access VPN. It provides secure encrypted connections over public networks, allowing remote users or branch offices to securely access the corporate network.
- Intrusion Prevention System (IPS): Cisco ASA includes an integrated IPS functionality, which inspects traffic for known vulnerabilities, exploits, and malicious activity. It can detect and block various types of attacks, such as intrusion attempts, DoS (Denial of Service) attacks, and malware activity.
- Application Visibility and Control: Cisco ASA offers deep packet inspection (DPI) capabilities, enabling visibility into the applications and protocols used in network traffic. It allows administrators to create granular policies based on application or protocol, enabling fine-grained control over network usage and ensuring compliance.
- Advanced Malware Protection (AMP): Cisco ASA can integrate with Cisco Advanced Malware Protection, which provides additional security against advanced threats. It utilizes advanced techniques such as file reputation analysis, sandboxing, and retrospective security to detect and mitigate malware outbreaks.
- High Availability and Redundancy: Cisco ASA supports various high availability features, such as failover clustering, to ensure continuous operation and minimize downtime. It allows for active-standby or active-active configurations, where multiple ASA devices work together to provide redundancy and seamless failover.
- Identity-based access control: Cisco ASA can integrate with identity management systems such as Active Directory, LDAP, or RADIUS to enforce access policies based on user identities. This allows for more granular control and enables dynamic access decisions based on user roles and attributes.
- IPv6 support: Cisco ASA supports IPv6, enabling the transition to the newer Internet Protocol version and providing security for IPv6 traffic.
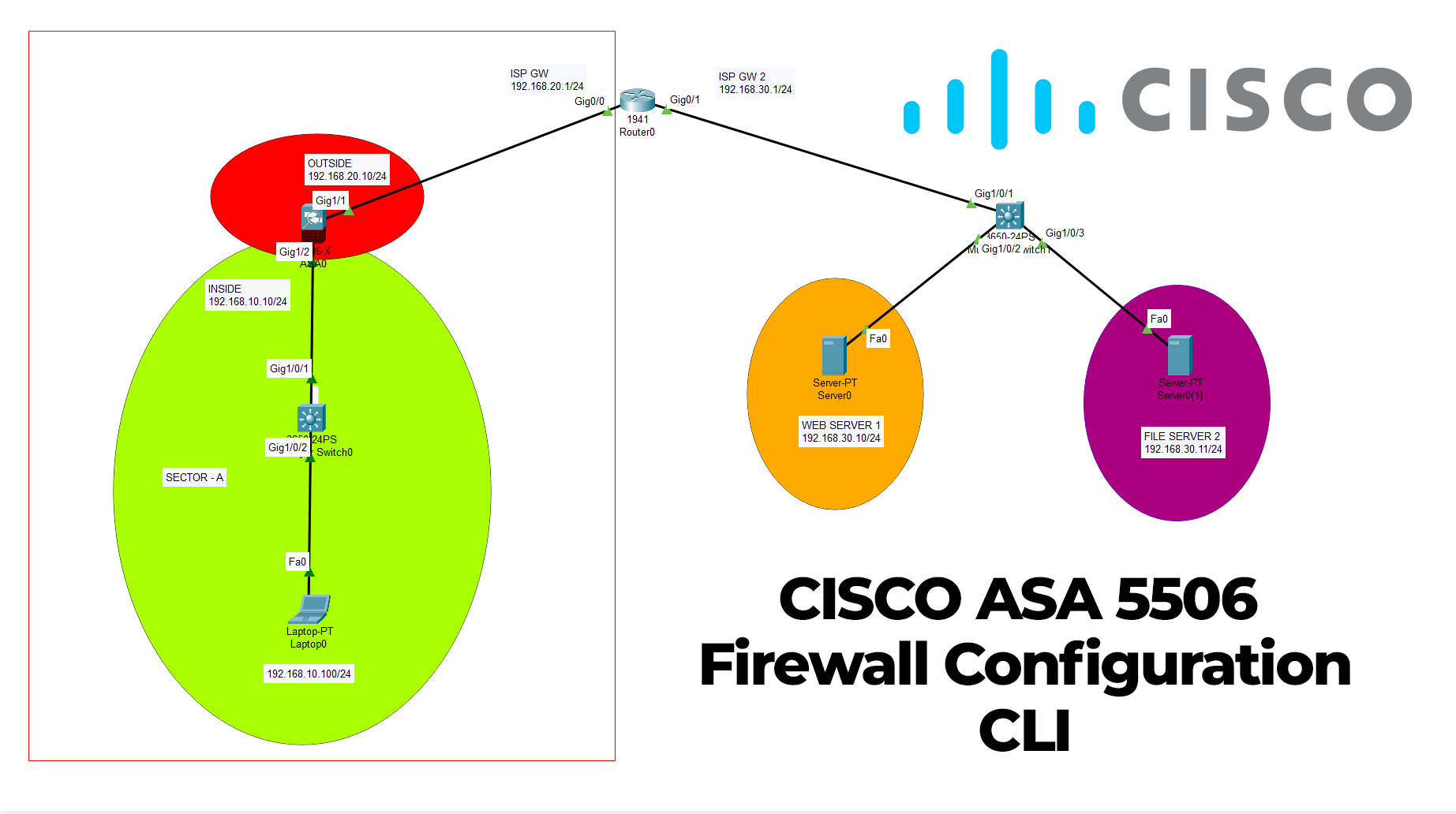
On our topology, we have one Cisco ASA 5506 firewall, two layer-3 Cisco switch, one Cisco router, one IIS server, one file server and one end-user pc. We will start configuring Cisco ASA interfaces at first phase. Then we will proceed with the router and servers etc.
Let’s start to configure Cisco ASA interfaces and related policies using CLI.
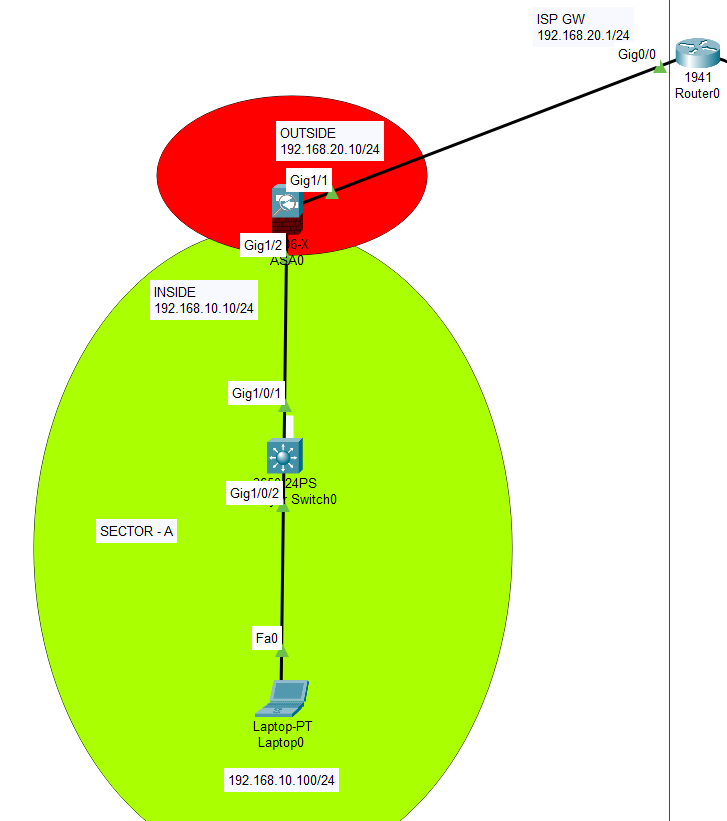
CISCO ASA 5506 Configuration
ciscoasa#configure terminal ciscoasa(config)# ciscoasa(config)#interface g1/1 ciscoasa(config-if)#nameif outside INFO: Security level for "outside" set to 0 by default. ciscoasa(config-if)#ip address 192.168.20.10 255.255.255.0 ciscoasa(config-if)#no shutdown ciscoasa(config-if)#exit ciscoasa(config)#interface g1/2 ciscoasa(config-if)#nameif inside INFO: Security level for "inside" set to 100 by default. ciscoasa(config-if)#ip address 192.168.10.10 255.255.255.0 ciscoasa(config-if)#no shutdown ciscoasa(config-if)#exit ciscoasa(config)#do wr ciscoasa(config)#exit ciscoasa#copy running-config startup-config Source filename [running-config]? Cryptochecksum: 7e953c4e 0e732e44 23853f58 4c074cb2 1161 bytes copied in 1.392 secs (834 bytes/sec) ciscoasa# ciscoasa# ciscoasa#configure terminal ciscoasa(config)#route outside 0.0.0.0 0.0.0.0 192.168.10.1 ciscoasa(config)#object network INSIDE-NET ciscoasa(config-network-object)#subnet 192.168.10.0 255.255.255.0 ciscoasa(config-network-object)#nat (inside,outside) dynamic interface ciscoasa(config-network-object)#exit ciscoasa#configure terminal ciscoasa(config)#class-map inspection_default ciscoasa(config-cmap)#match default-inspection-traffic ciscoasa(config-cmap)#exit ciscoasa(config)# ciscoasa(config)#policy-map global_policy ciscoasa(config-pmap)#class inspection_default ciscoasa(config-pmap-c)#inspect icmp ciscoasa(config-pmap-c)#exit ciscoasa(config)#service-policy global_policy global WARNING: Policy map global_policy is already configured as a service policy ciscoasa(config)#no dhcpd enable inside ciscoasa(config)#no dhcpd enable outside ciscoasa(config)#do wr ciscoasa(config)#policy-map global_policy ciscoasa(config-pmap)#class inspection_default ciscoasa(config-pmap-c)#inspect http ciscoasa(config-pmap-c)#exit ciscoasa(config)#do wr ciscoasa(config)#exit ciscoasa#copy running-config startup-config Source filename [running-config]? Cryptochecksum: 7e953c4e 0e732e44 23853f58 4c074cb2 1333 bytes copied in 1.381 secs (965 bytes/sec) ciscoasa# ciscoasa#configure terminal ciscoasa(config)#hostname CiscoFW CiscoFW(config)#username baris password Cisco123! CiscoFW(config)# CiscoFW(config)# CiscoFW(config)# CiscoFW(config)#service-policy global_policy global WARNING: Policy map global_policy is already configured as a service policy ciscoasa(config)#exit ciscoasa#copy running-config startup-config
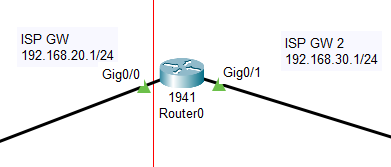
ROUTER Configuration
Router>en Router# Router#configure terminal Router(config)# Router(config)#int g0/0 Router(config-if)#ip address 192.168.20.1 255.255.255.0 Router(config-if)#no shutdown Router(config-if)#exit %LINK-5-CHANGED: Interface GigabitEthernet0/0, changed state to up Router(config)#int g0/1 Router(config-if)#ip address 192.168.30.1 255.255.255.0 Router(config-if)#no shutdown Router(config-if)# %LINK-5-CHANGED: Interface GigabitEthernet0/1, changed state to up %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/1, changed state to up Router(config-if)#exit Router(config)#do wr Building configuration... [OK] Router(config)#ip routing Router(config)#do wr Building configuration... [OK] Router(config)#do copy running-config startup-config Destination filename [startup-config]? Building configuration... [OK] Router(config)#

After completion of firewall devices, we start configuring web servers with related IPV4 and gateway addresses. Once we finish all addressing, give these network devices to send ARP packages each other for a short while. Then all addresses will be reachable from end points.
Test connectivity with a ping test from end-user. Ping Webserver and File server from Enduser laptop.
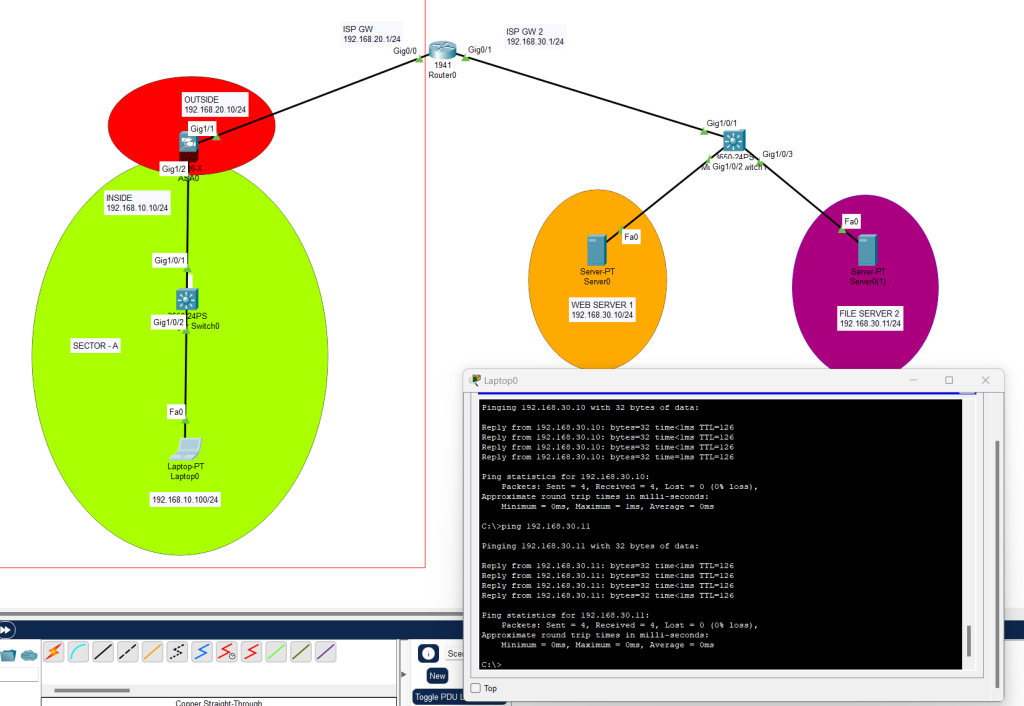
Important turning points on this topology
1-Be careful while configuring Cisco ASA interfaces and interface names. Cisco has default interface names like “inside” , “outside” etc. Once you define these names to interface; security-level can be upgraded to 100 or vice versa to 0. Traffic always tend to flow from secure point (“100”) to low secure point.
2-Be careful with the gateways. Gateways sometime can be tricky. Make sure that you have set correct gateways to all devices.
3-Do not forget to add related policies and NAT settings. Otherwise you cannot ping outside and cannot reach outside IPs.
4-DO NOT GET FRUSTRATED. THINGS ARE WAY MORE EASIER WITH GRAPHICAL USER INTERFACE. GET THINGS DONE WITH CLI THEN YOU CAN JUMP INTO GUI.
Please feel free to contact me for your network related questions.
Happy networking 🙂
You can download this simulation using below link;