[Hacking Series/Lab 5] –How to use CAM table overflow for attack? (MAC flooding)
Disclaimer: These methods and techniques are purely for educational and informational purposes. All attacks were carried out in an offline isolated virtual environment. The use of these techniques in normal life is illegal and the responsibility lies strictly with the reader. DO NOT USE THESE TECHNIQUES IN REAL LIFE ! A CAM table attack, also […]
[Hacking Series/Lab 4] –How to launch MAN IN THE MIDDLE Attack? (ARP poisoning)
Disclaimer: These methods and techniques are purely for educational and informational purposes. All attacks were carried out in an offline isolated virtual environment. The use of these techniques in normal life is illegal and the responsibility lies strictly with the reader. DO NOT USE THESE TECHNIQUES IN REAL LIFE ! ARP poisoning and Man-in-the-Middle (MITM) […]
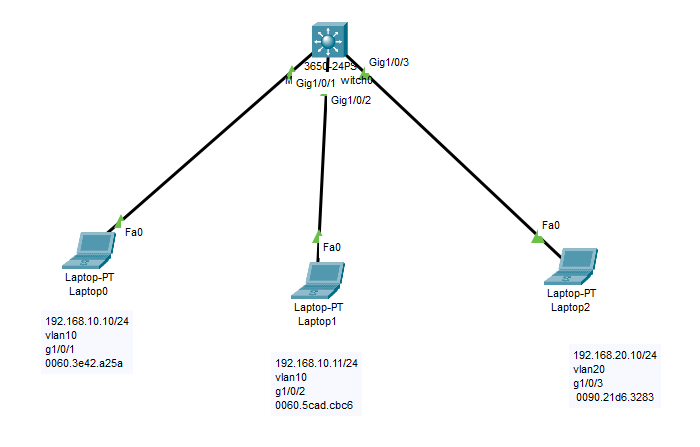
[Hacking Series/Lab 1] – VLAN Hopping Attack ! This training was created for preventive defensive purposes.
Disclaimer: These methods and techniques are purely for educational and informational purposes. All attacks were carried out in an offline isolated virtual environment. The use of these techniques in normal life is illegal and the responsibility lies strictly with the reader. DO NOT USE THESE TECHNIQUES IN REAL LIFE ! In this training, I will […]
Ethernet MAC Port-security
Today we will implement port security on our Cisco switch. We will bind the MAC address of the NIC device with our related port. So if some changes happen on the physical ports, then new device will be restricted. CISCO SWITCH MAIN CONFIGURATION Switch>enable Switch#configure terminal Enter configuration commands, one per line. End with CNTL/Z. […]
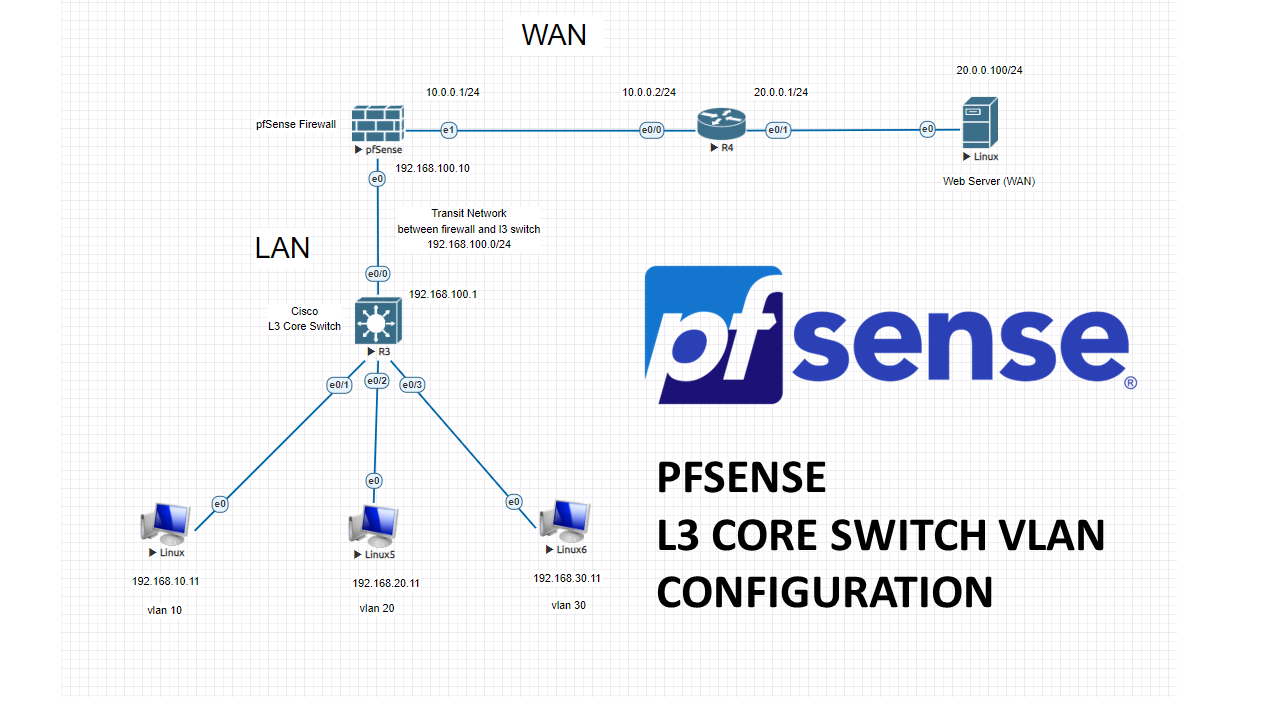
PfSense firewall + L3 Core switch configuration with VLANs
In this lab, we will create 3 vlans and connect our core switch to pfSense firewall with a transit network. Then we will configure our firewall with these vlan subnets. LAN related traffic will not hit the firewall, because SVIs (VLANgateways) will be created on L3 Core switch. All the necessary permissions between vlans will […]
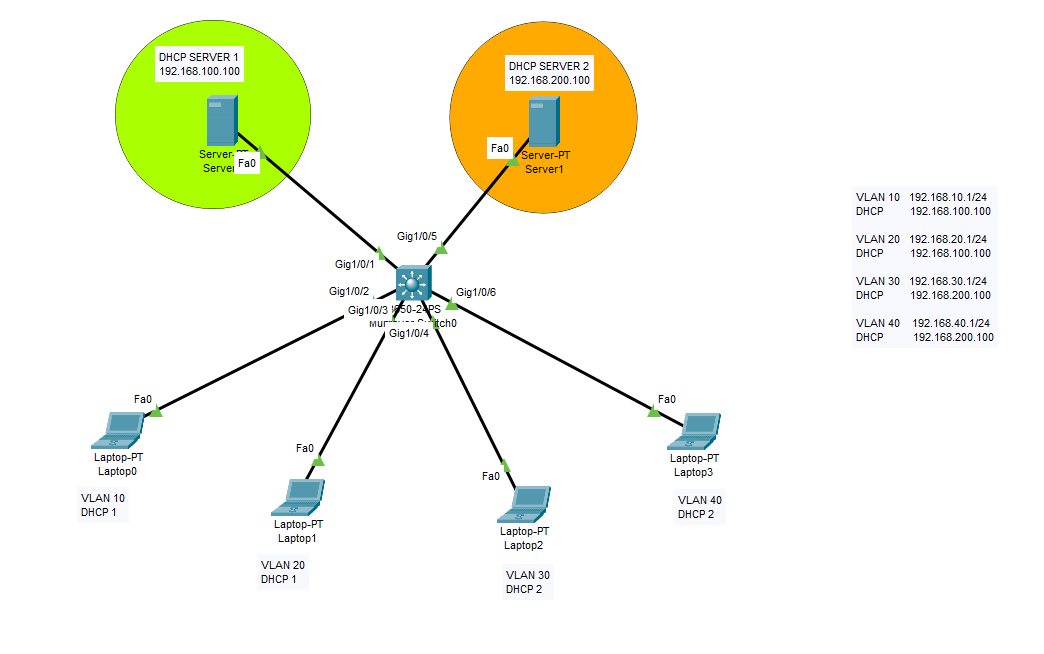
Multiple DHCP Server Configurations For VLANs
On this practice lab, we will configure two DHCP servers for 4 different VLANs. We will create the VLANs on the core switch, then we will assign the DHCP servers to VLANs with the command of “ip helper-address“. By this method, you will be able to use different DHCP servers for different purposes. Cisco Core […]
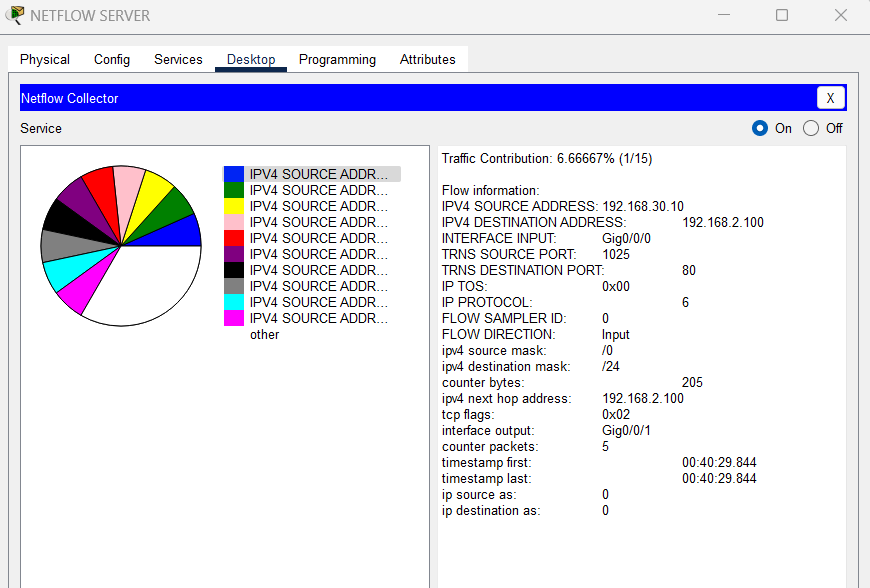
What is Netflow protocol? Deployment of Netflow server
NetFlow is a network protocol developed by Cisco that is used for network traffic monitoring and analysis. It allows network administrators to collect and view information about the traffic flowing through their network devices, such as routers and switches. A NetFlow server, sometimes referred to as a NetFlow collector or analyzer, is a system or […]
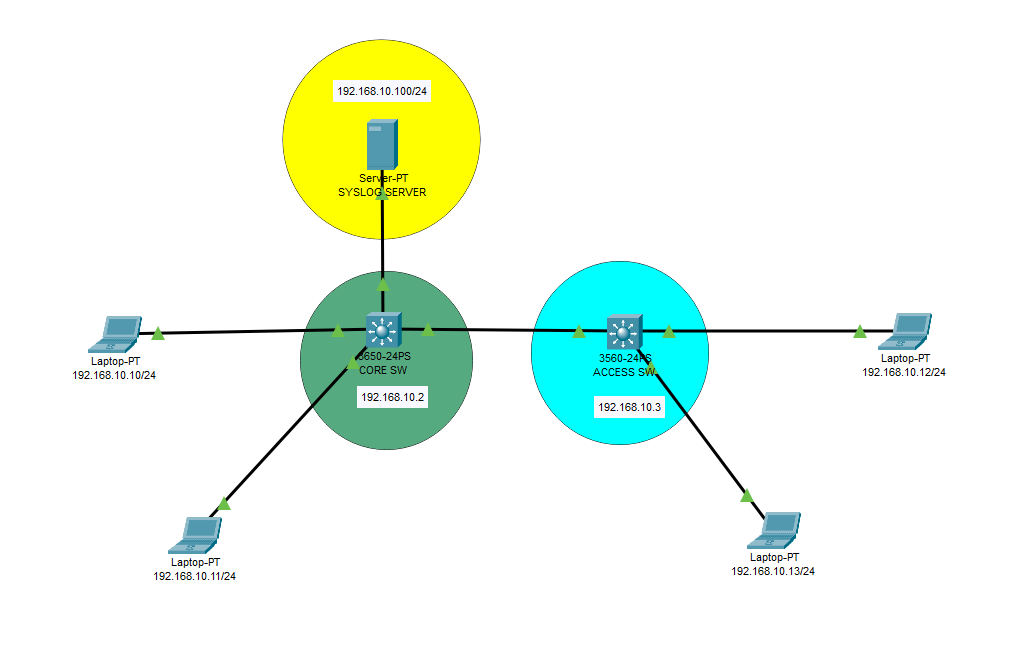
Syslog Server implementation for Cisco network devices
On Cisco networking devices, a syslog server refers to a system or application that collects, stores, and manages log messages generated by the Cisco devices. These log messages contain valuable information about the operation, performance, and events occurring on the network equipment. The syslog server helps network administrators and engineers to monitor, troubleshoot, and analyze […]
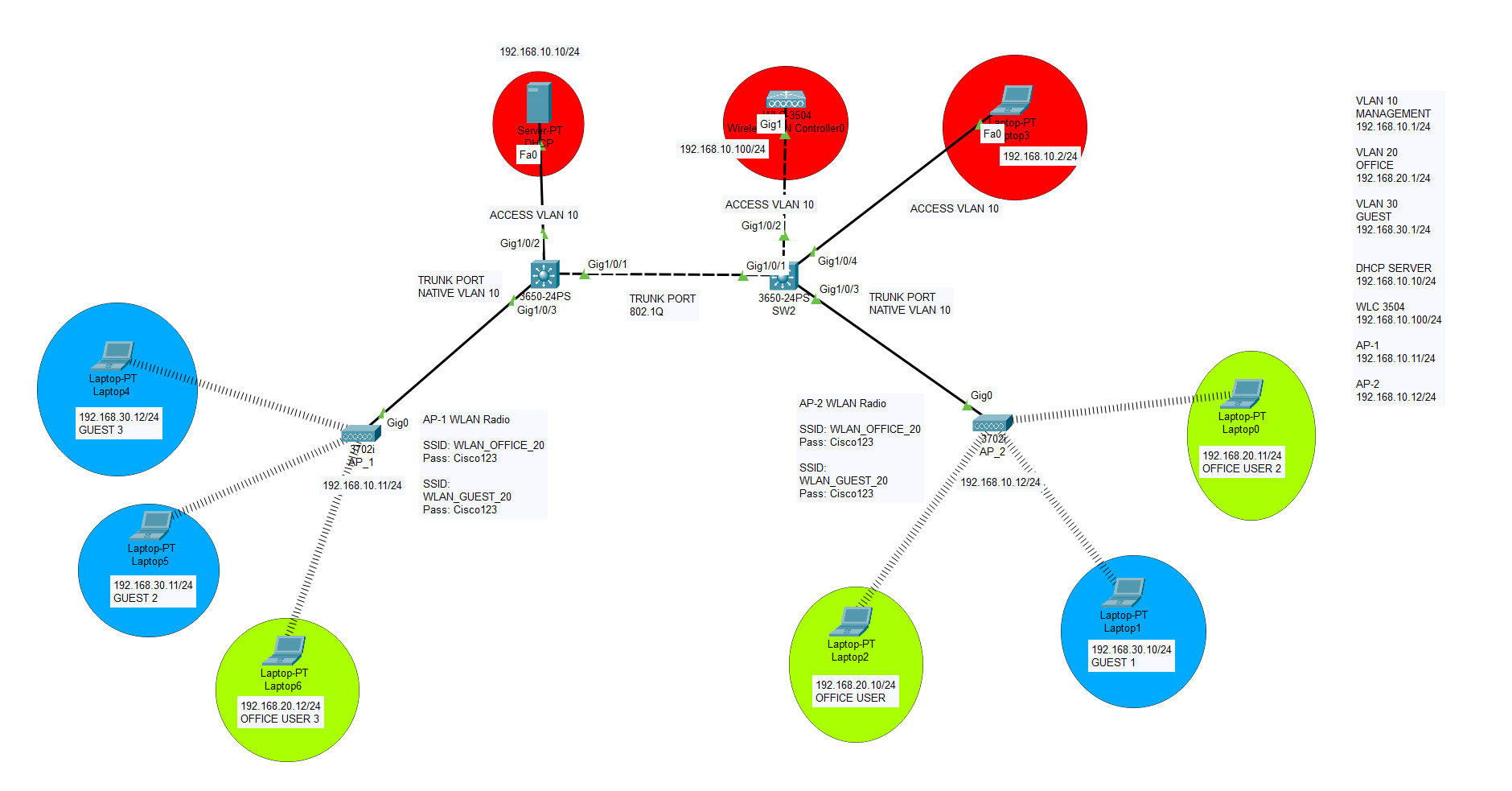
Cisco WLAN Controller with VLANs through multiple SSIDs
Let’s start configuring our VLANs and ports. We will create 3 VLANs on SW1 core switch. One of them will serve as Management subnet, others will serve as Office and Guest networks. Upon completion of VLAN and port configurations, we will start configuring Cisco Wireless Controllers and our Cisco Access Points. Both access points will […]
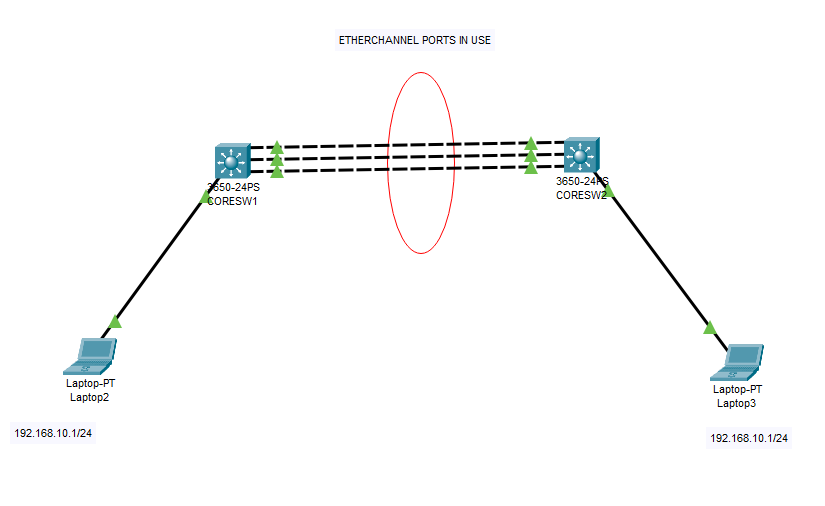
What is Etherchannel ? How to use it?
EtherChannel is a technology used in networking to create a logical link aggregation or link bundling of multiple physical Ethernet links into a single logical link, providing increased bandwidth, improved redundancy, and load balancing across the bundled links. It is also known as Link Aggregation, Port Channel, or Port Aggregation. EtherChannel is typically used in […]
![[Hacking Series/Lab 5] –How to use CAM table overflow for attack? (MAC flooding)](https://barisyuksel.com.tr/wp-content/uploads/2024/08/macof_general1-966x653.png)
![[Hacking Series/Lab 4] –How to launch MAN IN THE MIDDLE Attack? (ARP poisoning)](https://barisyuksel.com.tr/wp-content/uploads/2024/08/mitm_diagram_topology-1035x653.png)
![[Hacking Series/Lab 1] – VLAN Hopping Attack ! This training was created for preventive defensive purposes.](https://barisyuksel.com.tr/wp-content/uploads/2024/07/vlan-hopping-diagram2.png)