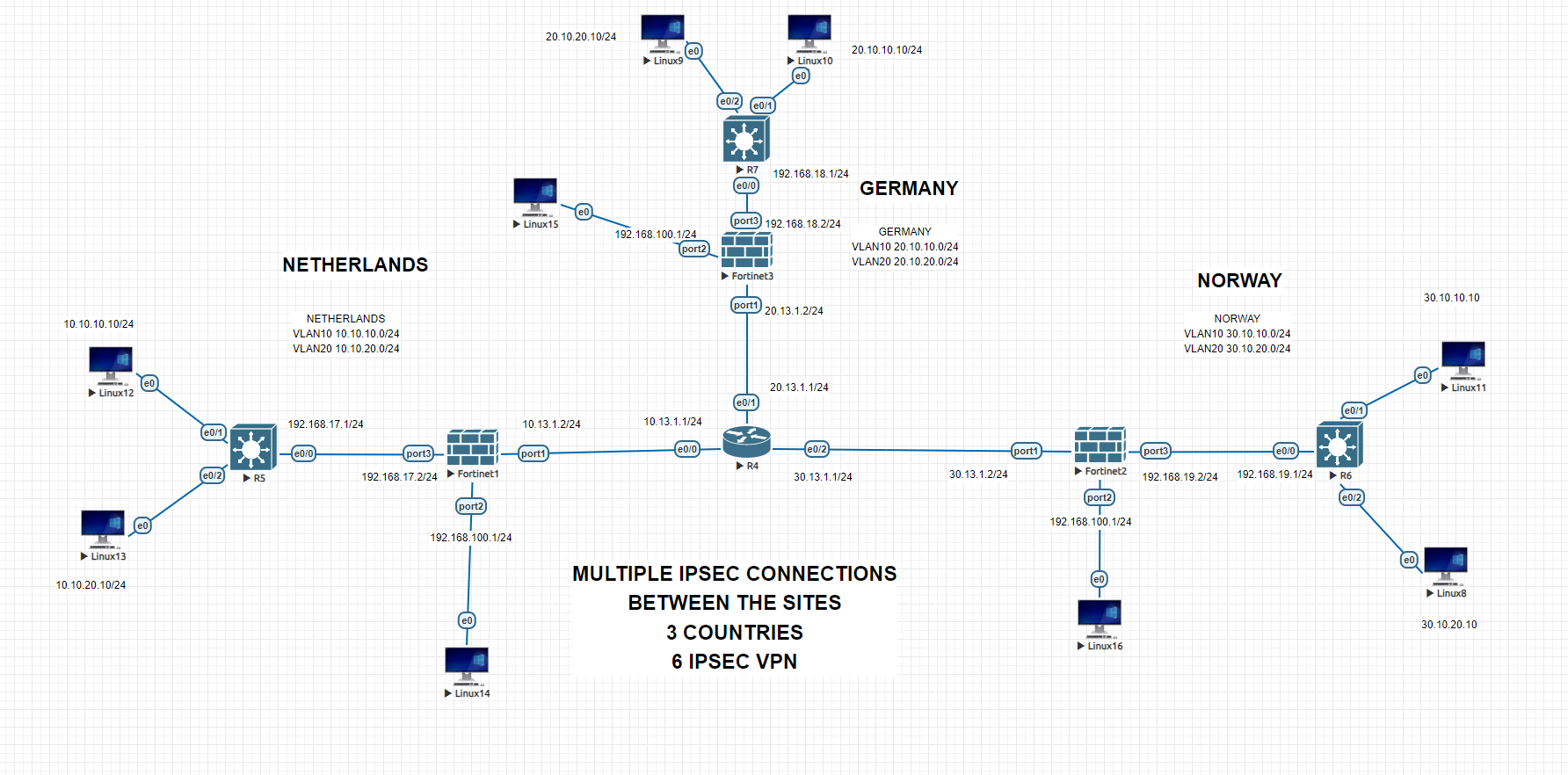
IPsec, short for Internet Protocol Security, is a suite of protocols used to ensure secure communication over IP networks. It provides security services at the IP layer by enabling encryption, authentication, and integrity checking of IP packets. IPsec can be used to establish secure VPN (Virtual Private Network) connections between remote networks or individual devices, as well as to secure communication between hosts within a single network.
IPsec operates in two main modes:
- Transport mode: In this mode, only the payload (data) of the IP packet is encrypted and authenticated. The original IP header remains intact, making it suitable for securing communication between individual hosts.
- Tunnel mode: In this mode, the entire IP packet, including the original IP header, is encrypted and authenticated. This mode is typically used to establish secure communication between networks or to create VPN tunnels.
IPsec relies on cryptographic algorithms to provide security services such as encryption (to ensure confidentiality), authentication (to verify the identity of communicating parties), and integrity checking (to detect any tampering with the data). Common cryptographic algorithms used in IPsec include AES (Advanced Encryption Standard) for encryption, HMAC (Hash-based Message Authentication Code) for authentication, and SHA (Secure Hash Algorithm) for integrity checking.
What we are going to do on this lab;
1- We will calculate and plan all the necessary IPs for this lab
2-We will configure the core switches with VLANs.
3-We will do the initial configuration on Fortigate to start.
4-Afterwards, we will do essential configuration on Fortigates to connect subnets to internet
5-With IPSEC wizard, we will create the encrypted IPSEC tunnels between all the sites.
6-We will check the connection between the sites.
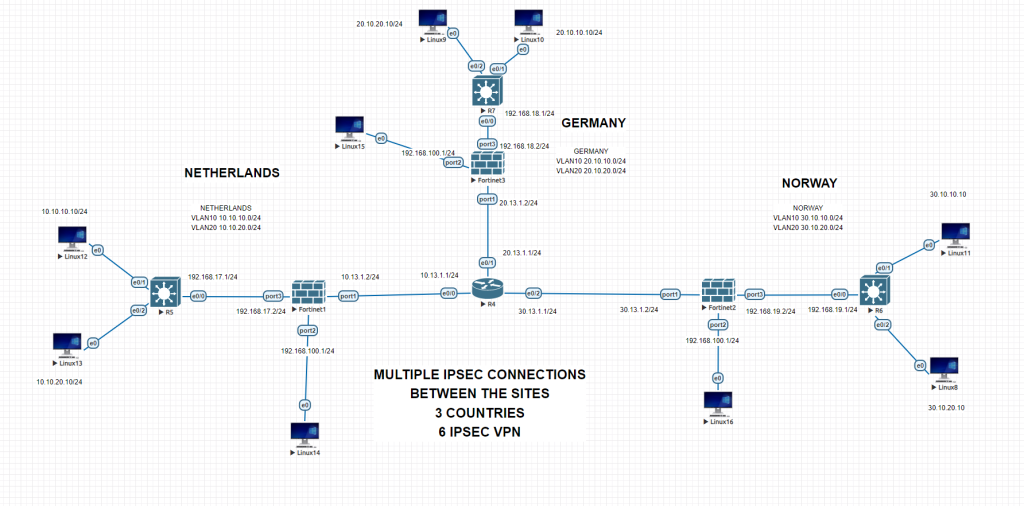
NETHERLANDS CORE SWITCH CONFIGURATIONS
Switch>enable
Switch#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#hostname SW-NETHERLANDS
SW-NETHERLANDS(config)#vlan 10
SW-NETHERLANDS(config-vlan)#vlan 20
SW-NETHERLANDS(config-vlan)#exit
SW-NETHERLANDS(config)#int vlan 10
SW-NETHERLANDS(config-if)#
SW-NETHERLANDS(config-if)#ip address 10.10.10.1 255.255.255.0
SW-NETHERLANDS(config-if)#no shutdown
SW-NETHERLANDS(config-if)#exit
SW-NETHERLANDS(config)#interface vlan 2
*Feb 25 15:19:22.066: %LINK-3-UPDOWN: Interface Vlan10, changed state to down
SW-NETHERLANDS(config)#interface vlan 20
SW-NETHERLANDS(config-if)#ip address 10.10.20.1 255.255.255.0
SW-NETHERLANDS(config-if)#no shutdown
SW-NETHERLANDS(config-if)#
*Feb 25 15:19:41.789: %LINK-3-UPDOWN: Interface Vlan20, changed state to down
SW-NETHERLANDS(config-if)#exit
SW-NETHERLANDS(config)#int e0/0
SW-NETHERLANDS(config-if)#no switchport
SW-NETHERLANDS(config-if)#ip address 192.168.17.1 255.255.255.0
SW-NETHERLANDS(config-if)#no shutdown
SW-NETHERLANDS(config-if)#exit
SW-NETHERLANDS(config)#ip routing
SW-NETHERLANDS(config)#do copy run start
Destination filename [startup-config]?
Building configuration...
Compressed configuration from 848 bytes to 573 bytes[OK]
SW-NETHERLANDS(config)#interface e0/1
SW-NETHERLANDS(config-if)#switchport mode access
SW-NETHERLANDS(config-if)#switchport access vlan 10
SW-NETHERLANDS(config-if)#no shutdown
SW-NETHERLANDS(config-if)#exit
SW-NETHERLANDS(config)#interface e0/2
SW-NETHERLANDS(config-if)#switchport mode access
SW-NETHERLANDS(config-if)#switchport access vlan 20
SW-NETHERLANDS(config-if)#no shutdown
SW-NETHERLANDS(config-if)#exit
SW-NETHERLANDS(config)#do copy run start
Destination filename [startup-config]?
Building configuration...
Compressed configuration from 950 bytes to 623 bytes[OK]
SW-NETHERLANDS(config)#
*Feb 25 15:21:45.104: %LINK-3-UPDOWN: Interface Vlan10, changed state to up
*Feb 25 15:21:46.112: %LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan10, changed state to up
SW-NETHERLANDS(config)#
*Feb 25 15:22:09.071: %LINK-3-UPDOWN: Interface Vlan20, changed state to up
*Feb 25 15:22:10.075: %LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan20, changed state to up
SW-NETHERLANDS(config)#do copy run start
Destination filename [startup-config]?
Building configuration...
Compressed configuration from 950 bytes to 623 bytes[OK]
SW-NETHERLANDS(config)#ip route 0.0.0.0 0.0.0.0 192.168.17.2
SW-NETHERLANDS(config)#do copy run start
Destination filename [startup-config]?
Building configuration...
Compressed configuration from 988 bytes to 641 bytes[OK]
SW-NETHERLANDS(config)#
GERMANY CORE SWITCH CONFIGURATIONS
Switch>enable
Switch#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#hostname SW-GERMANY
SW-GERMANY(config)#vlan 10
SW-GERMANY(config-vlan)#vlan 20
SW-GERMANY(config-vlan)#exit
SW-GERMANY(config)#int vlan 10
SW-GERMANY(config-if)#ip address
*Feb 25 15:25:25.509: %LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan10, changed state to down
SW-GERMANY(config-if)#ip address 20.10.10.1 255.255.255.0
SW-GERMANY(config-if)#no shutdown
SW-GERMANY(config-if)#exit
SW-GERMANY(config)#int vlan 2
*Feb 25 15:25:38.377: %LINK-3-UPDOWN: Interface Vlan10, changed state to down
SW-GERMANY(config)#int vlan 20
SW-GERMANY(config-if)#ip address
*Feb 25 15:25:41.940: %LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan20, changed state to down
SW-GERMANY(config-if)#ip address 20.10.20.1 255.255.255.0
SW-GERMANY(config-if)#no shutdown
SW-GERMANY(config-if)#exit
SW-GERMANY(config)#
*Feb 25 15:26:21.337: %LINK-3-UPDOWN: Interface Vlan20, changed state to down
SW-GERMANY(config)#int e0/0
SW-GERMANY(config-if)#no switchport
SW-GERMANY(config-if)#ip address
*Feb 25 15:26:38.772: %LINK-3-UPDOWN: Interface Ethernet0/0, changed state to up
*Feb 25 15:26:39.772: %LINEPROTO-5-UPDOWN: Line protocol on Interface Ethernet0/0, changed state to up
SW-GERMANY(config-if)#ip address 192.168.18.1 255.255.255.0
SW-GERMANY(config-if)#no shutdown
SW-GERMANY(config-if)#exit
SW-GERMANY(config)#interface e0/1
SW-GERMANY(config-if)#switchport mode access
SW-GERMANY(config-if)#switchport access vlan 10
SW-GERMANY(config-if)#no shutdown
SW-GERMANY(config-if)#exit
SW-GERMANY(config)#interface e0/2
SW-GERMANY(config-if)#switchport mode access
SW-GERMANY(config-if)#switchport access vlan 20
SW-GERMANY(config-if)#no shutdown
SW-GERMANY(config-if)#exit
SW-GERMANY(config)#ip routing
SW-GERMANY(config)#ip route 0.0.0.0 0.0.0.0 192.168.18.2
SW-GERMANY(config)#no shutdown
SW-GERMANY(config)#
*Feb 25 15:27:37.341: %LINK-3-UPDOWN: Interface Vlan10, changed state to up
*Feb 25 15:27:38.341: %LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan10, changed state to up
SW-GERMANY(config)#do copy run start
Destination filename [startup-config]?
Building configuration...
Compressed configuration from 984 bytes to 638 bytes[OK]
SW-GERMANY(config)#
NORWAY CORE SWITCH CONFIGURATIONS
Switch>enable
Switch#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#hostname SW-NORWAY
SW-NORWAY(config)#vlan 10
SW-NORWAY(config-vlan)#vlan 20
SW-NORWAY(config-vlan)#exit
SW-NORWAY(config)#int vlan 10
SW-NORWAY(config-if)#ip address 30.10.10.1 255.255.255.0
SW-NORWAY(config-if)#no shutdown
SW-NORWAY(config-if)#exit ^
SW-NORWAY(config)#interface vlan 20
SW-NORWAY(config-if)#ip address
*Feb 25 15:30:29.005: %LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan20, changed state to down
SW-NORWAY(config-if)#ip address 30.10.20.1 255.255.255.0
SW-NORWAY(config-if)#no shutdown
SW-NORWAY(config-if)#exit
SW-NORWAY(config)#
*Feb 25 15:30:40.221: %LINK-3-UPDOWN: Interface Vlan20, changed state to down
SW-NORWAY(config)#interface e0/0
SW-NORWAY(config-if)#no switchport
SW-NORWAY(config-if)#ip address
*Feb 25 15:33:01.112: %LINK-3-UPDOWN: Interface Ethernet0/0, changed state to up
*Feb 25 15:33:02.116: %LINEPROTO-5-UPDOWN: Line protocol on Interface Ethernet0/0, changed state to up
SW-NORWAY(config-if)#ip address 192.168.19.1 255.255.255.0
SW-NORWAY(config-if)#no shutdown
SW-NORWAY(config-if)#exit
SW-NORWAY(config)#ip routing
SW-NORWAY(config)#ip route 0.0.0.0 0.0.0.0 192.168.19.2
SW-NORWAY(config)#interface e0/1
SW-NORWAY(config-if)#switchport mode access
SW-NORWAY(config-if)#switchport access vlan 10
SW-NORWAY(config-if)#no shutdown
SW-NORWAY(config-if)#exit
SW-NORWAY(config)#interface e0/2
SW-NORWAY(config-if)#switchport mode access
SW-NORWAY(config-if)#switchport access vlan 20
SW-NORWAY(config-if)#no shutdown
SW-NORWAY(config-if)#exit
SW-NORWAY(config)#do copy run start
Destination filename [startup-config]?
Building configuration...
Compressed configuration from 983 bytes to 638 bytes[OK]
SW-NORWAY(config)#
*Feb 25 15:34:08.625: %LINK-3-UPDOWN: Interface Vlan10, changed state to up
*Feb 25 15:34:09.625: %LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan10, changed state to up
SW-NORWAY(config)#
NETHERLANDS FIREWALL INITAL CLI CONFIGURATION
FortiGate-VM64-KVM login: admin
Password:
You are forced to change your password, please input a new password.
New Password:*****
Confirm Password:*****
Welcome !
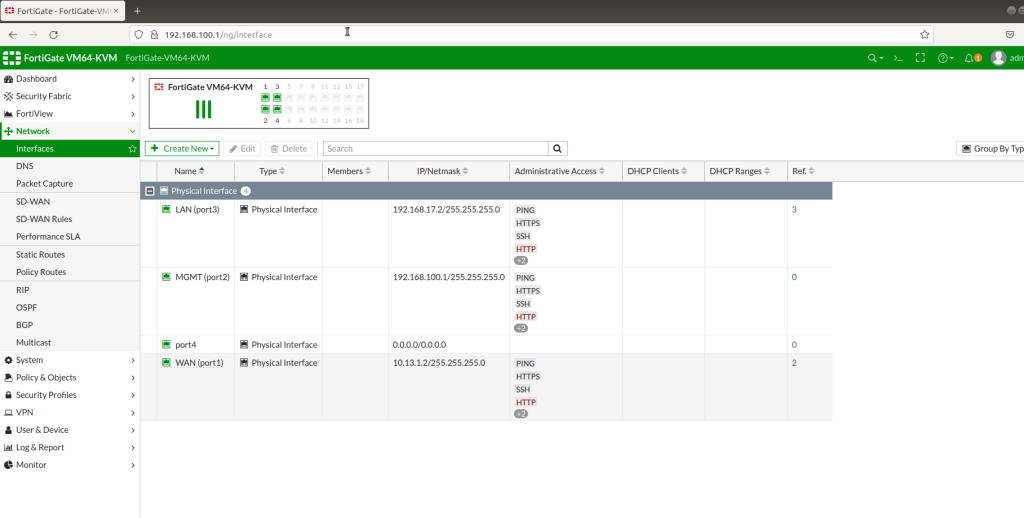
FortiGate-VM64-KVM # config system interface
FortiGate-VM64-KVM (interface) # edit port1
FortiGate-VM64-KVM (port1) # set alias WAN
FortiGate-VM64-KVM (port1) # set role wan
FortiGate-VM64-KVM (port1) # set mode static
FortiGate-VM64-KVM (port1) # set ip 10.13.1.2 255.255.255.0
FortiGate-VM64-KVM (port1) # set allowaccess ssh ping http https telnet fgfm
FortiGate-VM64-KVM (port1) # next
FortiGate-VM64-KVM (interface) # edit port2
FortiGate-VM64-KVM (port2) # set alias MGMT
FortiGate-VM64-KVM (port2) # set role lan
FortiGate-VM64-KVM (port2) # set mode static
FortiGate-VM64-KVM (port2) # set ip 192.168.100.1 255.255.255.0
FortiGate-VM64-KVM (port2) # set allowaccess ssh ping telnet http https fgfm
FortiGate-VM64-KVM (port2) # next
FortiGate-VM64-KVM (interface) # edit port3
FortiGate-VM64-KVM (port3) # set alias LAN
FortiGate-VM64-KVM (port3) # set role lan
FortiGate-VM64-KVM (port3) # set mode static
FortiGate-VM64-KVM (port3) # set ip 192.168.17.2 255.255.255.0
FortiGate-VM64-KVM (port3) # set allowaccess ssh ping telnet http https fgfm
FortiGate-VM64-KVM (port3) # end
FortiGate-VM64-KVM #
GERMANY FIREWALL INITIAL CLI CONFIGURATION
FortiGate-VM64-KVM login: admin
Password:
You are forced to change your password, please input a new password.
New Password:*****
Confirm Password:*****
Welcome !
FortiGate-VM64-KVM # config system interface
FortiGate-VM64-KVM (interface) # edit port1
FortiGate-VM64-KVM (port1) # set alias WAN
FortiGate-VM64-KVM (port1) # set mode static
FortiGate-VM64-KVM (port1) # set role wan
FortiGate-VM64-KVM (port1) # set ip 20.13.1.2 255.255.255.0
FortiGate-VM64-KVM (port1) # set allowaccess ping ssh telnet http https fgfm
FortiGate-VM64-KVM (port1) # next
FortiGate-VM64-KVM (interface) # edit port2
FortiGate-VM64-KVM (port2) # set alias MGMT
FortiGate-VM64-KVM (port2) # set role lan
FortiGate-VM64-KVM (port2) # set mode static
FortiGate-VM64-KVM (port2) # set ip 192.168.100.1 255.255.255.0
FortiGate-VM64-KVM (port2) # set allowaccess http https ping ssh telnet fgfm
FortiGate-VM64-KVM (port2) # next
FortiGate-VM64-KVM (interface) # edit port3
FortiGate-VM64-KVM (port3) # set alias LAN
FortiGate-VM64-KVM (port3) # set role lan
FortiGate-VM64-KVM (port3) # set mode static
FortiGate-VM64-KVM (port3) # set ip 192.168.18.2 255.255.255.0
FortiGate-VM64-KVM (port3) # set allowaccess ssh ping telnet http https fgfm
FortiGate-VM64-KVM (port3) # end
FortiGate-VM64-KVM #
NORWAY FIREWALL INITIAL CLI CONFIGURATION
FortiGate-VM64-KVM login: admin
Password:
You are forced to change your password, please input a new password.
New Password:*****
Confirm Password:*****
Welcome !
FortiGate-VM64-KVM # config system interface
FortiGate-VM64-KVM (interface) # edit port1
FortiGate-VM64-KVM (port1) # set alias wan
FortiGate-VM64-KVM (port1) # set role wan
FortiGate-VM64-KVM (port1) # set mode static
FortiGate-VM64-KVM (port1) # set ip 30.13.1.2 255.255.255.0
FortiGate-VM64-KVM (port1) # set allowaccess ssh ping telnet fgfm http https
FortiGate-VM64-KVM (port1) # next
FortiGate-VM64-KVM (interface) # edit port2
FortiGate-VM64-KVM (port2) # set alias MGMT
FortiGate-VM64-KVM (port2) # set role lan
FortiGate-VM64-KVM (port2) # set mode static
FortiGate-VM64-KVM (port2) # set ip 192.168.100.1 255.255.255.0
FortiGate-VM64-KVM (port2) # set allowaccess ssh ping telnet fgfm http https
FortiGate-VM64-KVM (port2) # next
FortiGate-VM64-KVM (interface) # edit port3
FortiGate-VM64-KVM (port3) # set alias LAN
FortiGate-VM64-KVM (port3) # set role lan
FortiGate-VM64-KVM (port3) # set mode static
FortiGate-VM64-KVM (port3) # set ip 192.168.19.2 255.255.255.0
FortiGate-VM64-KVM (port3) # set allowaccess ssh ping telnet fgfm http https
FortiGate-VM64-KVM (port3) # end
FortiGate-VM64-KVM #
ISP ROUTER CONFIGURATION
% Please answer 'yes' or 'no'.
Would you like to enter the initial configuration dialog? [yes/no]: no
Press RETURN to get started!
*Feb 25 15:16:02.851: %CTS-6-ENV_DATA_START_STATE: Environment Data Download in start state
*Feb 25 15:16:04.734: %LINEPROTO-5-UPDOWN: Line protocol on Interface VoIP-Null0, changed state to up
*Feb 25 15:16:04.807: %LINK-3-UPDOWN: Interface Ethernet0/0, changed state to up
*Feb 25 15:16:04.812: %LINK-3-UPDOWN: Interface Ethernet0/1, changed state to up
*Feb 25 15:16:04.826: %LINK-3-UPDOWN: Interface Ethernet0/2, changed state to up
*Feb 25 15:16:04.839: %LINK-3-UPDOWN: Interface Ethernet0/3, changed state to up
*Feb 25 15:16:05.813: %LINEPROTO-5-UPDOWN: Line protocol on Interface Ethernet0/0, changed state to up
*Feb 25 15:16:05.813: %LINEPROTO-5-UPDOWN: Line protocol on Interface Ethernet0/1, changed state to up
*Feb 25 15:16:05.826: %LINEPROTO-5-UPDOWN: Line protocol on Interface Ethernet0/2, changed state to up
*Feb 25 15:16:05.842: %LINEPROTO-5-UPDOWN: Line protocol on Interface Ethernet0/3, changed state to up
*Feb 25 15:44:50.448: %LINK-5-CHANGED: Interface Ethernet0/0, changed state to administratively down
*Feb 25 15:44:50.448: %LINK-5-CHANGED: Interface Ethernet0/1, changed state to administratively down
*Feb 25 15:44:50.448: %LINK-5-CHANGED: Interface Ethernet0/2, changed state to administratively down
*Feb 25 15:44:50.457: %LINK-5-CHANGED: Interface Ethernet0/3, changed state to administratively down
*Feb 25 15:44:51.096: %SYS-5-RESTART: System restarted --
Cisco IOS Software, Linux Software (I86BI_LINUX-ADVENTERPRISEK9-M), Version 15.5(2)T, DEVELOPMENT TEST SOFTWARE
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2015 by Cisco Systems, Inc.
Compiled Thu 26-Mar-15 07:36 by prod_rel_team
*Feb 25 15:44:51.107: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is OFF
*Feb 25 15:44:51.107: %CRYPTO-6-GDOI_ON_OFF: GDOI is OFF
*Feb 25 15:44:51.339: %IP-5-WEBINST_KILL: Terminating DNS process
*Feb 25 15:44:51.448: %LINEPROTO-5-UPDOWN: Line protocol on Interface Ethernet0/0, changed state to down
*Feb 25 15:44:51.449: %LINEPROTO-5-UPDOWN: Line protocol on Interface Ethernet0/1, changed state to down
*Feb 25 15:44:51.449: %LINEPROTO-5-UPDOWN: Line protocol on Interface Ethernet0/2, changed state to down
*Feb 25 15:44:51.457: %LINEPROTO-5-UPDOWN: Line protocol on Interface Ethernet0/3, changed state to down
Router>en
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#hostname ISP-ROUTER
ISP-ROUTER(config)#int e0/0
ISP-ROUTER(config-if)#ip address 10.13.1.1 255.255.255.0
ISP-ROUTER(config-if)#no sh
ISP-ROUTER(config-if)#ex
ISP-ROUTER(config)#int e0/
*Feb 25 15:45:31.462: %LINK-3-UPDOWN: Interface Ethernet0/0, changed state to up
*Feb 25 15:45:32.466: %LINEPROTO-5-UPDOWN: Line protocol on Interface Ethernet0/0, changed state to up
ISP-ROUTER(config)#int e0/1
ISP-ROUTER(config-if)#ip address 20.13.1.1 255.255.255.0
ISP-ROUTER(config-if)#no sh
ISP-ROUTER(config-if)#ex
ISP-ROUTER(config)#int e0/2
ISP-ROUTER(config-if)#
*Feb 25 15:45:47.848: %LINK-3-UPDOWN: Interface Ethernet0/1, changed state to up
*Feb 25 15:45:48.853: %LINEPROTO-5-UPDOWN: Line protocol on Interface Ethernet0/1, changed state to up
ISP-ROUTER(config-if)#ip address 30.13.1.1 255.255.255.0
ISP-ROUTER(config-if)#no sh
ISP-ROUTER(config-if)#ex
ISP-ROUTER(config)#
*Feb 25 15:46:02.014: %LINK-3-UPDOWN: Interface Ethernet0/2, changed state to up
*Feb 25 15:46:03.014: %LINEPROTO-5-UPDOWN: Line protocol on Interface Ethernet0/2, changed state to up
ISP-ROUTER(config)#ip routing
ISP-ROUTER(config)#do copy run start
Destination filename [startup-config]?
Building configuration...
[OK]
ISP-ROUTER(config)#int e0/0
ISP-ROUTER(config-if)#desc
ISP-ROUTER(config-if)#description ISP_LINK_TO_NETHERLANDS
ISP-ROUTER(config-if)#no sh
ISP-ROUTER(config-if)#ex
ISP-ROUTER(config)#int e0/1
ISP-ROUTER(config-if)#des
ISP-ROUTER(config-if)#description ISP_LINK_TO_GERMANY
ISP-ROUTER(config-if)#NO SH
ISP-ROUTER(config-if)#
ISP-ROUTER(config-if)#ex
ISP-ROUTER(config)#int e0/2
ISP-ROUTER(config-if)#desc
ISP-ROUTER(config-if)#description ISP_LINK_TO_NORWAY
ISP-ROUTER(config-if)#NO SH
ISP-ROUTER(config-if)#ex
ISP-ROUTER(config)#do copy run start
Destination filename [startup-config]?
Building configuration...
[OK]
ISP-ROUTER(config)#
NETHERLANDS FIREWALL GENERAL CONFIGURATION
After you complete all this configuration, all your subnets will be able to connect internet. Afterwards we will configure IPSEC between sites.
GERMANY FIREWALL GENERAL CONFIGURATION
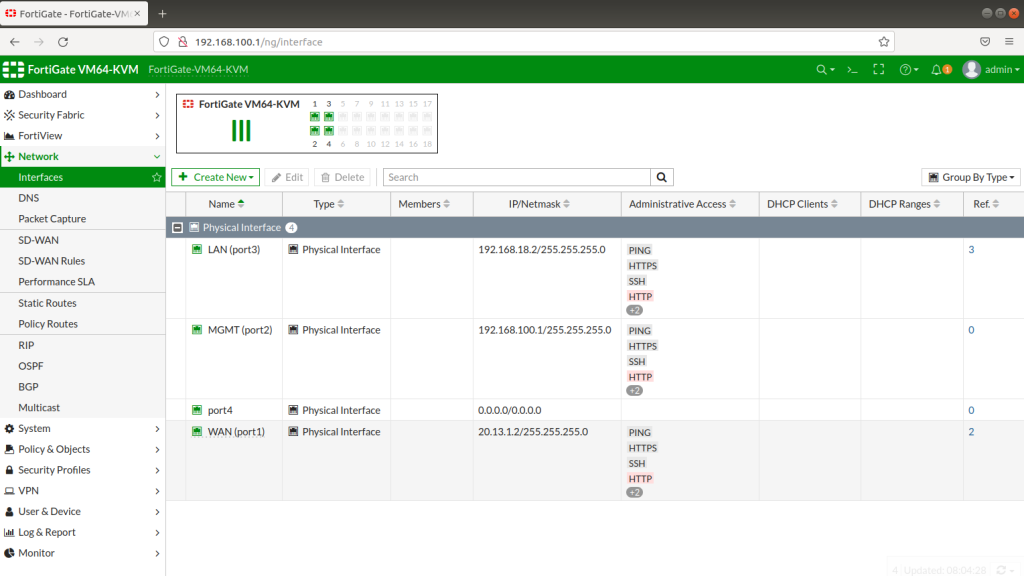
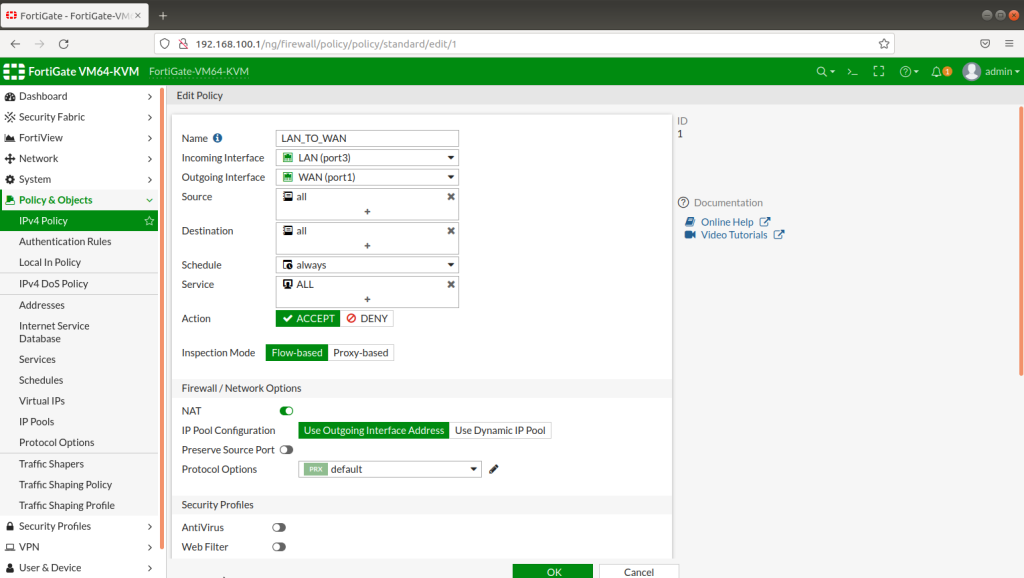
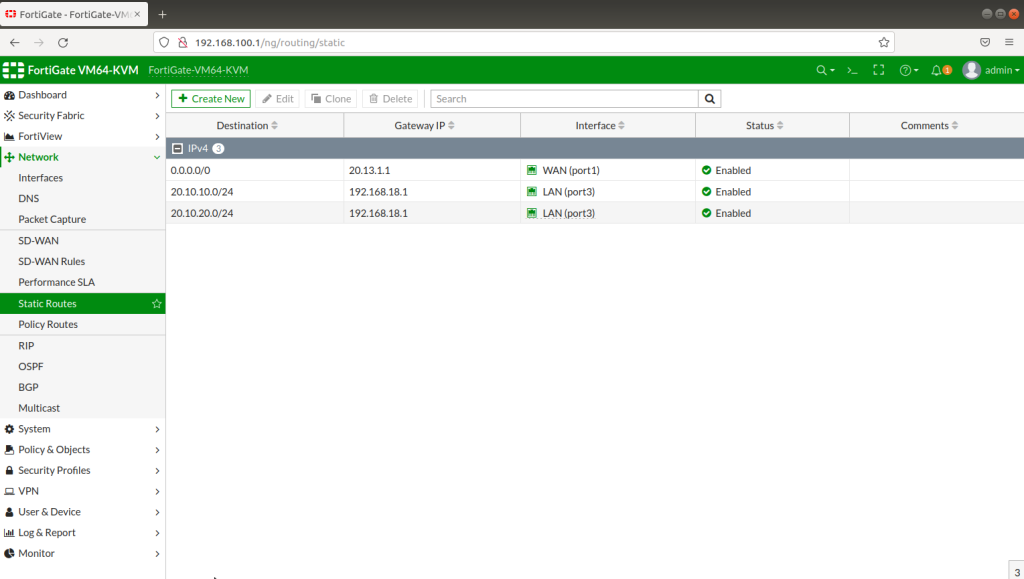
NORWAY FIREWALL GENERAL CONFIGURATION
These configurations are essential to connect your subnets to internet. Not for IPSEC tunnels.
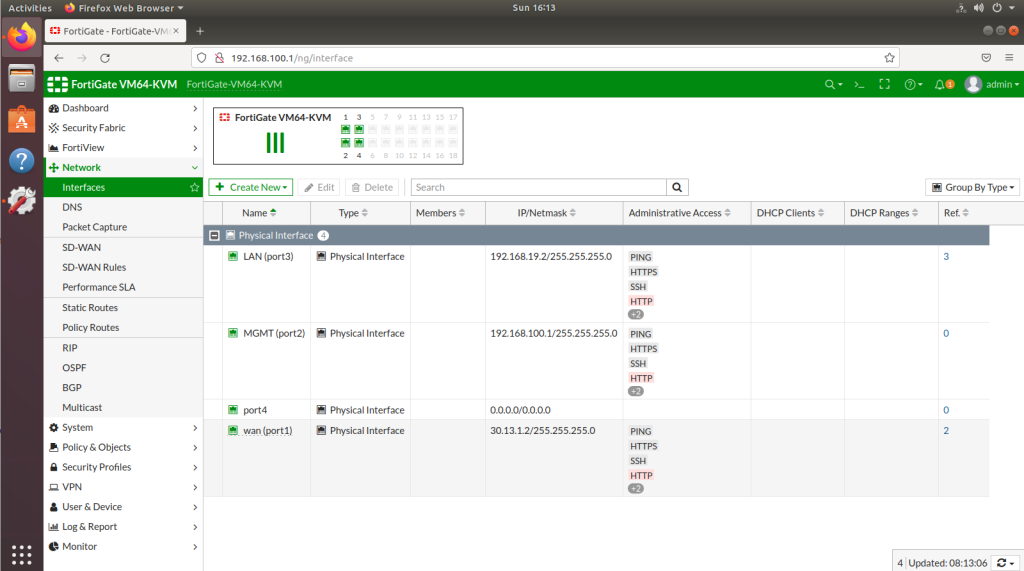
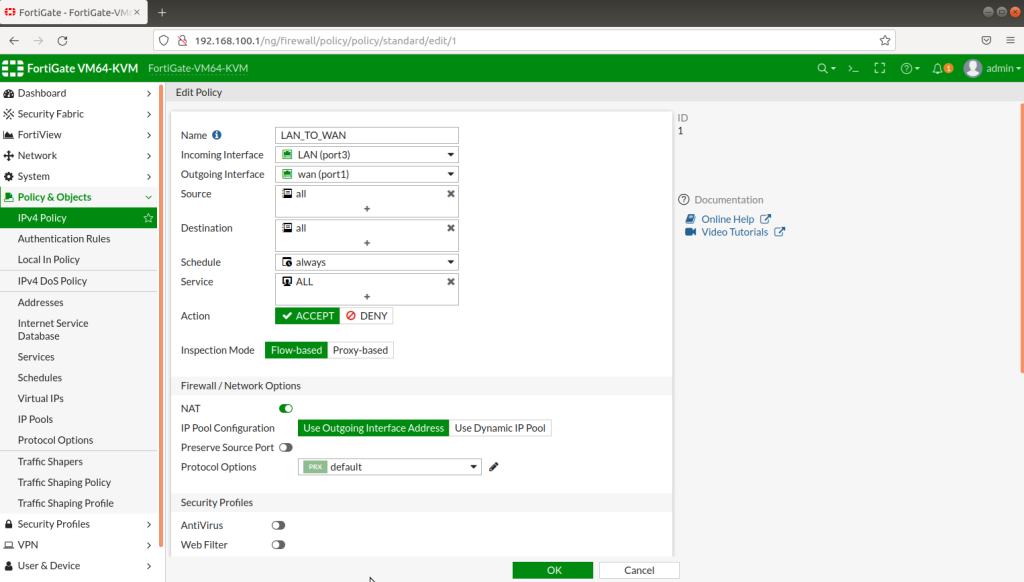
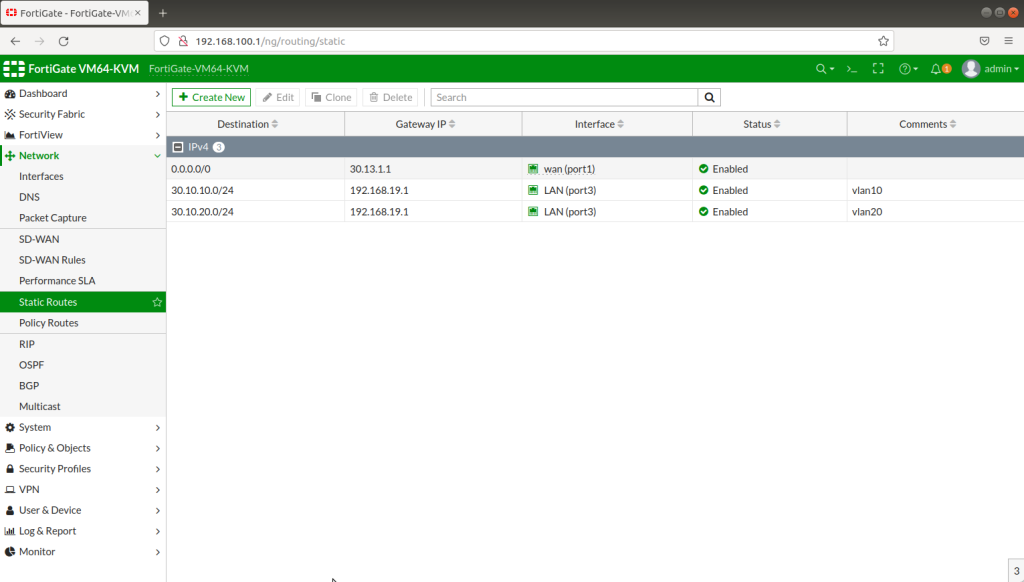
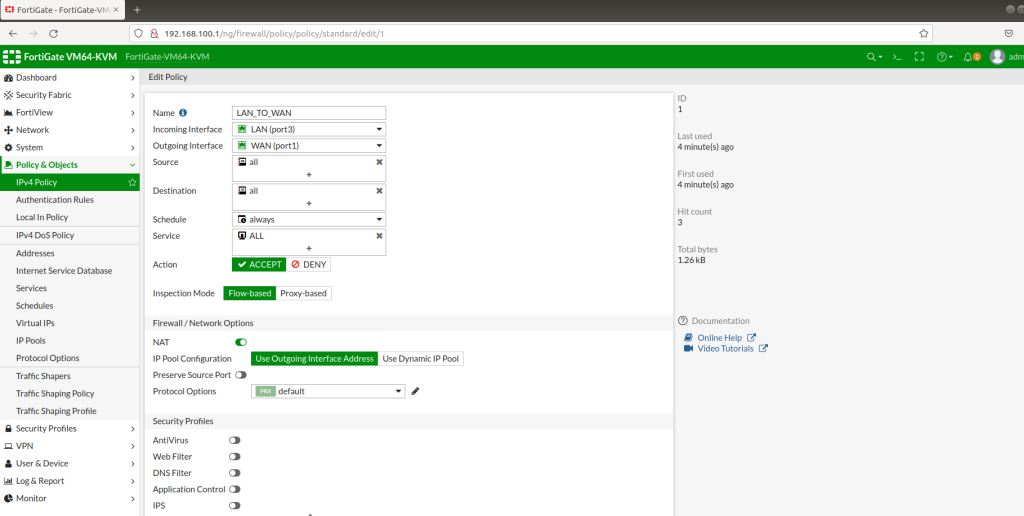
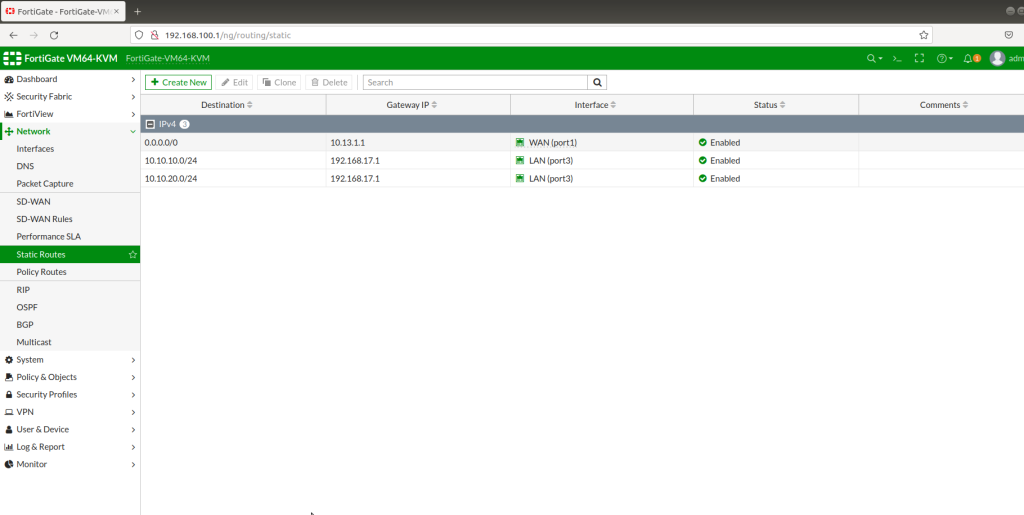
After completing Interface setups, static routes, IPV4 policies, our subnets can ping to WAN IPS gateway (internet access). Now we will configure IPSECs. As in the example you will see for one site, then you will implement the same for other sites as shown. During IPSEC installation, most important thing is that make sure you add your local and remote vlan subnets.
IPSEC Tunnel Netherlands to Norway
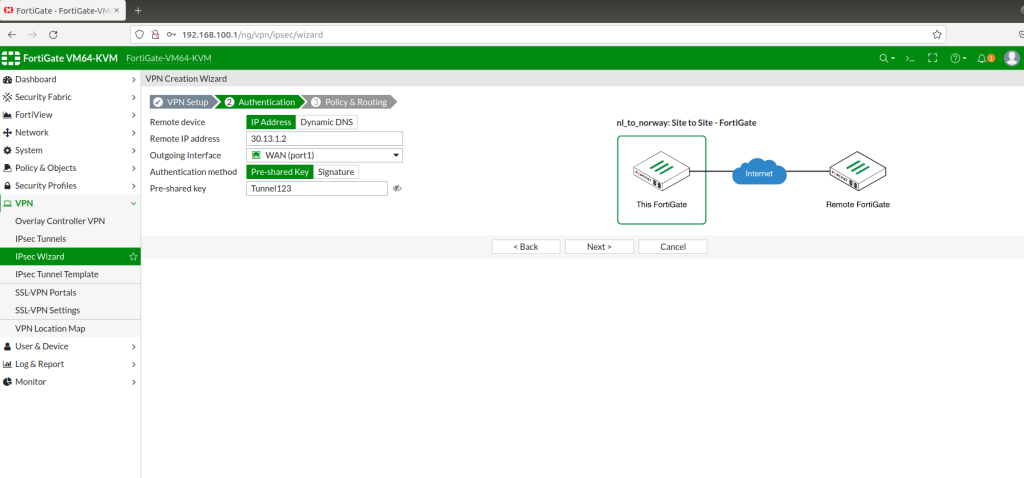
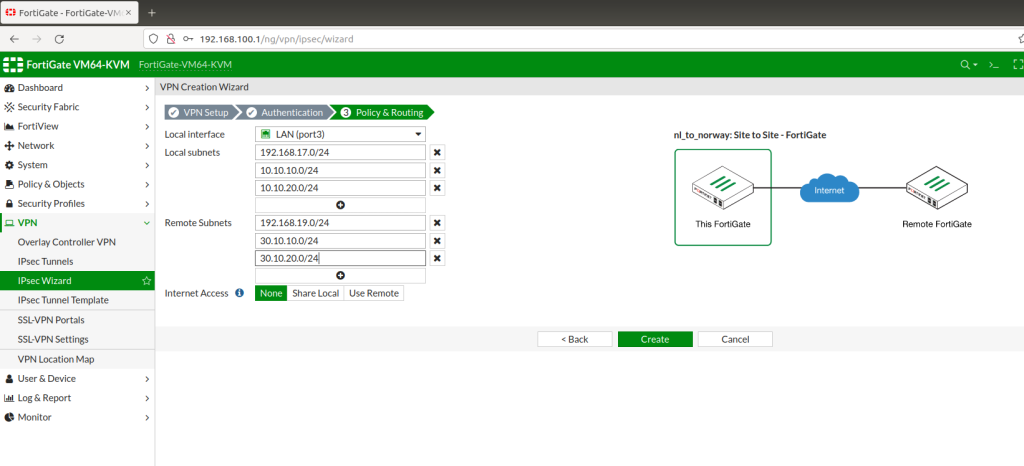
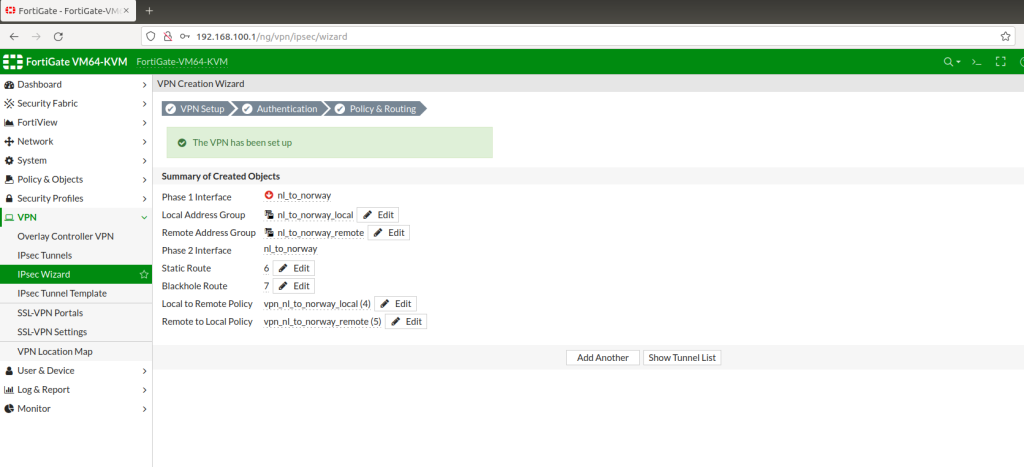
IPSEC Norway to Netherlands
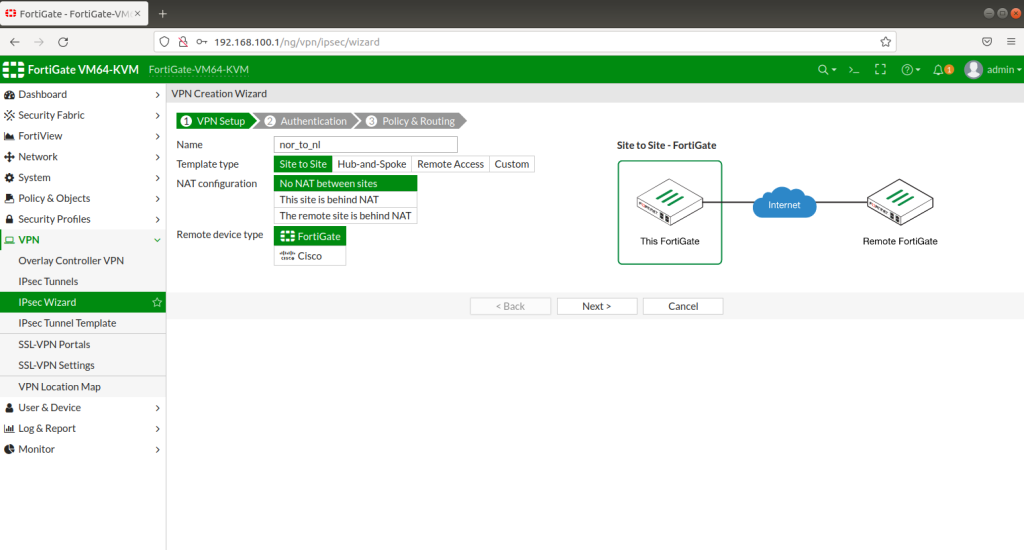
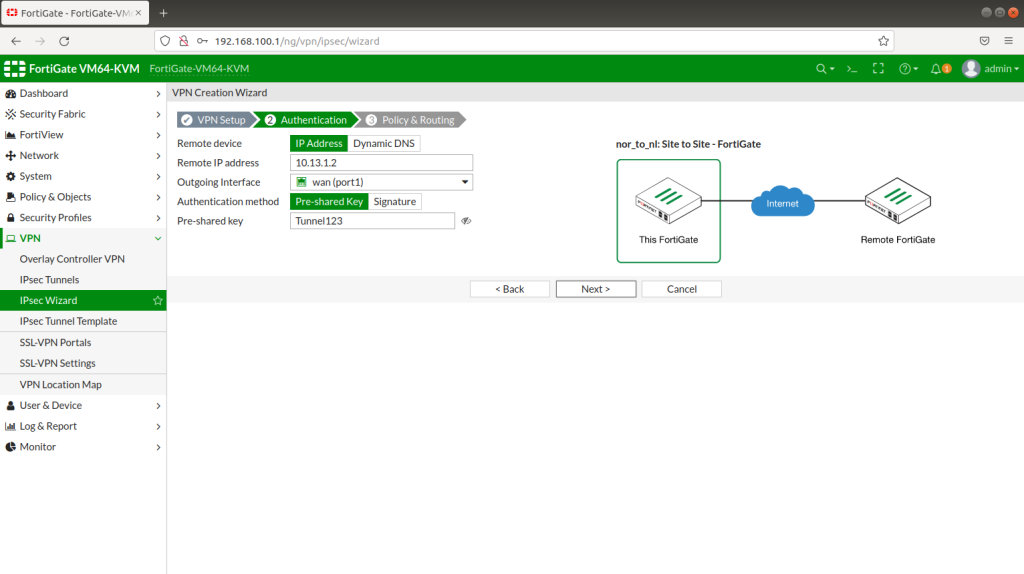
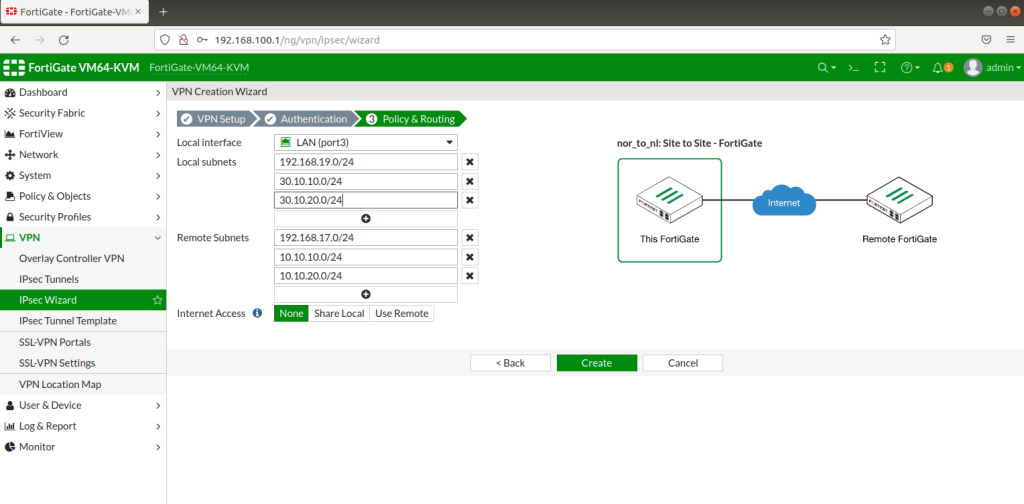
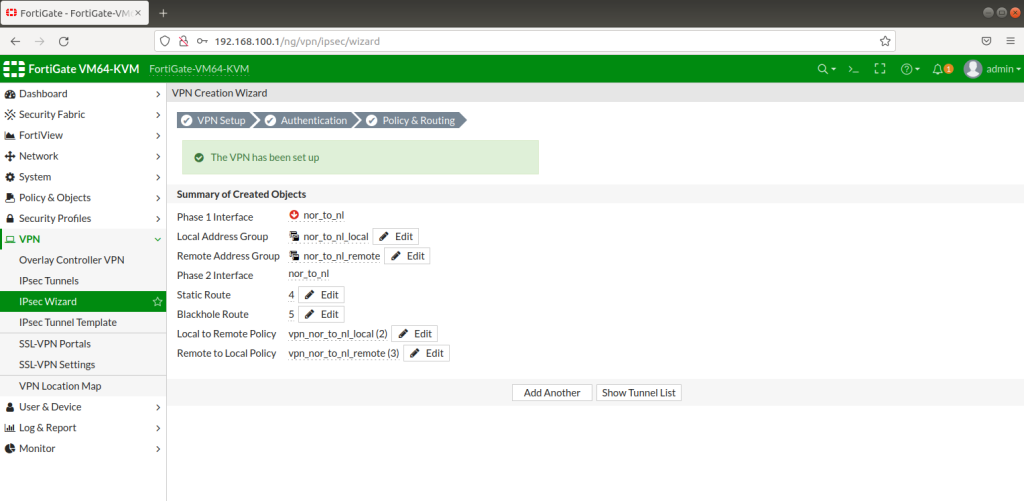
After completing the configuration, you will realize that the tunnels are not up! This is because it is still trying to recognize subnets, vlans and routings. Tunnel will show up as green after a while as below.
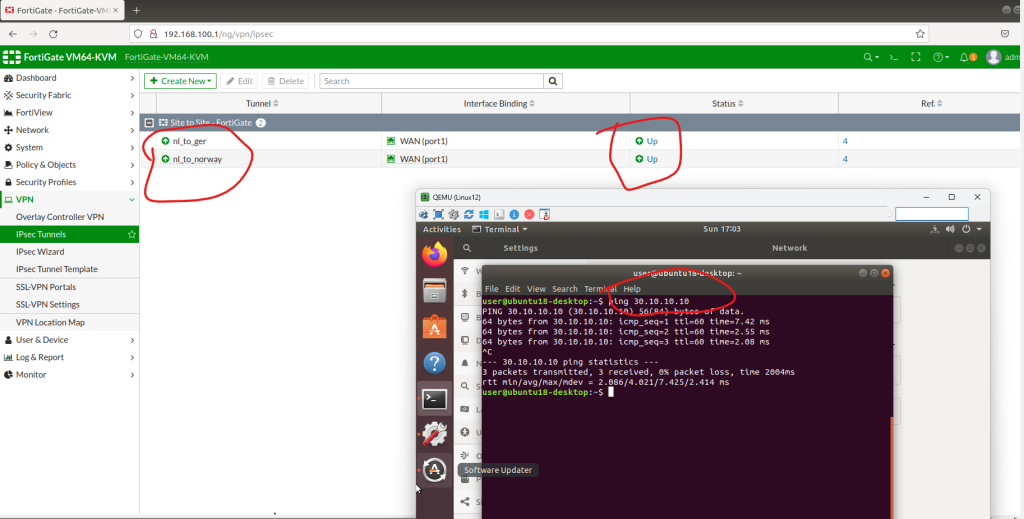
Do the same for all other sites. You will have 3 sites, 6 IPSEC tunnels. Each of the vlan subnets can reach each other.
Do not hesitate to contact me if you have any questions.
Happy networking 🙂