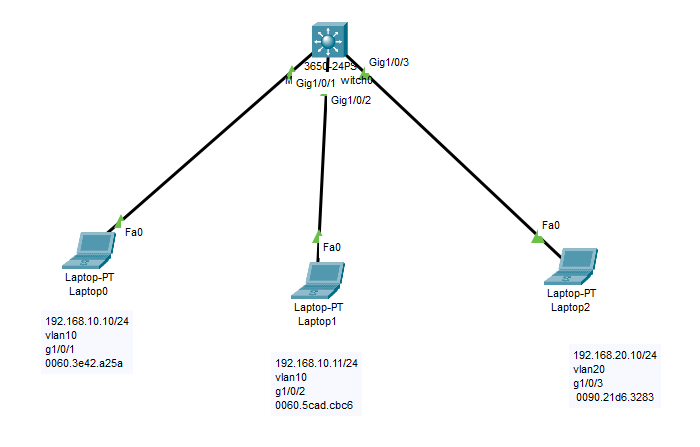
[Hacking Series/Lab 1] – VLAN Hopping Attack ! This training was created for preventive defensive purposes.
Disclaimer: These methods and techniques are purely for educational and informational purposes. All attacks were carried out in an offline isolated virtual environment. The use of these techniques in normal life is illegal and the responsibility lies strictly with the reader. DO NOT USE THESE TECHNIQUES IN REAL LIFE ! In this training, I will […]
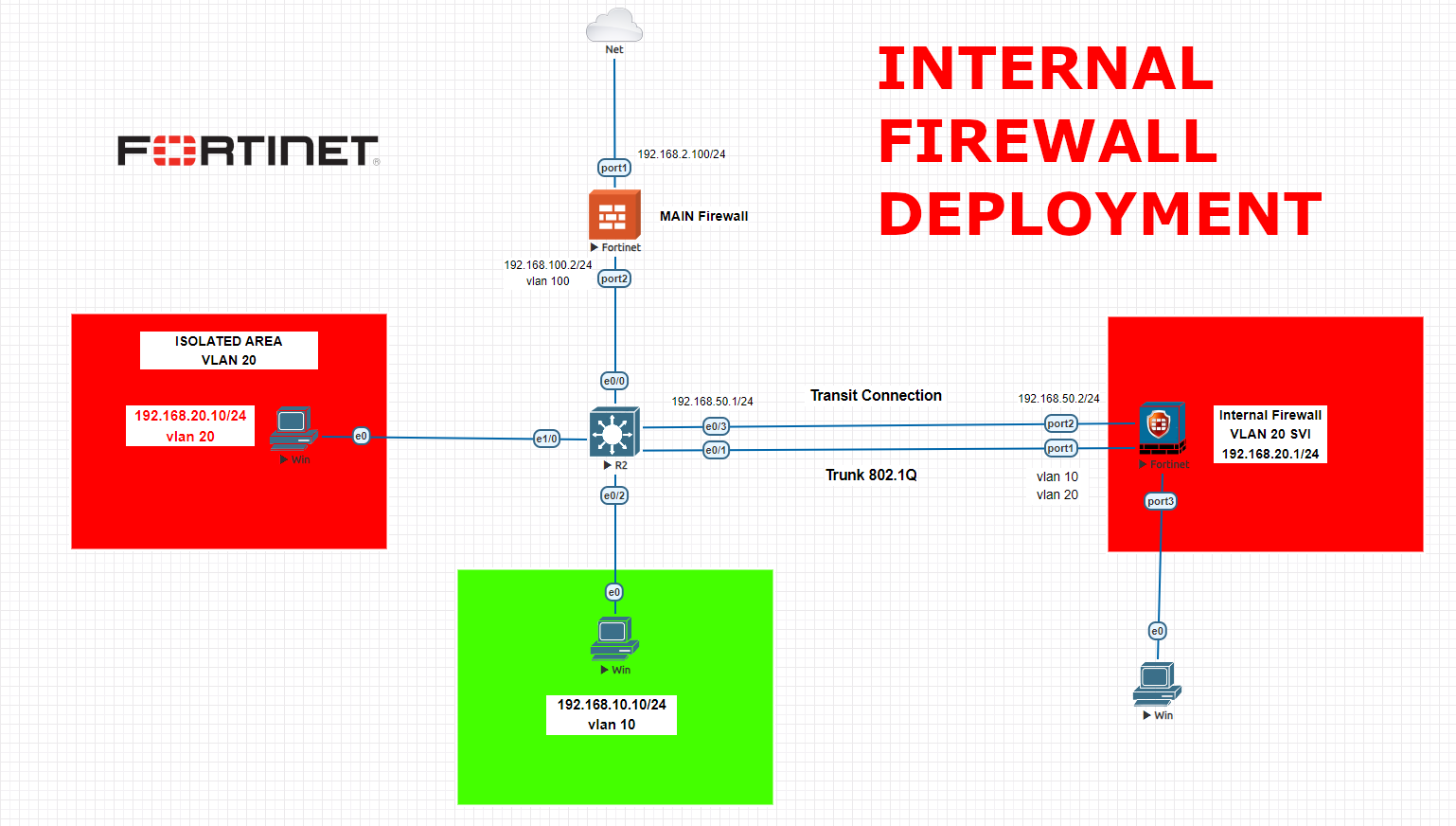
OT/IT Security – Internal Firewall Fortigate Implementation with configurations for your critical networks
An internal firewall, also known as an internal network firewall or a segment firewall, is a security system designed to protect and control traffic between different segments within an organization’s internal network. Unlike a perimeter firewall, which protects the network from external threats, an internal firewall focuses on securing the internal network by regulating the […]
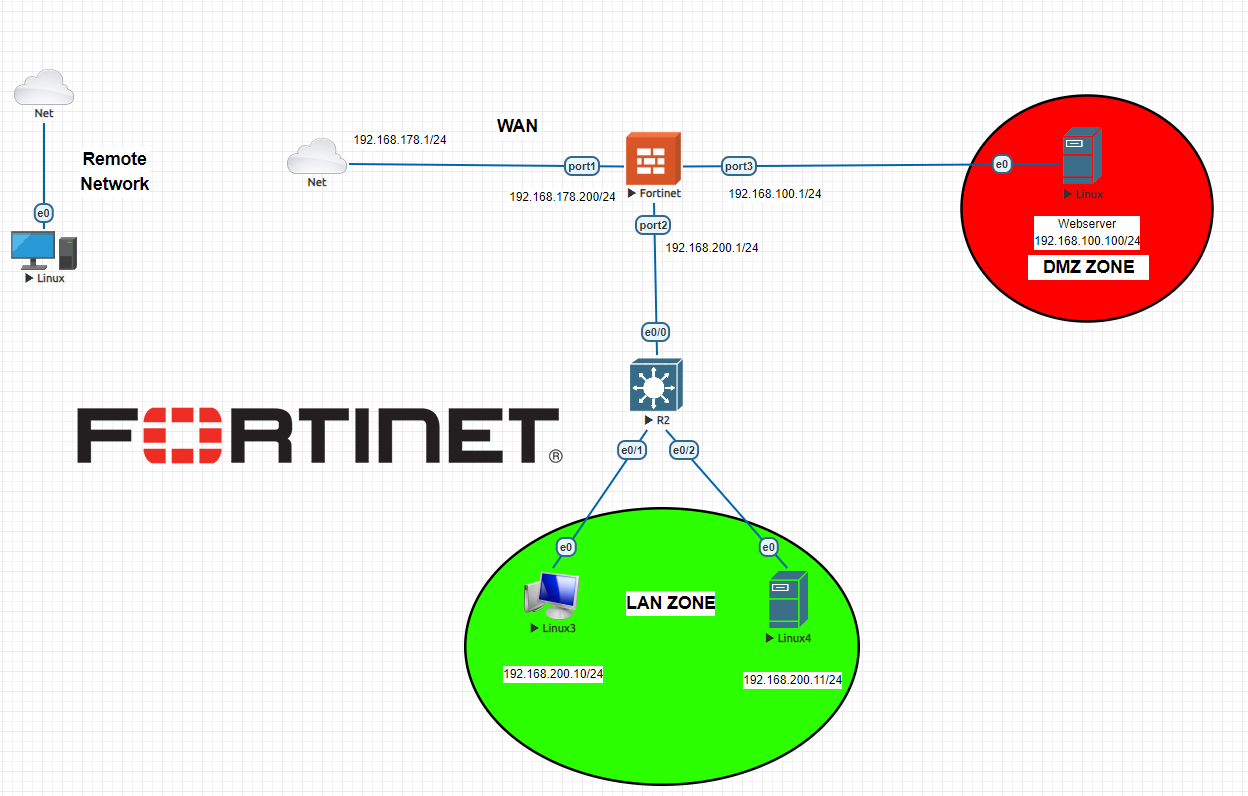
How to create DMZ (Demilitarized Zone) on Fortigate Firewall?
What is DMZ (Demilitarized Zone)? A DMZ (Demilitarized Zone) in computer networking refers to a physical or logical subnetwork that contains and exposes an organization’s external-facing services to an untrusted network, usually the internet. The purpose of a DMZ is to add an additional layer of security to an organization’s local area network (LAN); an […]
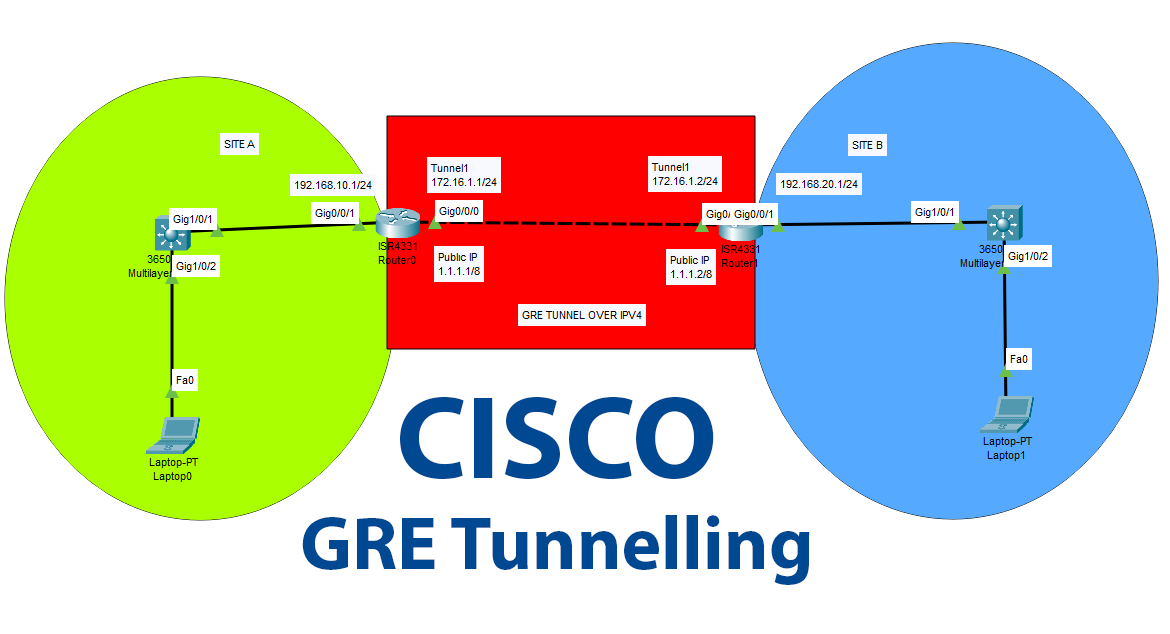
GRE Tunnels between multiple sites
A GRE (Generic Routing Encapsulation) tunnel in Cisco is a method of encapsulating and tunneling network traffic over an IP network. It allows the creation of a virtual point-to-point link between two endpoints, typically routers or switches, across an existing network infrastructure. Here’s how it works: GRE tunnels are often used for various purposes, such […]
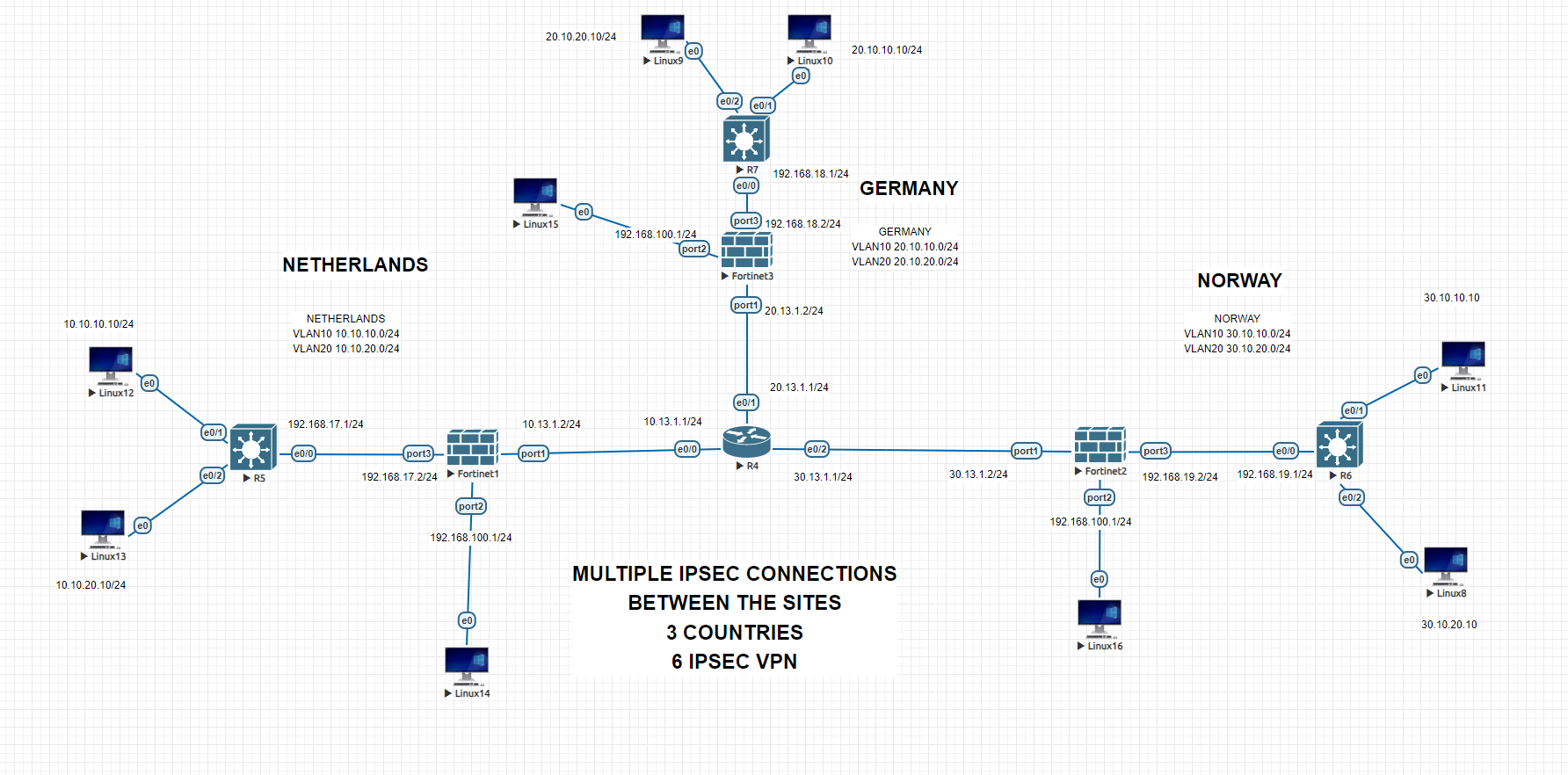
Multiple company-sites IPSEC connection with multiple VLANs
IPsec, short for Internet Protocol Security, is a suite of protocols used to ensure secure communication over IP networks. It provides security services at the IP layer by enabling encryption, authentication, and integrity checking of IP packets. IPsec can be used to establish secure VPN (Virtual Private Network) connections between remote networks or individual devices, […]
Ethernet MAC Port-security
Today we will implement port security on our Cisco switch. We will bind the MAC address of the NIC device with our related port. So if some changes happen on the physical ports, then new device will be restricted. CISCO SWITCH MAIN CONFIGURATION Switch>enable Switch#configure terminal Enter configuration commands, one per line. End with CNTL/Z. […]
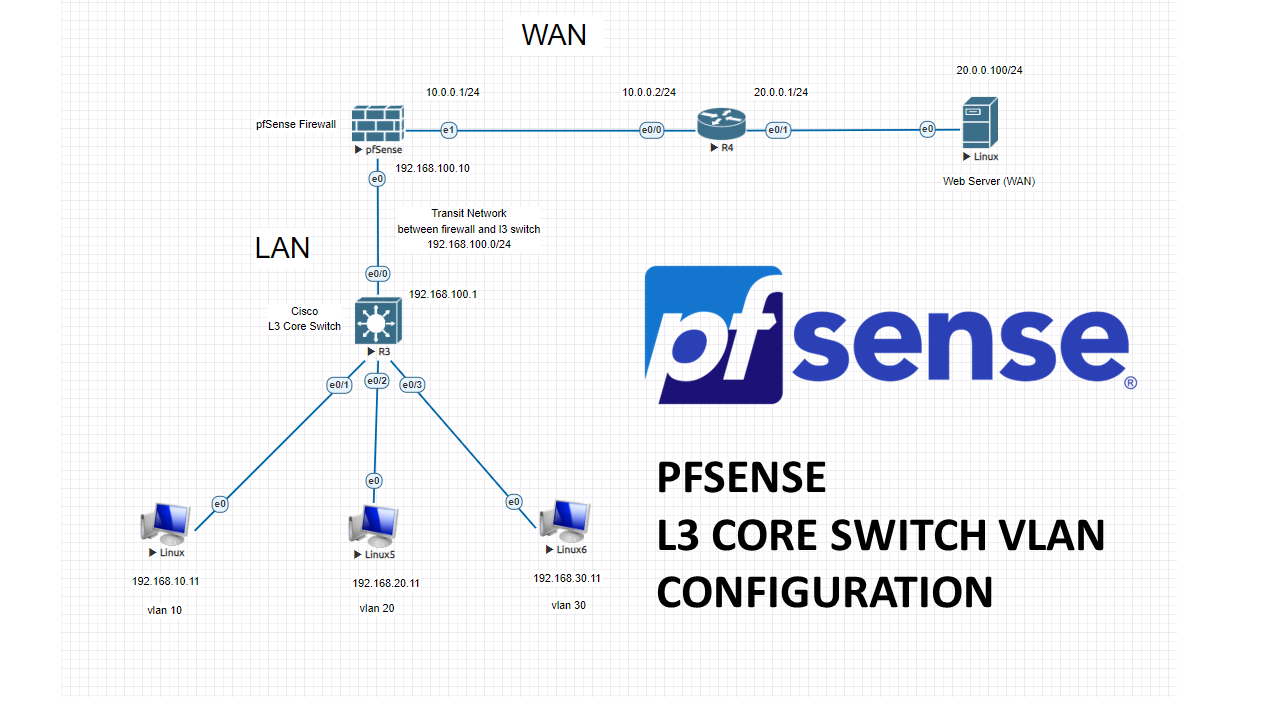
PfSense firewall + L3 Core switch configuration with VLANs
In this lab, we will create 3 vlans and connect our core switch to pfSense firewall with a transit network. Then we will configure our firewall with these vlan subnets. LAN related traffic will not hit the firewall, because SVIs (VLANgateways) will be created on L3 Core switch. All the necessary permissions between vlans will […]
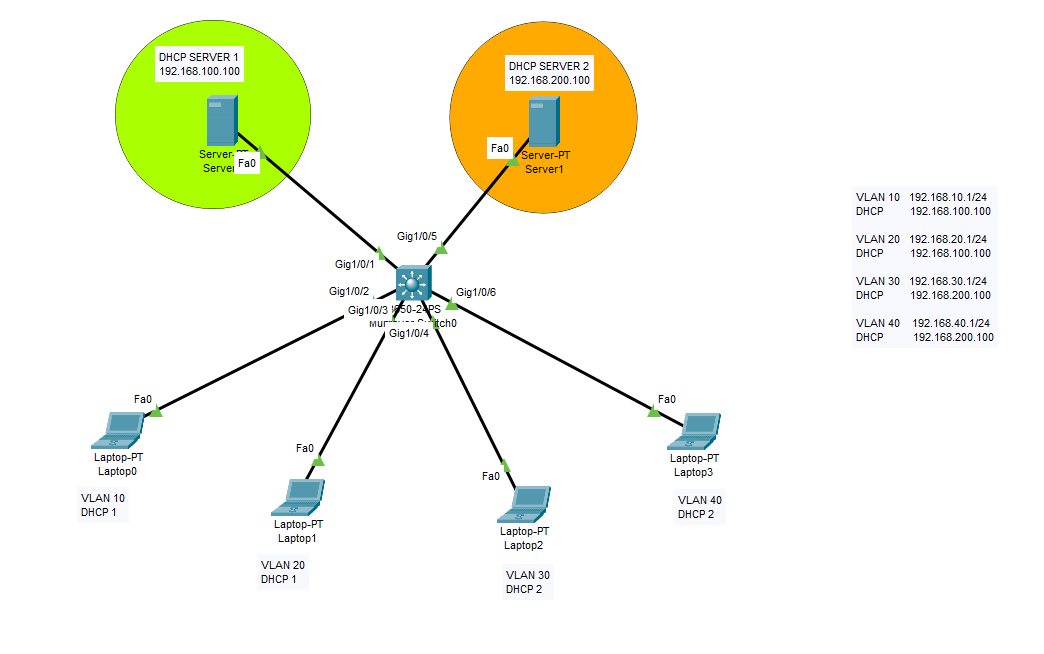
Multiple DHCP Server Configurations For VLANs
On this practice lab, we will configure two DHCP servers for 4 different VLANs. We will create the VLANs on the core switch, then we will assign the DHCP servers to VLANs with the command of “ip helper-address“. By this method, you will be able to use different DHCP servers for different purposes. Cisco Core […]
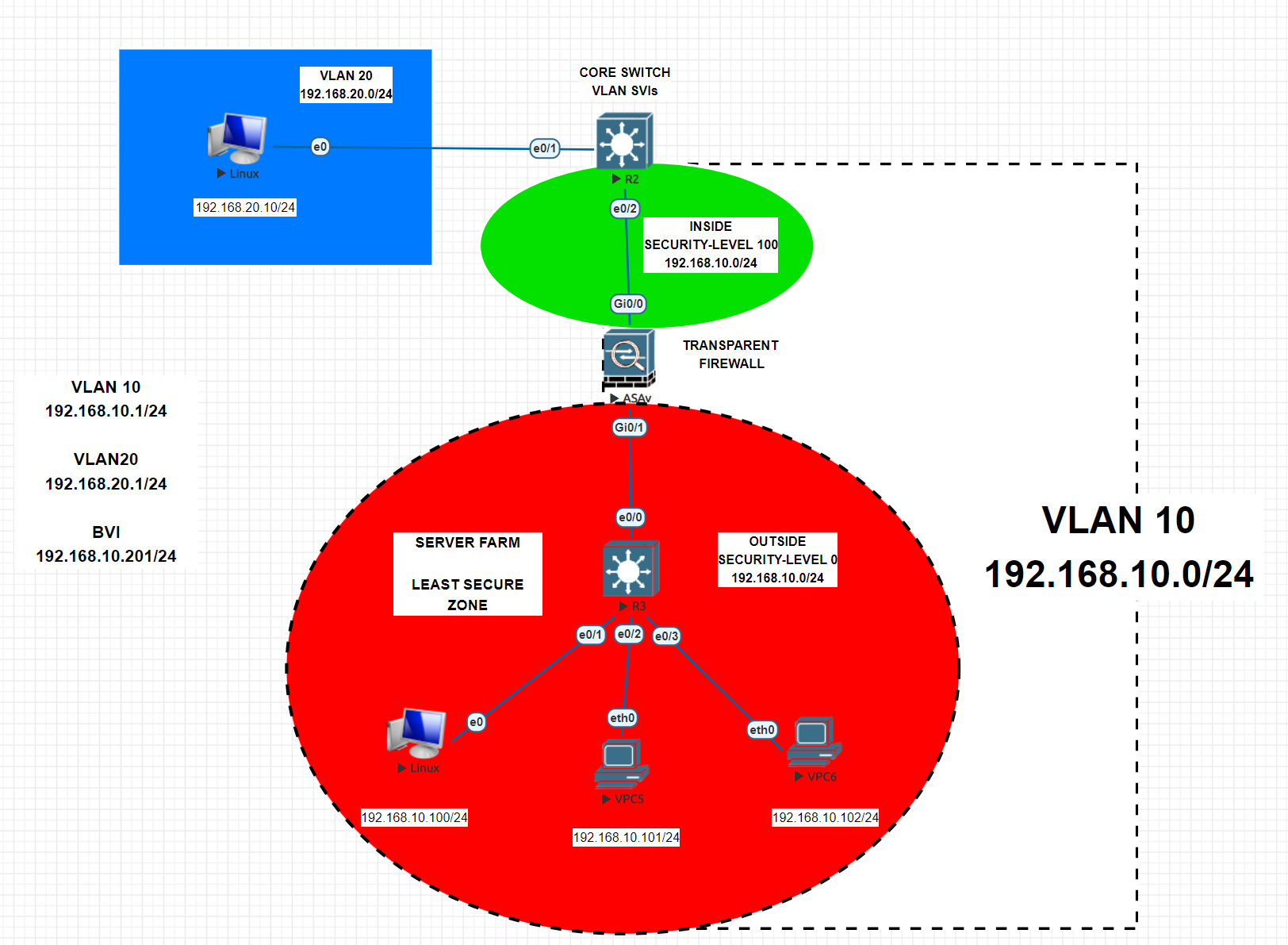
Cisco ASA Transparent Internal Firewall Configuration
Cisco ASA (Adaptive Security Appliance) is a security device that provides firewall, VPN, and other security services for networks. It can operate in multiple modes, including Routed Mode and Transparent Mode. Let’s focus on Cisco ASA Transparent Mode. In Transparent Mode, the Cisco ASA firewall is inserted into a network without requiring any IP address […]
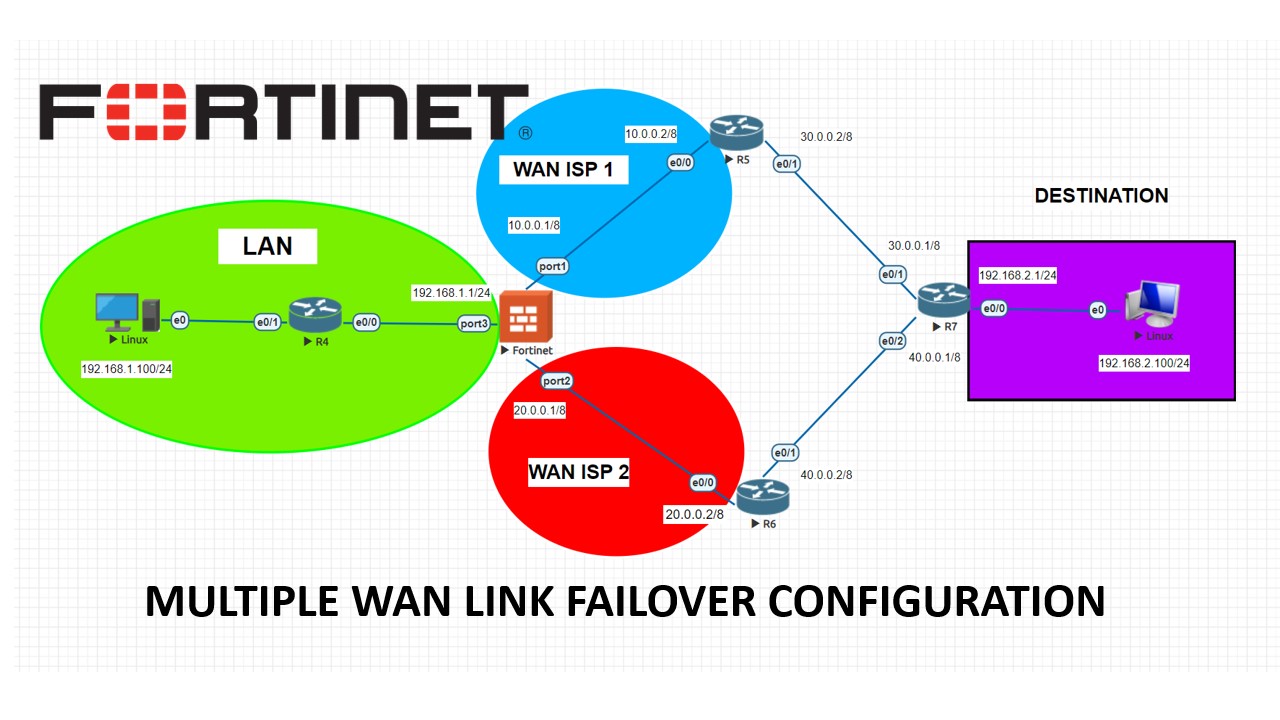
Fortinet Firewall – Multiple WAN ISP Basic Failover
On our topology, we have Fortigate firewall, Cisco routers and 2 ISP provider with 20.0.0.2 and 10.0.0.2 gateways. We would like to setup a basic failover on Fortigate firewall which will allow us to use 2nd ISP link if ISP-1 drops. Basic idea behind this is “administrative distance” on Static routes on the firewall. We […]
![[Hacking Series/Lab 1] – VLAN Hopping Attack ! This training was created for preventive defensive purposes.](https://barisyuksel.com.tr/wp-content/uploads/2024/07/vlan-hopping-diagram2.png)