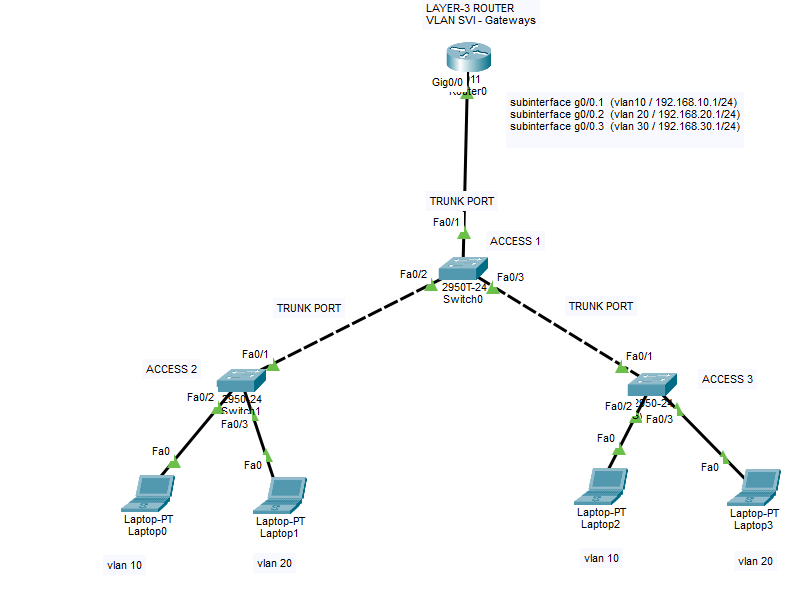
Router On A Stick Method for Layer 2 switches (ROAS Inter-vlan Legacy Communication) CISCO
In this lab, we will inspect how intervlan communication handled on Layer-3 Router with Router On a Stick model. If you have layer 2 switches for end devices, then you will need a layer 3 router or switch for intervlan communication. Layer 2 devices cannot do IP routing between VLAN gateways (SVIs) so therefore you […]
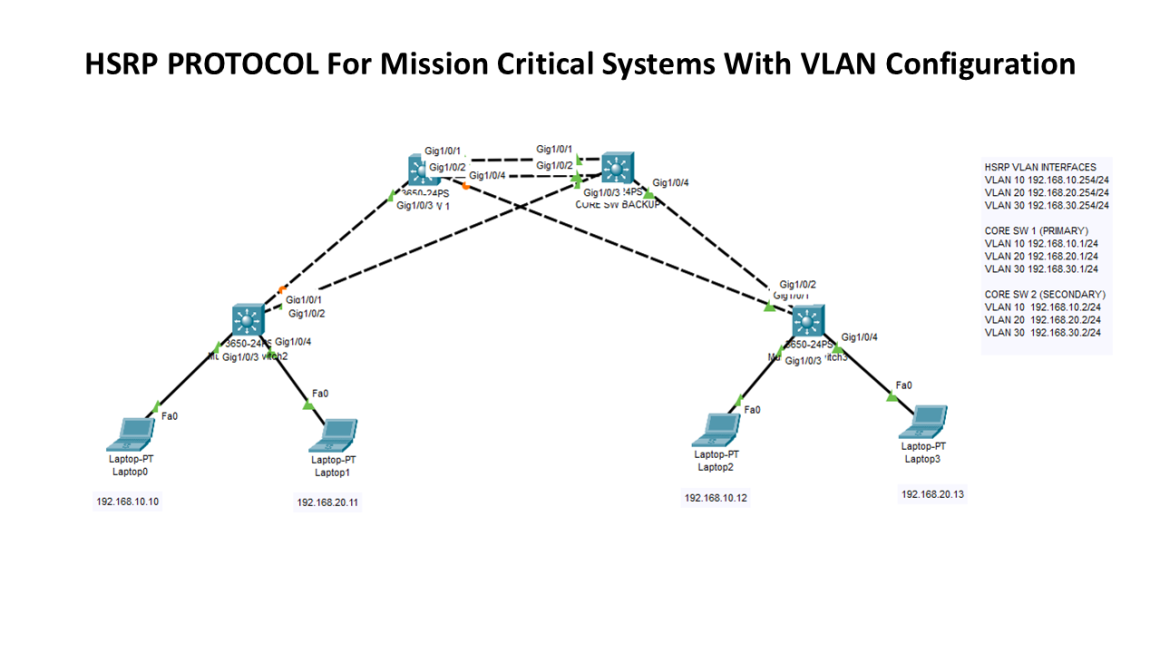
Mission Critical Systems L3 Core Switch HA
In this lab, we will use HSRP protocol to create high availability for our topology using two core switches as primary and secondary (backup) in case of a failure. By this way, we will avoid single point of failure and eliminate the system downtime. HSRP (Hot Standby Router Protocol) is a redundancy protocol developed by […]
[Hacking Series/Lab 4] –How to launch MAN IN THE MIDDLE Attack? (ARP poisoning)
Disclaimer: These methods and techniques are purely for educational and informational purposes. All attacks were carried out in an offline isolated virtual environment. The use of these techniques in normal life is illegal and the responsibility lies strictly with the reader. DO NOT USE THESE TECHNIQUES IN REAL LIFE ! ARP poisoning and Man-in-the-Middle (MITM) […]
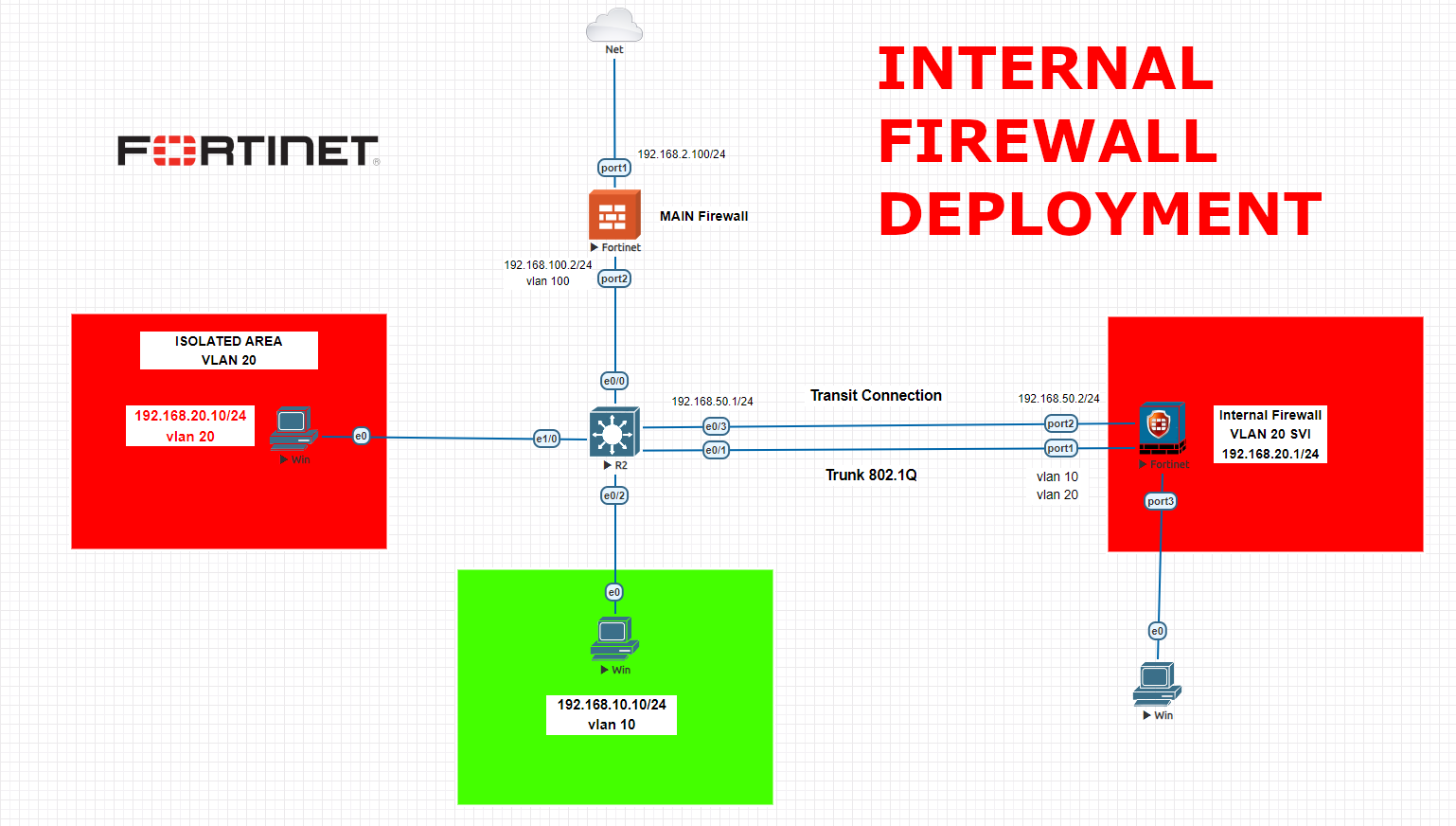
OT/IT Security – Internal Firewall Fortigate Implementation with configurations for your critical networks
An internal firewall, also known as an internal network firewall or a segment firewall, is a security system designed to protect and control traffic between different segments within an organization’s internal network. Unlike a perimeter firewall, which protects the network from external threats, an internal firewall focuses on securing the internal network by regulating the […]
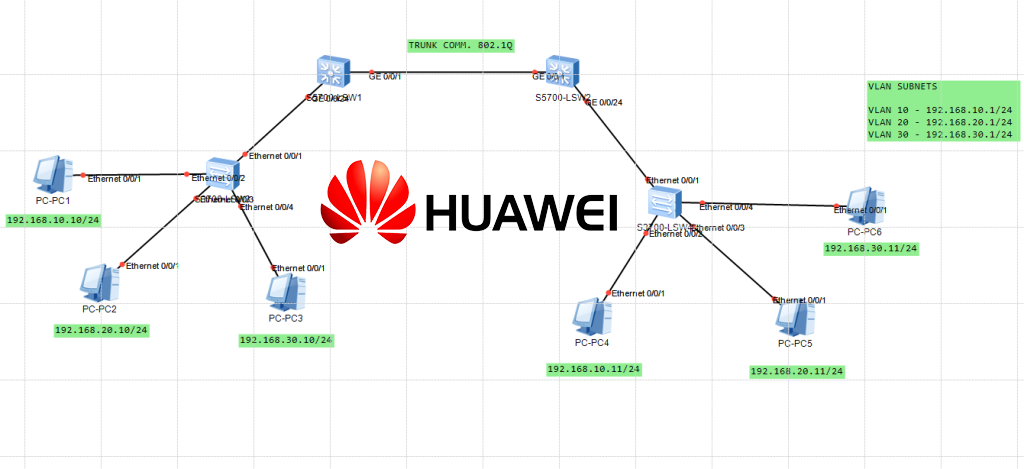
How to create VLANs on Huawei switches?
Huawei switches are network switches developed and produced by Huawei Technologies Co. Ltd., a leading global provider of information and communications technology (ICT) infrastructure and smart devices. Huawei switches offer a wide range of features and functionalities for both small and large-scale enterprise networks, including but not limited to: Huawei switches offer a robust and […]
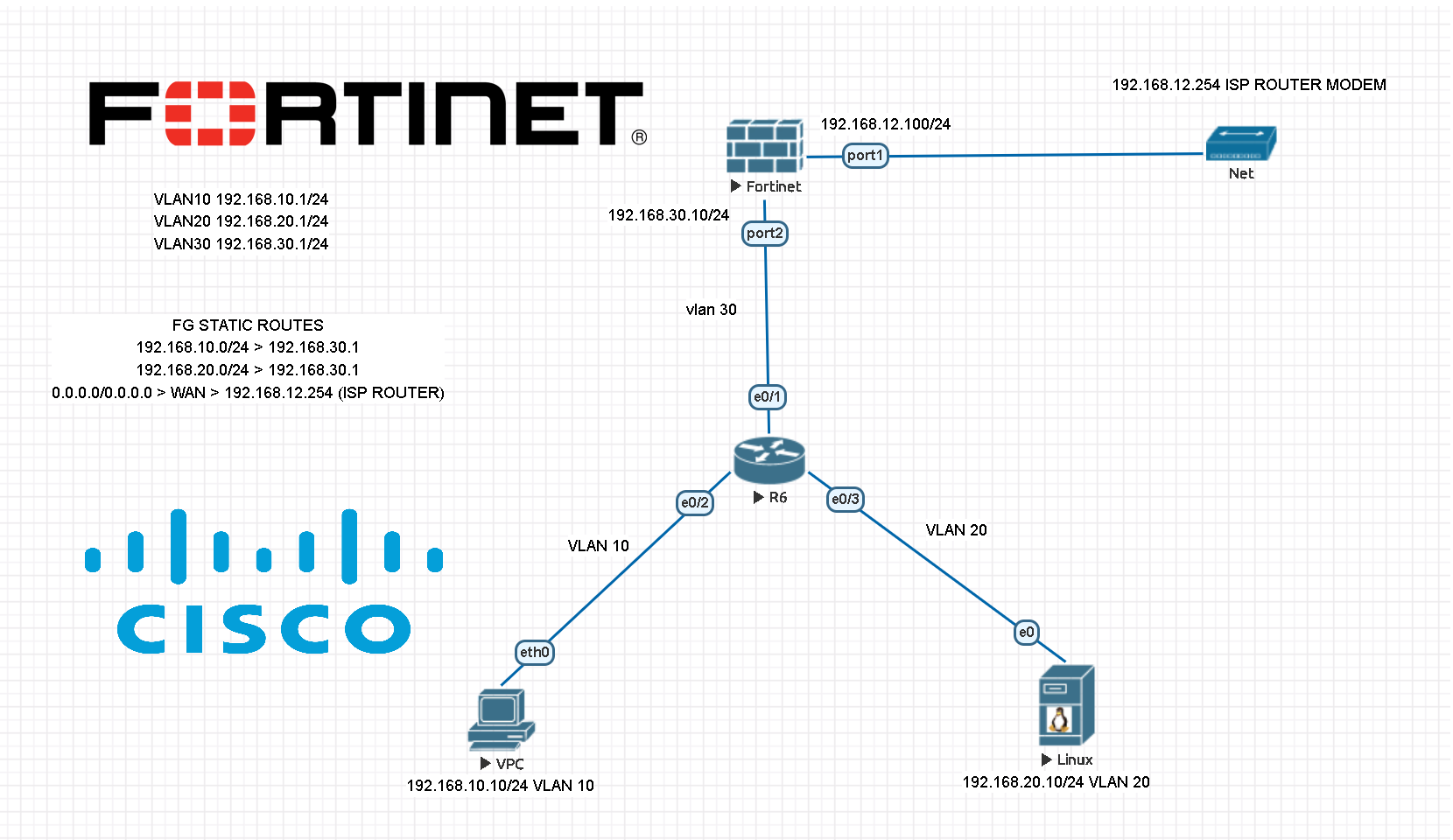
How to setup Fortigate firewall with Cisco core switches configured with VLANs?
Configuring a Fortigate Firewall is an important step for any network administrator. It not only ensures that the firewall is set up correctly, but also helps keep the network secure from any potential threats. In this article, we will discuss how to configure a Fortigate Firewall using CLI, from its first setup to more advanced […]
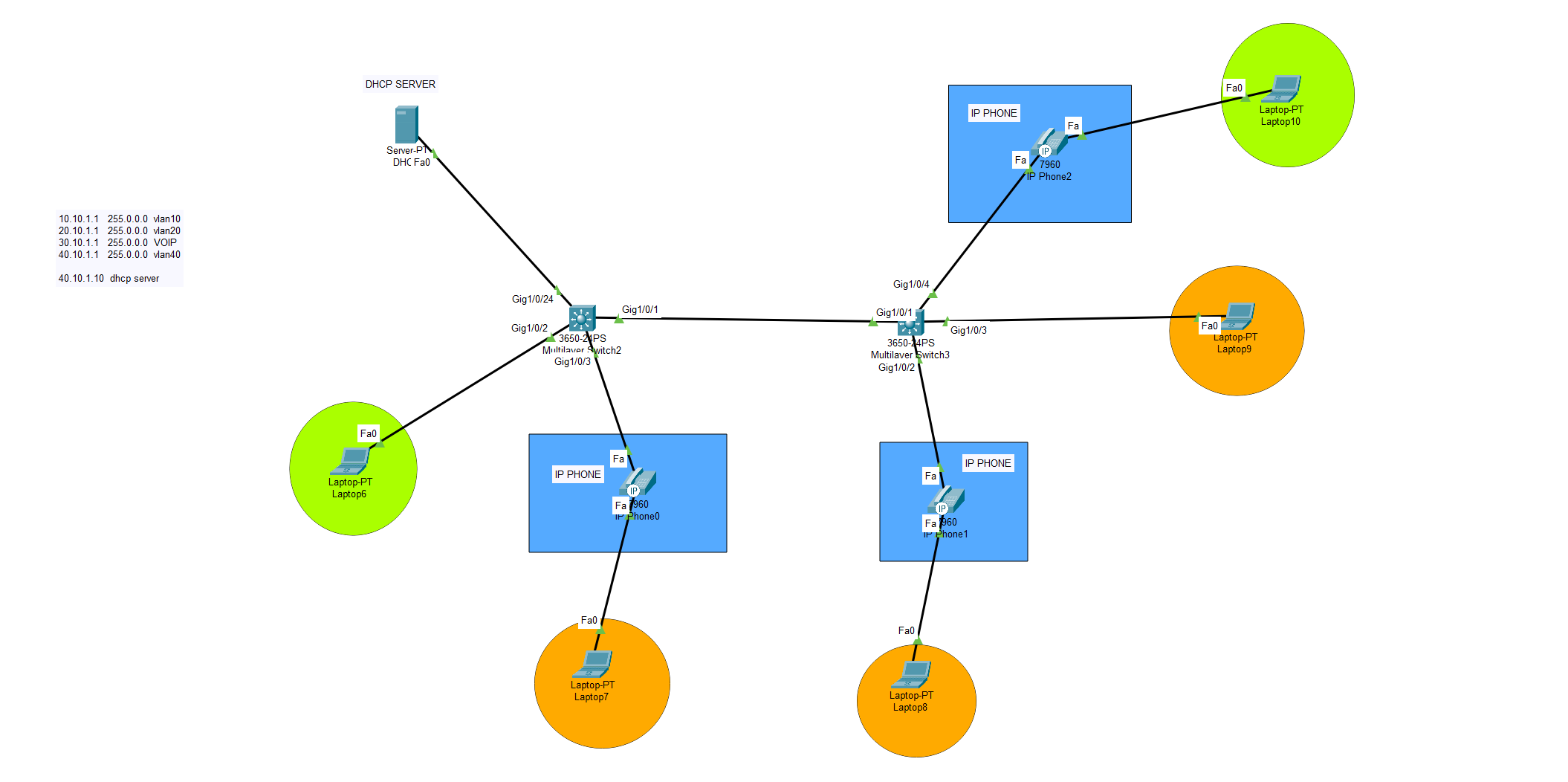
What is Voice VLAN? How to use IP Phones on our network?
Voice VLAN is used to provide voice traffic with a dedicated VLAN. Voice traffic is isolated from other network traffic and so it doesn’t slow down the network. In order to make a work voice vlan and computer together, you should turn on the voice vlan in your cisco phone. This is done by providing […]
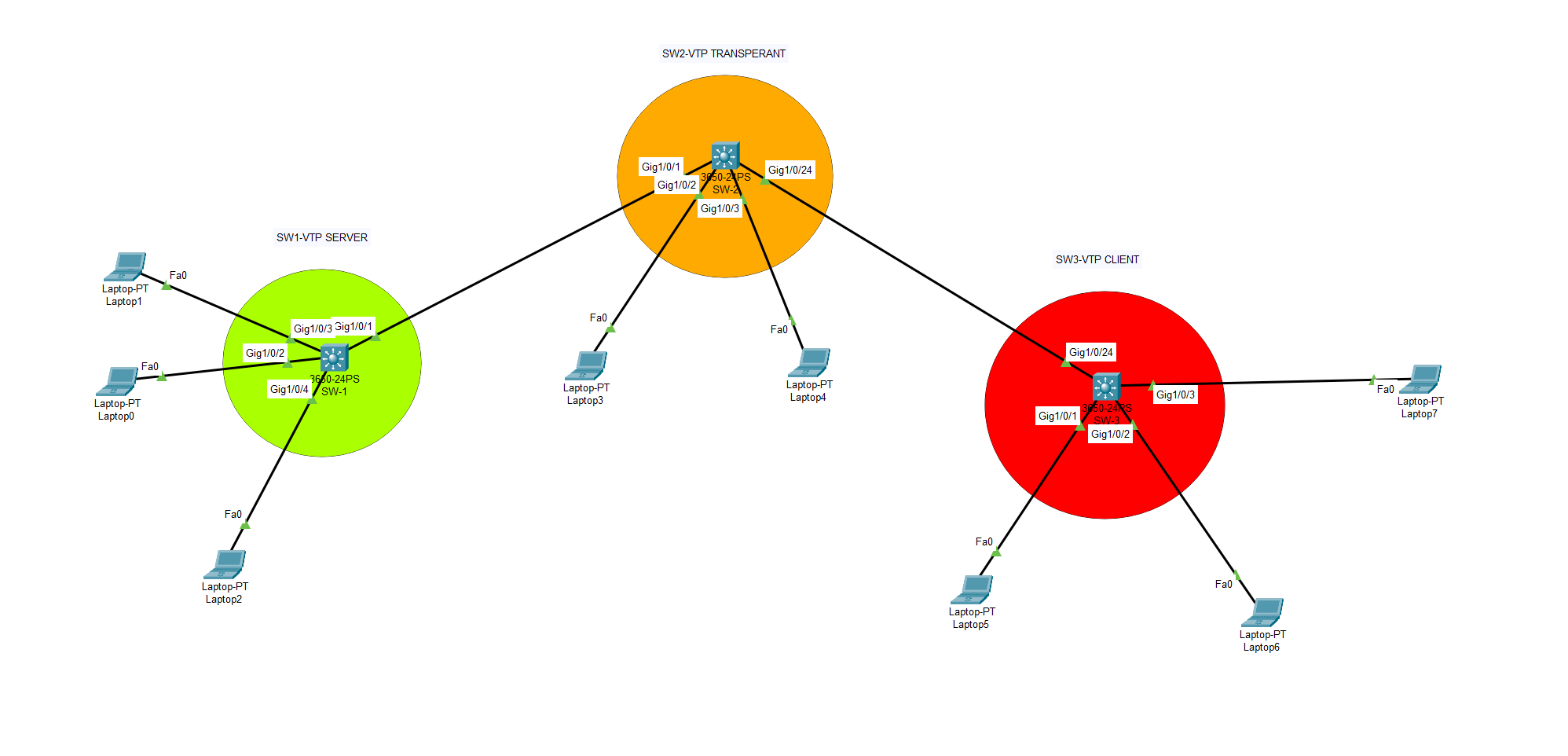
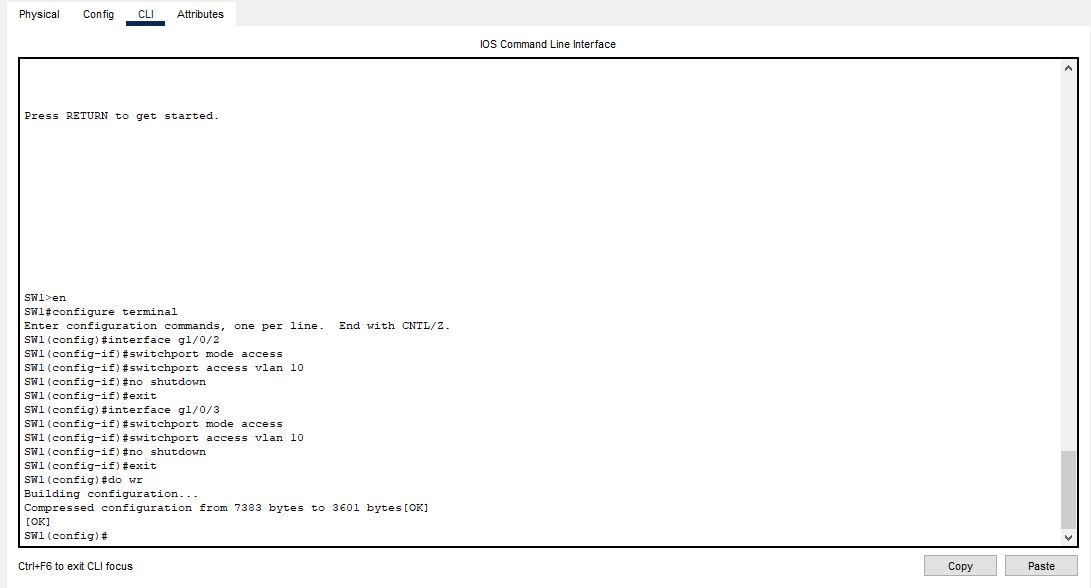
What is VTP (VLAN Trunking Protocol) ?
A VTP server is a switch to which other switches are connected. The VTP server maintains the VLAN database and propagates it to all the other switches. There are three modes in which a VTP server can operate: Server, Client and Transparent. The Server mode is used when there is more than one switch in […]
Extended ACL list for enterprise network system. Download
In this simulation you can find all necessary configuration. You can download .pkt Cisco Package Tracer file and open it on your computer. There are 5 VLAN configured and 1 extended ACL implemented on whole VLANs. Basically, hit CLI tab on the switch which you want to check then enter “show running-configuration” command to see […]
10 Most Used Commands on Cisco OS
#enable This command enables users to enter their commands on the terminal. Moves user to privilege mode. #configure terminal This command allows users to make some changes on the configuration. #show running-configuration This command shows you the latest running configuration on the device. To not to lose your latest configurations which you have done, you […]
![[Hacking Series/Lab 4] –How to launch MAN IN THE MIDDLE Attack? (ARP poisoning)](https://barisyuksel.com.tr/wp-content/uploads/2024/08/mitm_diagram_topology-1035x653.png)