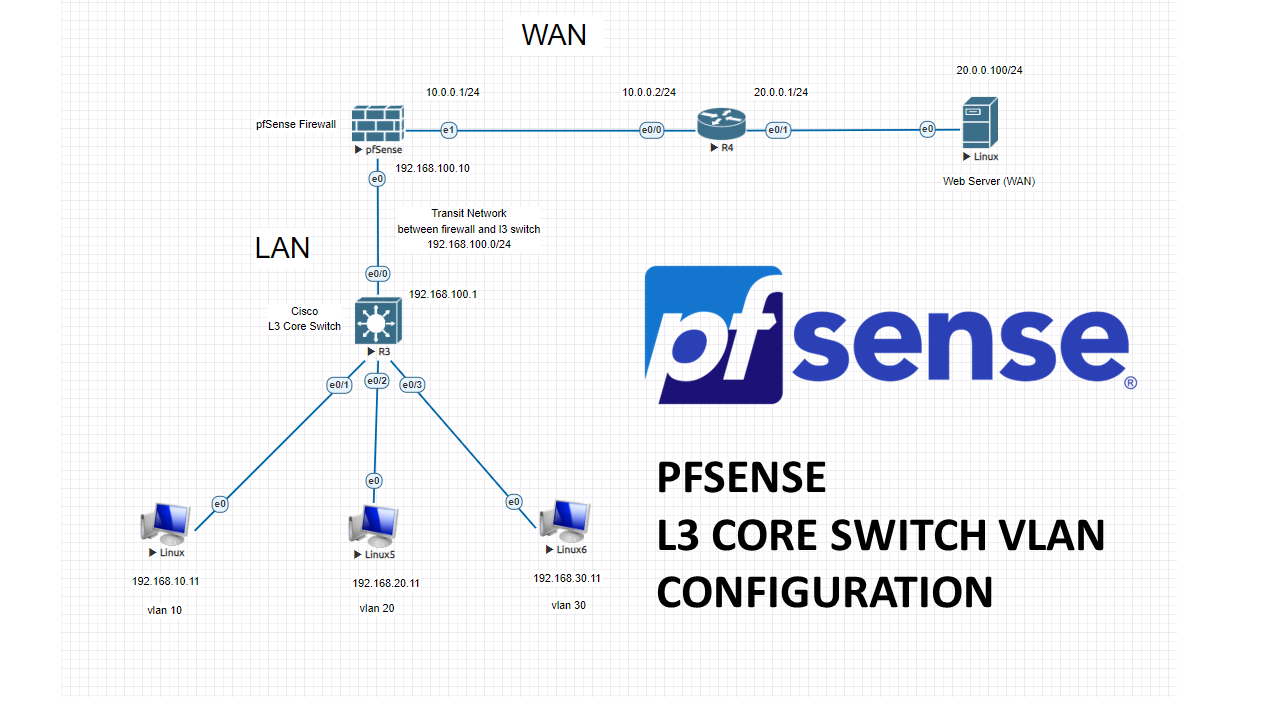
PfSense firewall + L3 Core switch configuration with VLANs
In this lab, we will create 3 vlans and connect our core switch to pfSense firewall with a transit network. Then we will configure our firewall with these vlan subnets. LAN related traffic will not hit the firewall, because SVIs (VLANgateways) will be created on L3 Core switch. All the necessary permissions between vlans will […]
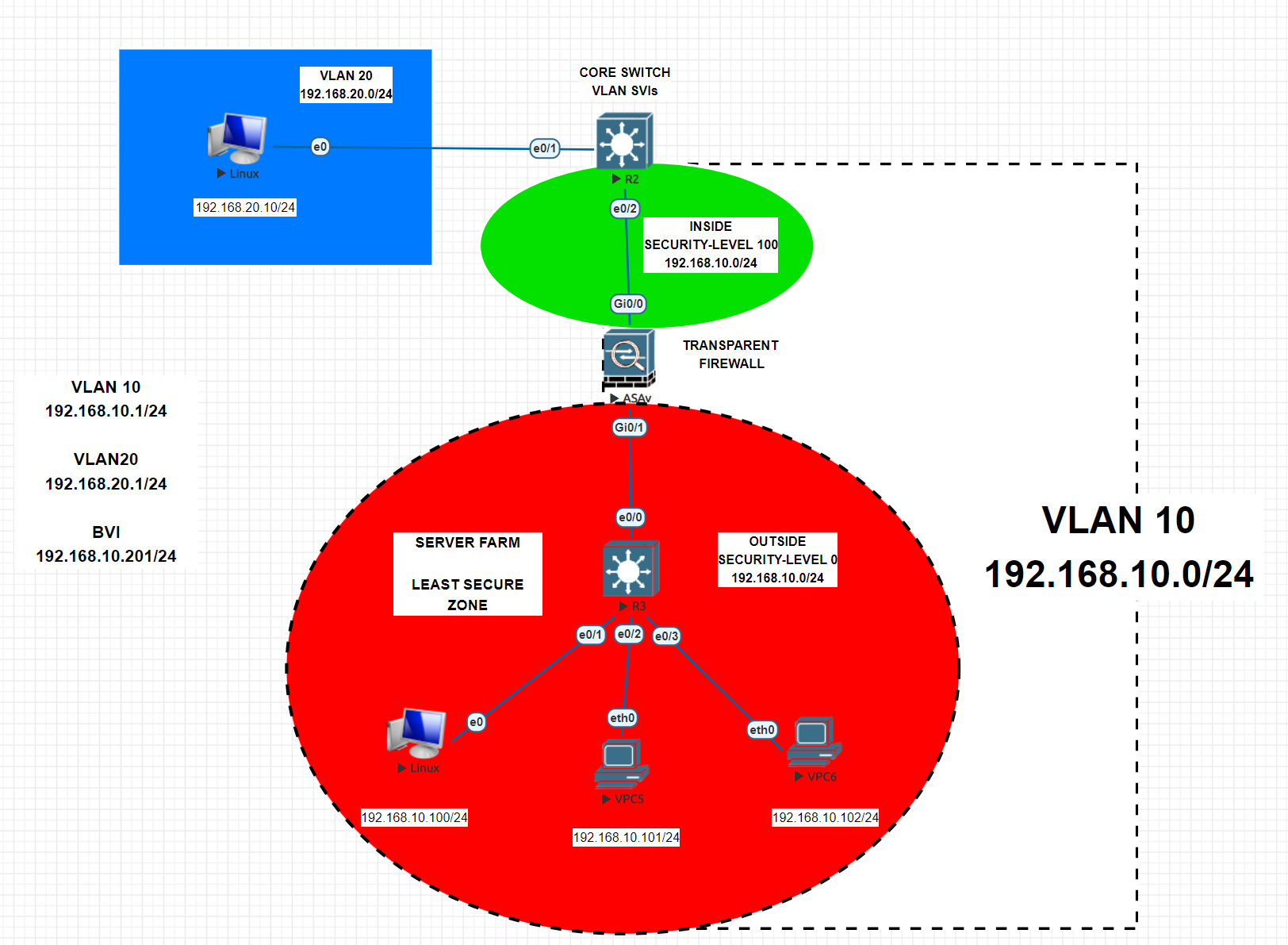
Cisco ASA Transparent Internal Firewall Configuration
Cisco ASA (Adaptive Security Appliance) is a security device that provides firewall, VPN, and other security services for networks. It can operate in multiple modes, including Routed Mode and Transparent Mode. Let’s focus on Cisco ASA Transparent Mode. In Transparent Mode, the Cisco ASA firewall is inserted into a network without requiring any IP address […]
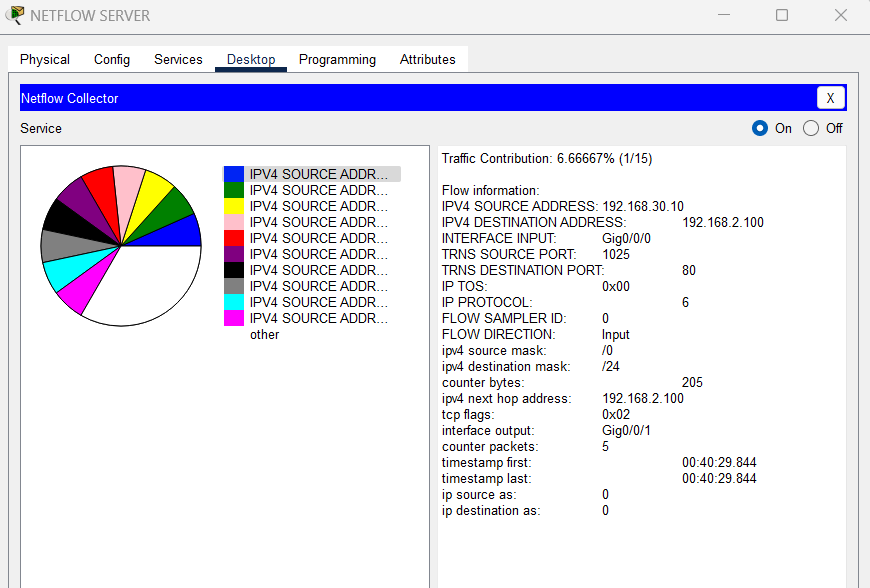
What is Netflow protocol? Deployment of Netflow server
NetFlow is a network protocol developed by Cisco that is used for network traffic monitoring and analysis. It allows network administrators to collect and view information about the traffic flowing through their network devices, such as routers and switches. A NetFlow server, sometimes referred to as a NetFlow collector or analyzer, is a system or […]
What is a DNS Server? How to setup on a network?
A DNS server, or Domain Name System server, is a crucial component of the internet infrastructure that helps translate human-readable domain names into IP addresses. Domain names are the familiar web addresses that people use to access websites, such as “www.barisyuksel.com.tr“. IP addresses, on the other hand, are numeric identifiers that computers and devices use […]
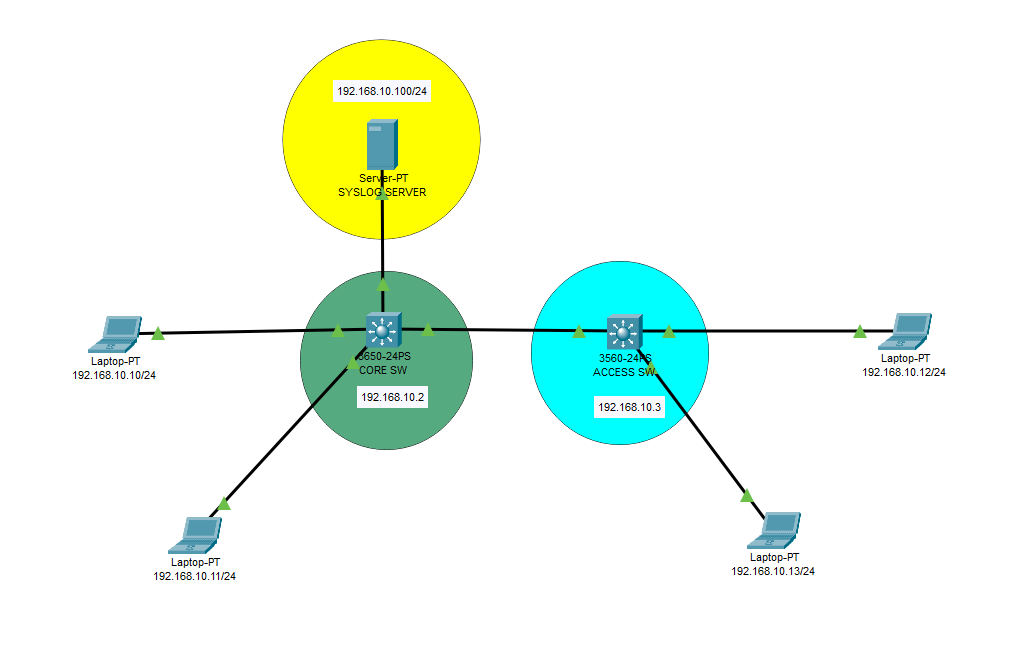
Syslog Server implementation for Cisco network devices
On Cisco networking devices, a syslog server refers to a system or application that collects, stores, and manages log messages generated by the Cisco devices. These log messages contain valuable information about the operation, performance, and events occurring on the network equipment. The syslog server helps network administrators and engineers to monitor, troubleshoot, and analyze […]
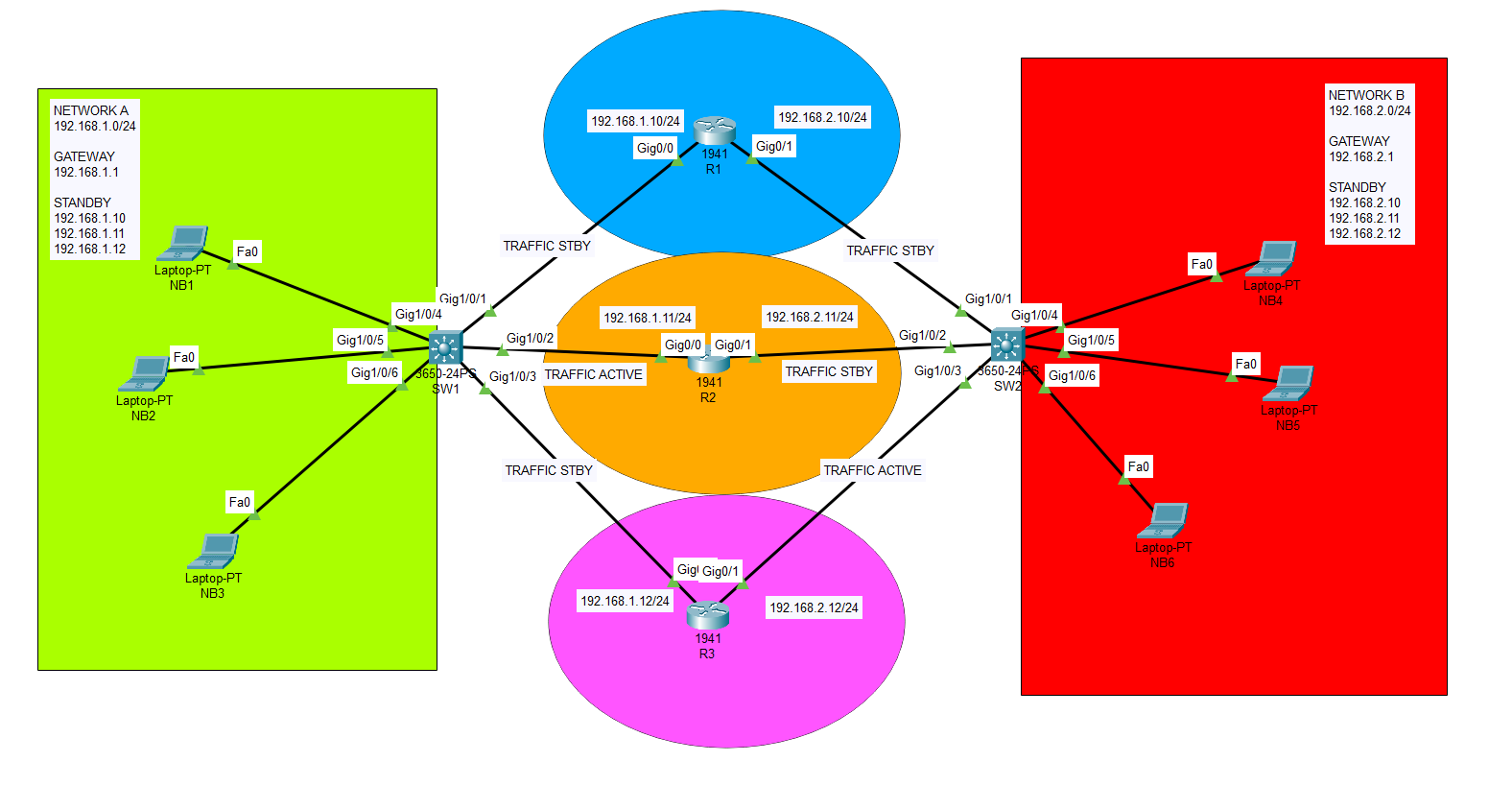
What is HSRP protocol? How to implement on the network?
HSRP, or the Hot Standby Router Protocol, is a Cisco proprietary protocol that enables two or more routers to work together in a group to present the illusion of a single virtual router to hosts on a LAN. The main purpose of HSRP is to establish network redundancy and avoid single points of failure, thus […]
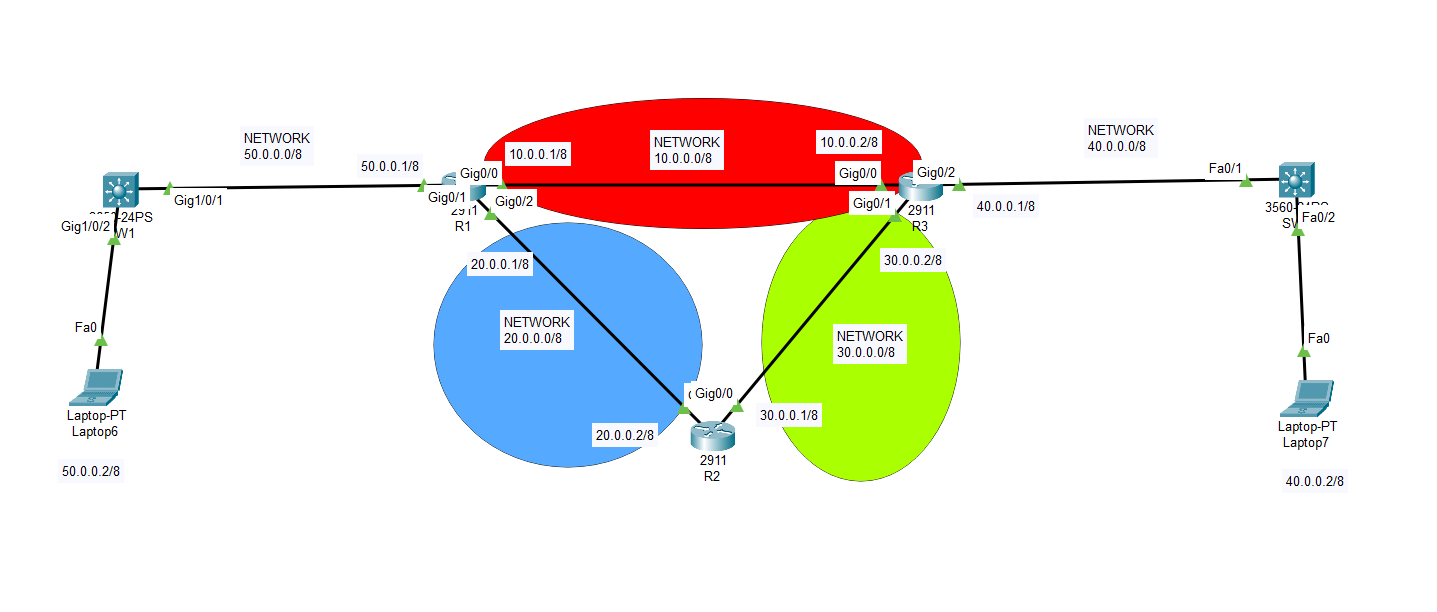
What is EIGRP Protocol? How to use EIGRP?
EIGRP, which stands for Enhanced Interior Gateway Routing Protocol, is a dynamic routing protocol used in computer networks to help routers exchange routing information efficiently. It was developed by Cisco Systems and is primarily designed for use in IP networks, including both local area networks (LANs) and wide area networks (WANs). EIGRP is an advanced […]
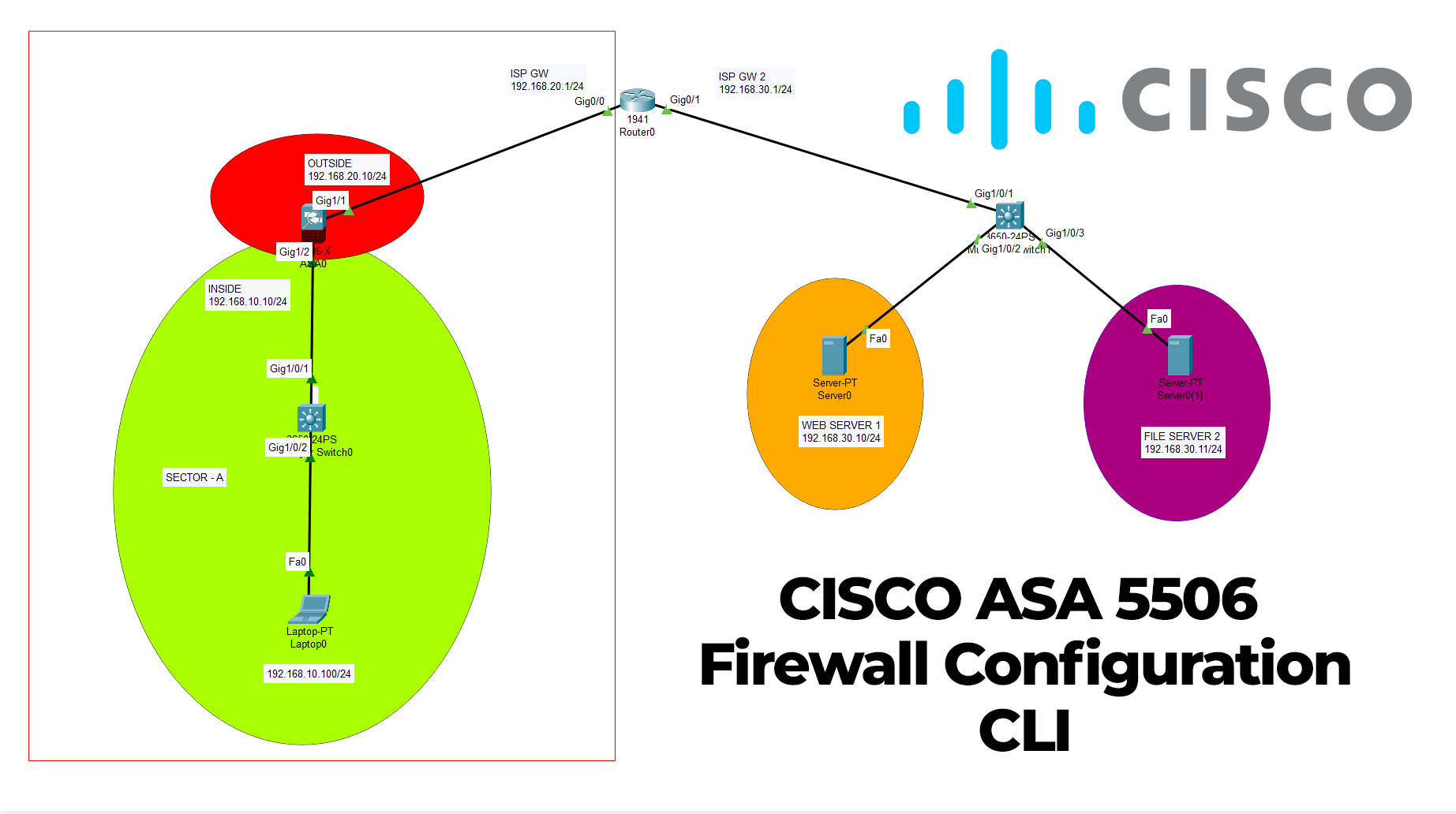
Cisco ASA 5506 firewall initial deployment with CLI
Cisco ASA (Adaptive Security Appliance) is a firewall and network security device produced by Cisco Systems. It provides advanced firewall, VPN (Virtual Private Network), and intrusion prevention capabilities to protect networks from unauthorized access, threats, and attacks. The Cisco ASA firewall offers both hardware and software components, including a dedicated security operating system called Cisco […]
What is a network port? Well known ports and registered ports.
A network port is a communication endpoint in a network. It is identified by a numerical value, called a port number, which helps direct network traffic to specific applications or services running on a device. Ports allow multiple applications to coexist on the same network device by assigning unique port numbers to each application. There […]
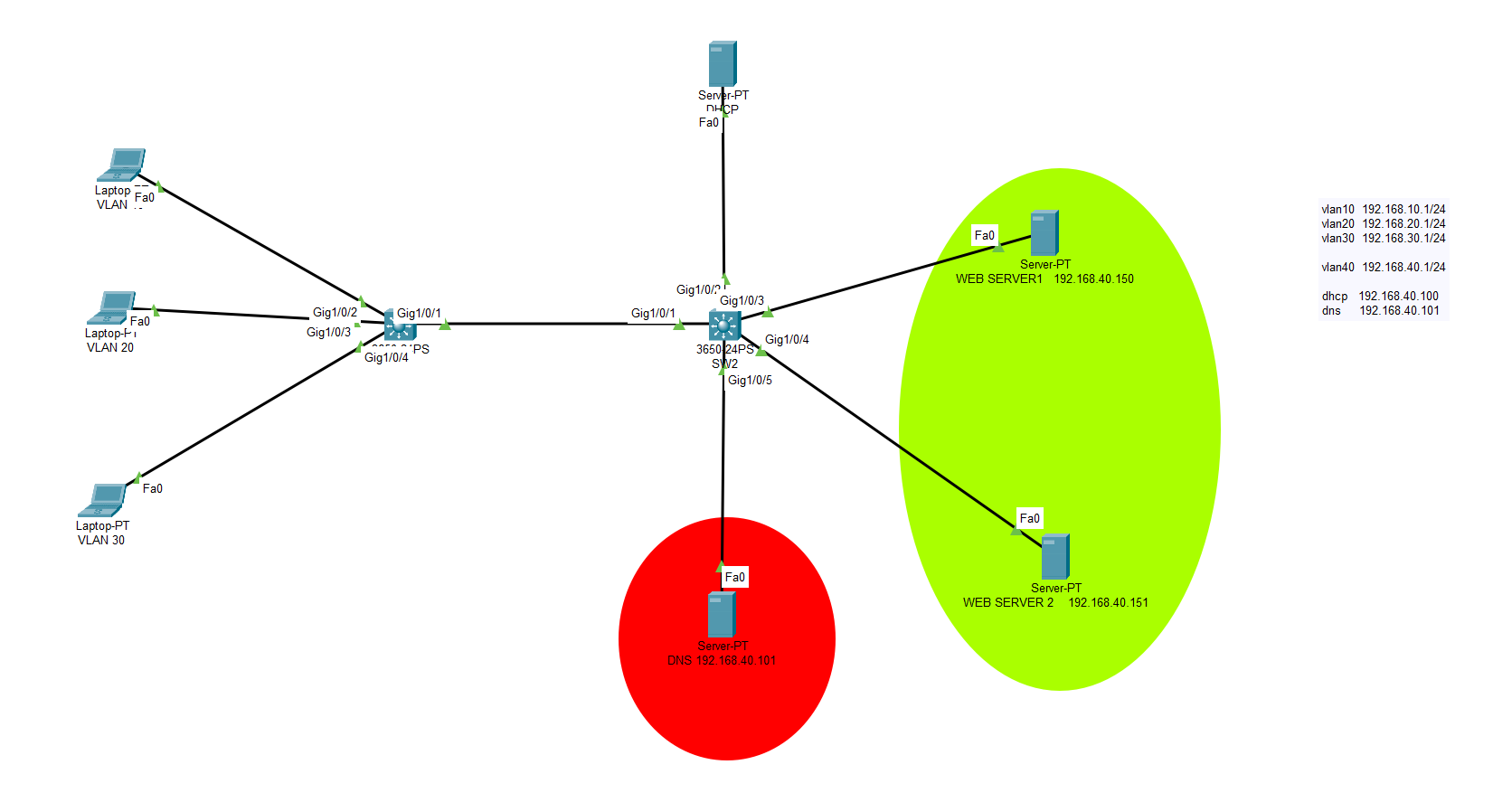
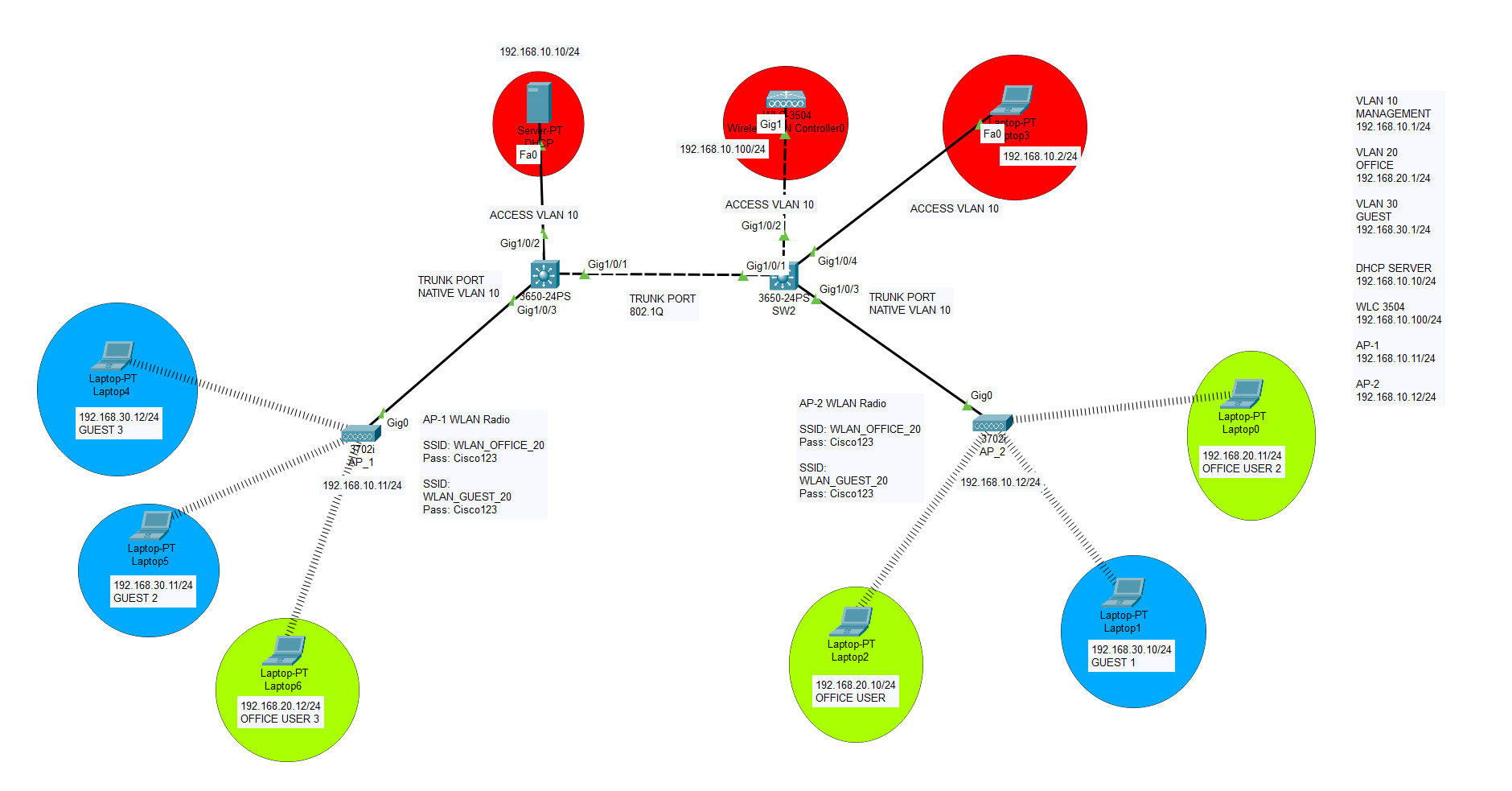
Cisco WLAN Controller with VLANs through multiple SSIDs
Let’s start configuring our VLANs and ports. We will create 3 VLANs on SW1 core switch. One of them will serve as Management subnet, others will serve as Office and Guest networks. Upon completion of VLAN and port configurations, we will start configuring Cisco Wireless Controllers and our Cisco Access Points. Both access points will […]