[Hacking Series/Lab 5] –How to use CAM table overflow for attack? (MAC flooding)
Disclaimer: These methods and techniques are purely for educational and informational purposes. All attacks were carried out in an offline isolated virtual environment. The use of these techniques in normal life is illegal and the responsibility lies strictly with the reader. DO NOT USE THESE TECHNIQUES IN REAL LIFE ! A CAM table attack, also […]
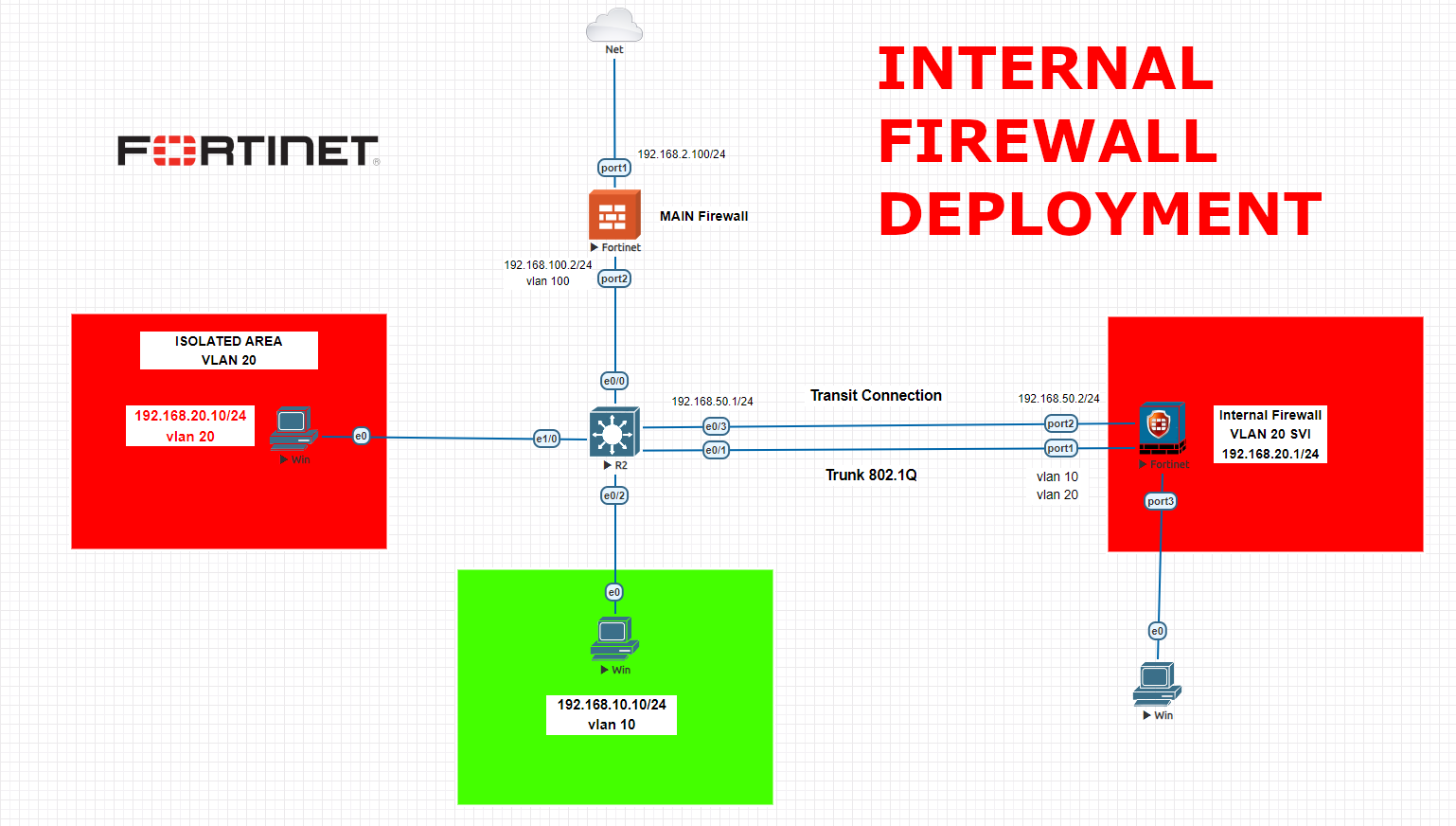
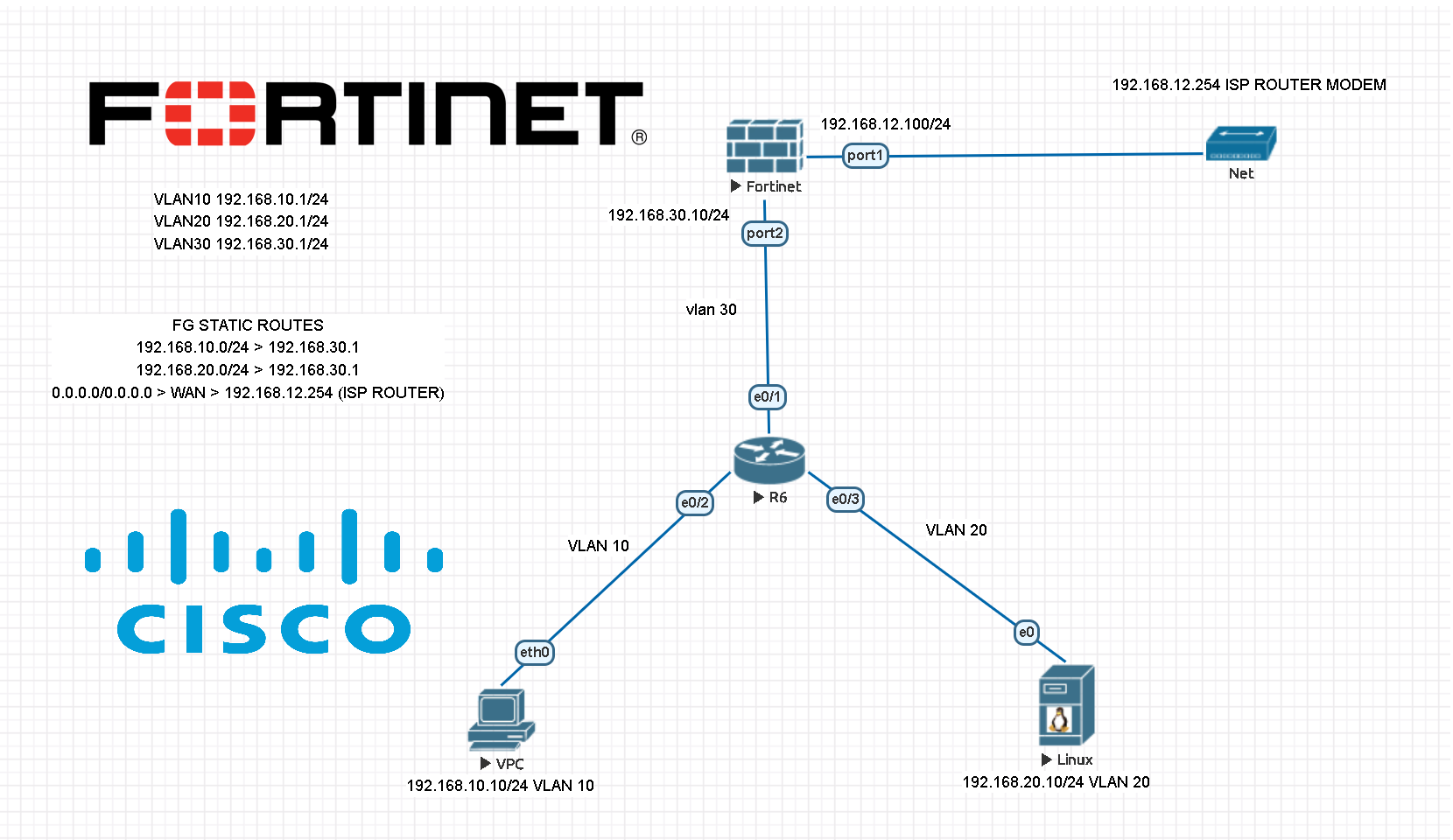
OT/IT Security – Internal Firewall Fortigate Implementation with configurations for your critical networks
An internal firewall, also known as an internal network firewall or a segment firewall, is a security system designed to protect and control traffic between different segments within an organization’s internal network. Unlike a perimeter firewall, which protects the network from external threats, an internal firewall focuses on securing the internal network by regulating the […]
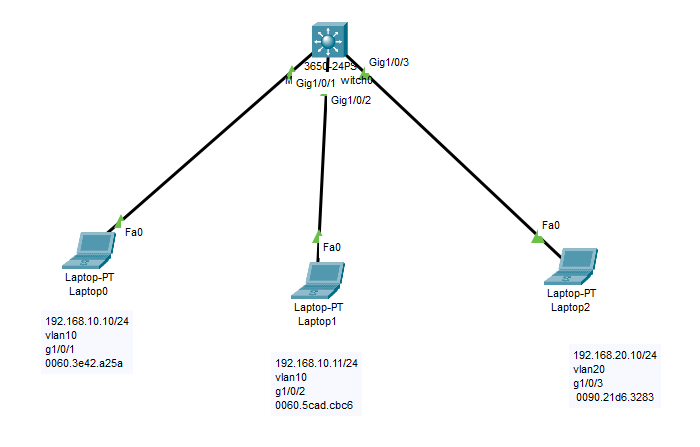
Ethernet MAC Port-security
Today we will implement port security on our Cisco switch. We will bind the MAC address of the NIC device with our related port. So if some changes happen on the physical ports, then new device will be restricted. CISCO SWITCH MAIN CONFIGURATION Switch>enable Switch#configure terminal Enter configuration commands, one per line. End with CNTL/Z. […]
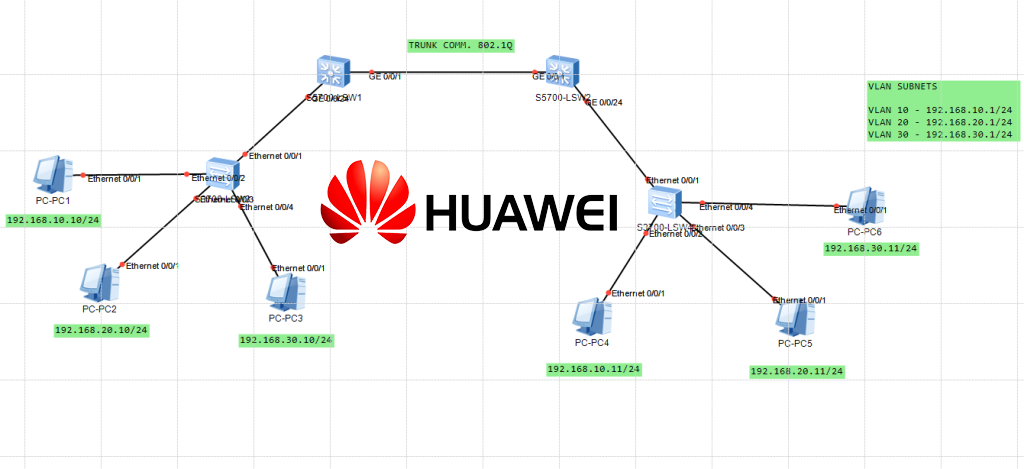
How to create VLANs on Huawei switches?
Huawei switches are network switches developed and produced by Huawei Technologies Co. Ltd., a leading global provider of information and communications technology (ICT) infrastructure and smart devices. Huawei switches offer a wide range of features and functionalities for both small and large-scale enterprise networks, including but not limited to: Huawei switches offer a robust and […]
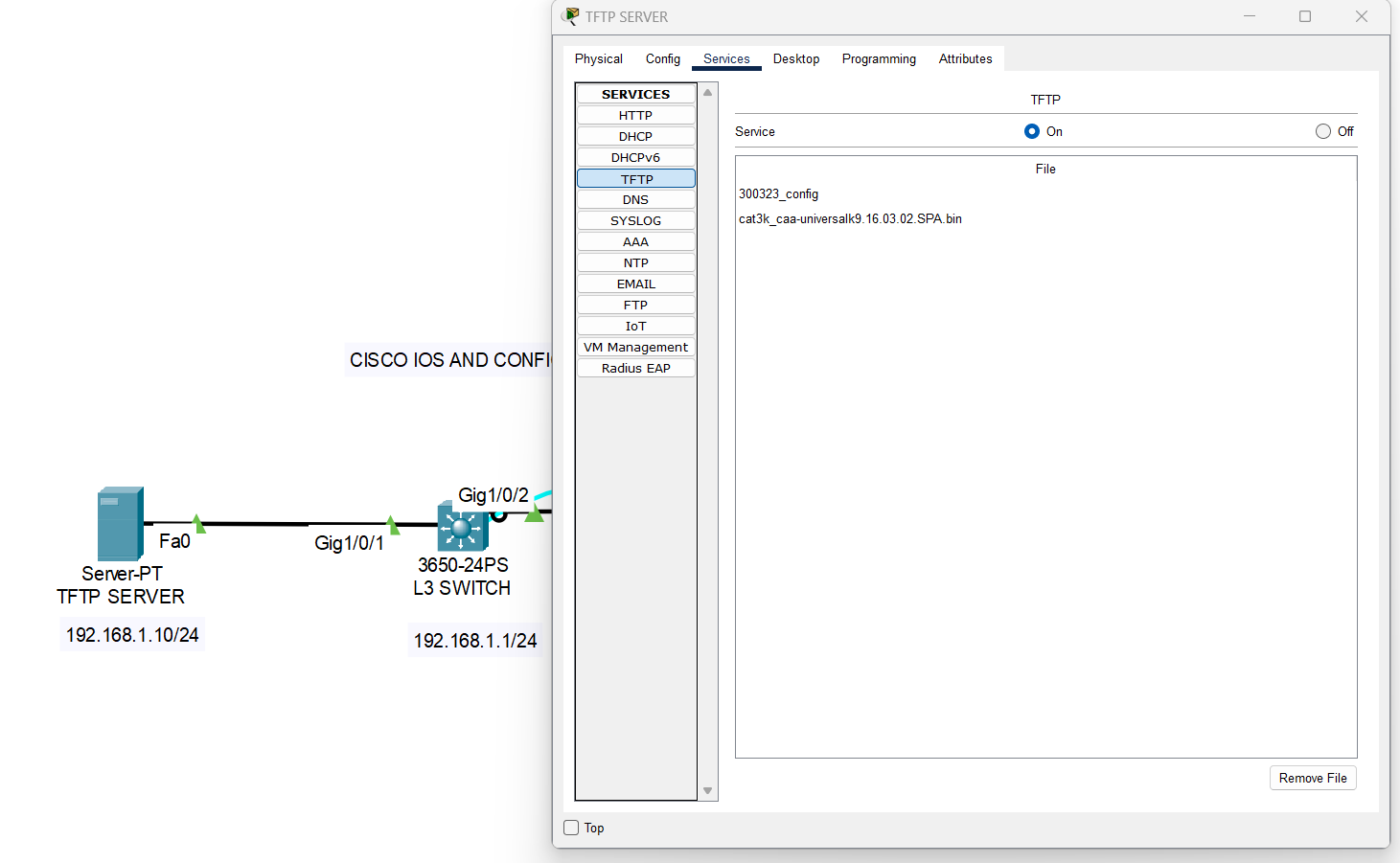
Cisco IOS and running-config backup to TFTP server
Backing up the Cisco IOS and running-config is extremely important for several reasons: To summarize, backing up the Cisco IOS and running-config is critical for ensuring network availability, performance, and security. It is a best practice that all network administrators should follow to avoid potential issues and minimize downtime. First create your TFTP server on […]
Cisco switch/router SSH configuration
Configuring a Cisco switch for SSH connection is an important task for network administrators. This process requires a good understanding of the Windows OS and network protocols such as TCP/IP, traceroute, etc. In this article, we will discuss the steps to configure a Cisco switch for SSH connection and how to troubleshoot any issues that […]
How to setup Fortigate firewall with Cisco core switches configured with VLANs?
Configuring a Fortigate Firewall is an important step for any network administrator. It not only ensures that the firewall is set up correctly, but also helps keep the network secure from any potential threats. In this article, we will discuss how to configure a Fortigate Firewall using CLI, from its first setup to more advanced […]
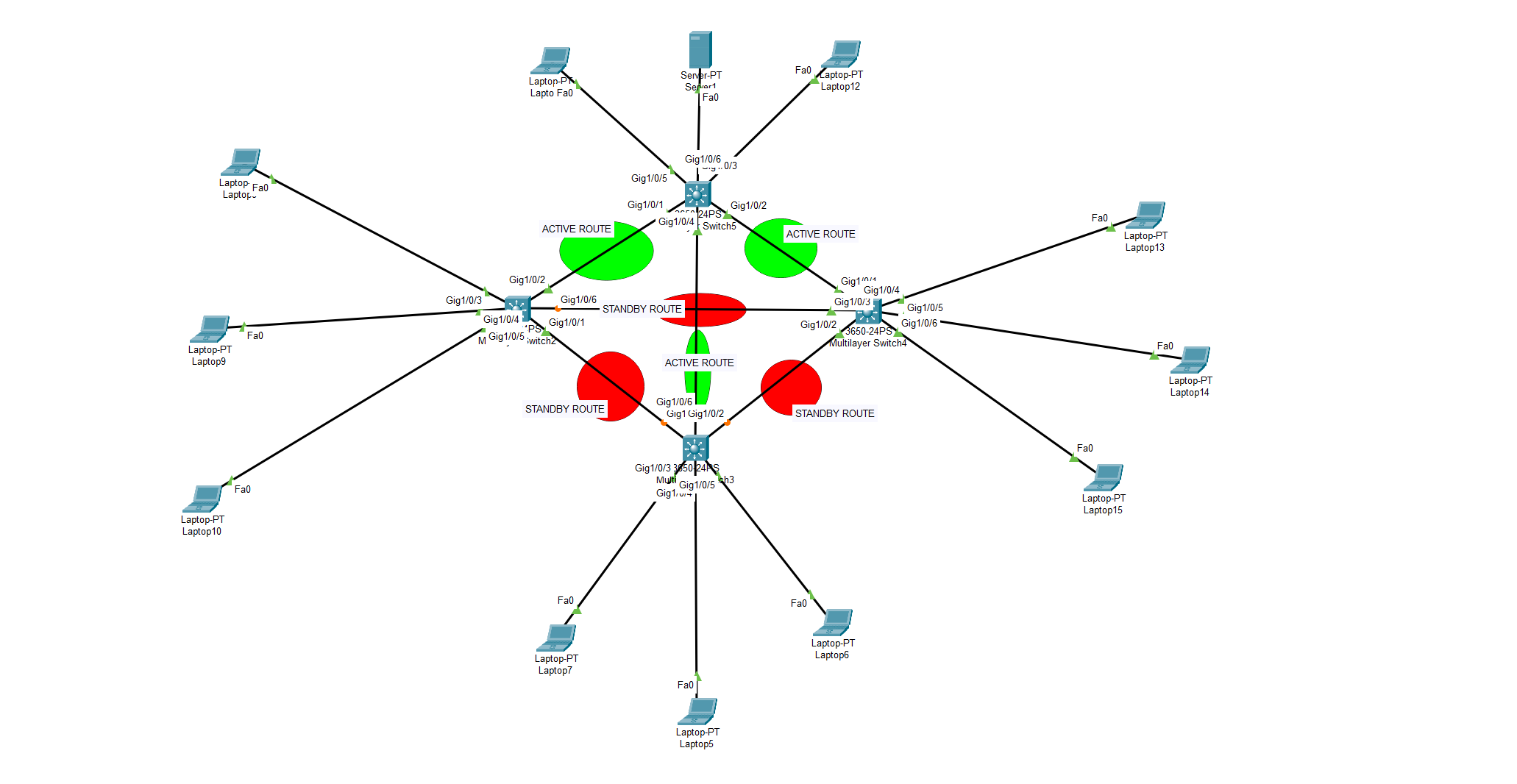
What is Spanning Tree Protocol? How to implement STP on multiple switch or router environment? How many STP modes are there?
Spanning Tree Protocol (STP) is a Layer 2 protocol used to prevent loops in the network by creating a logical topology of the network. It is used in Cisco IOS devices such as switches and routers to ensure redundant links are not creating broadcast storms and loops. STP works by assigning each switch or router […]
Initial/Basic configuration of Cisco Switches
Configuring Cisco switches is an essential part of any IT network. With the right configuration, you can ensure that your network is running optimally and securely. In this article, we will discuss how to configure a Cisco switch using the Cisco IOS command-line interface (CLI). We will cover topics such as setting up basic networking […]
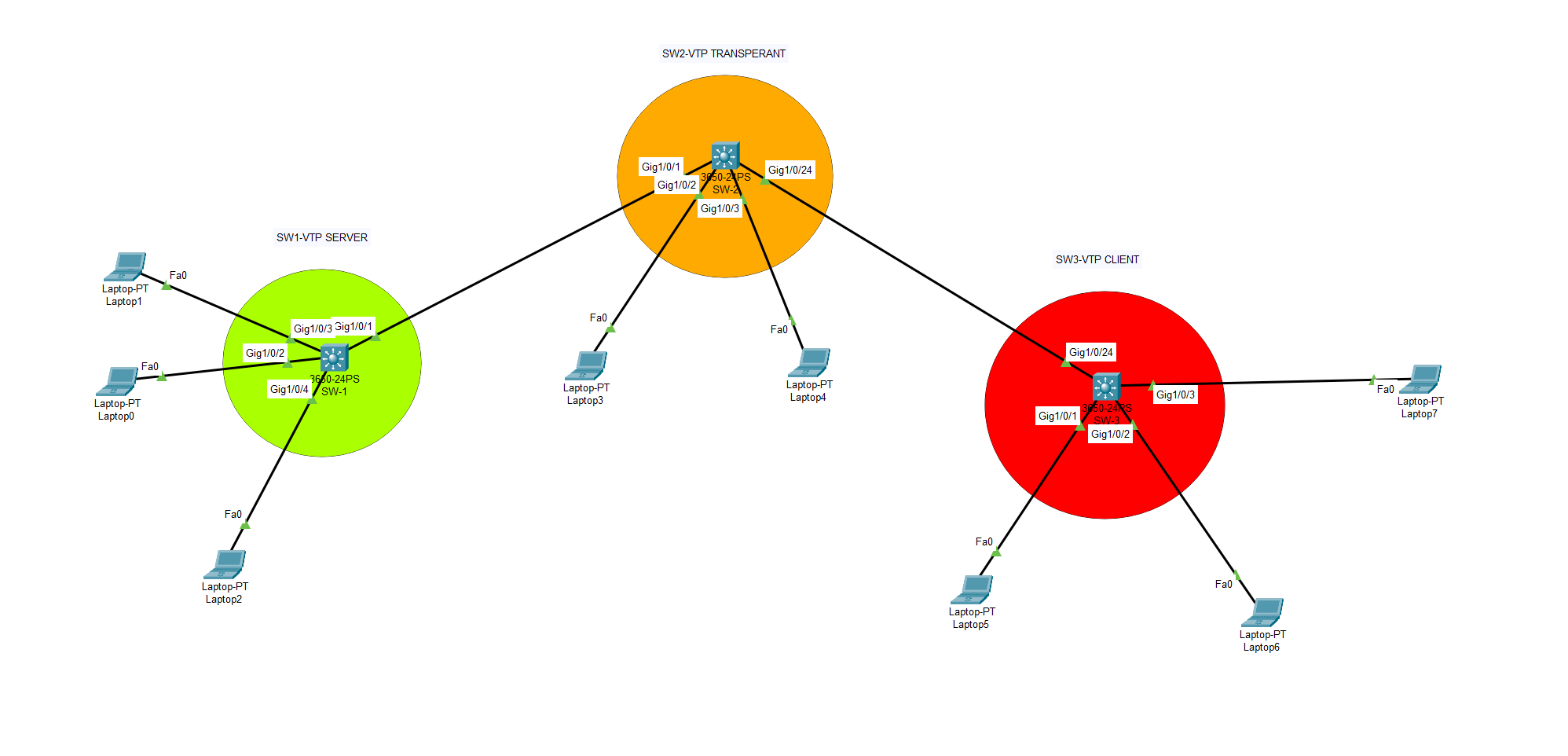
What is VTP (VLAN Trunking Protocol) ?
A VTP server is a switch to which other switches are connected. The VTP server maintains the VLAN database and propagates it to all the other switches. There are three modes in which a VTP server can operate: Server, Client and Transparent. The Server mode is used when there is more than one switch in […]
![[Hacking Series/Lab 5] –How to use CAM table overflow for attack? (MAC flooding)](https://barisyuksel.com.tr/wp-content/uploads/2024/08/macof_general1-966x653.png)