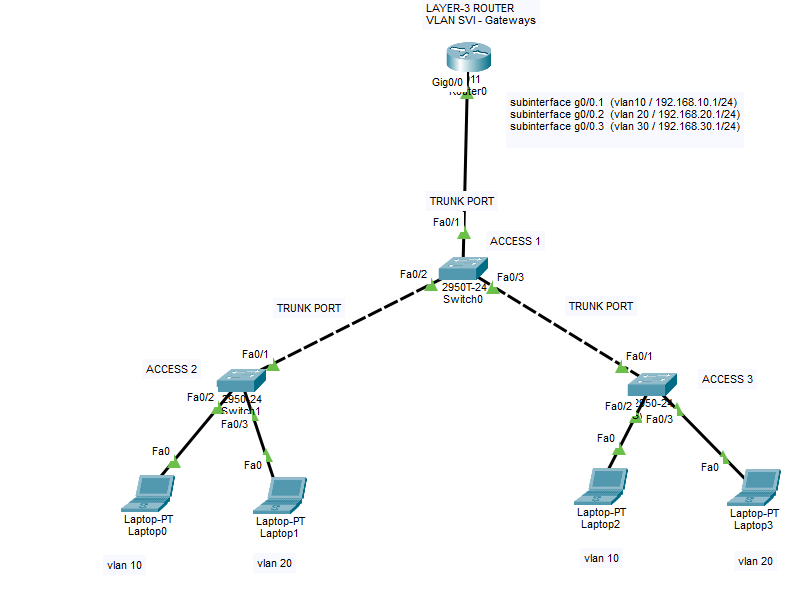
Router On A Stick Method for Layer 2 switches (ROAS Inter-vlan Legacy Communication) CISCO
In this lab, we will inspect how intervlan communication handled on Layer-3 Router with Router On a Stick model. If you have layer 2 switches for end devices, then you will need a layer 3 router or switch for intervlan communication. Layer 2 devices cannot do IP routing between VLAN gateways (SVIs) so therefore you […]
LACP (802.3ad) connection between Cisco Switch and Fortigate Firewall
LACP (Link Aggregation Control Protocol) is part of the IEEE 802.3ad standard that allows multiple physical Ethernet links to be combined into a single logical link, called a link aggregation group (LAG) or EtherChannel (in Cisco terms). Why do we need LACP? Increased Bandwidth: Combine several links for higher throughput. Redundancy: If one link fails, […]
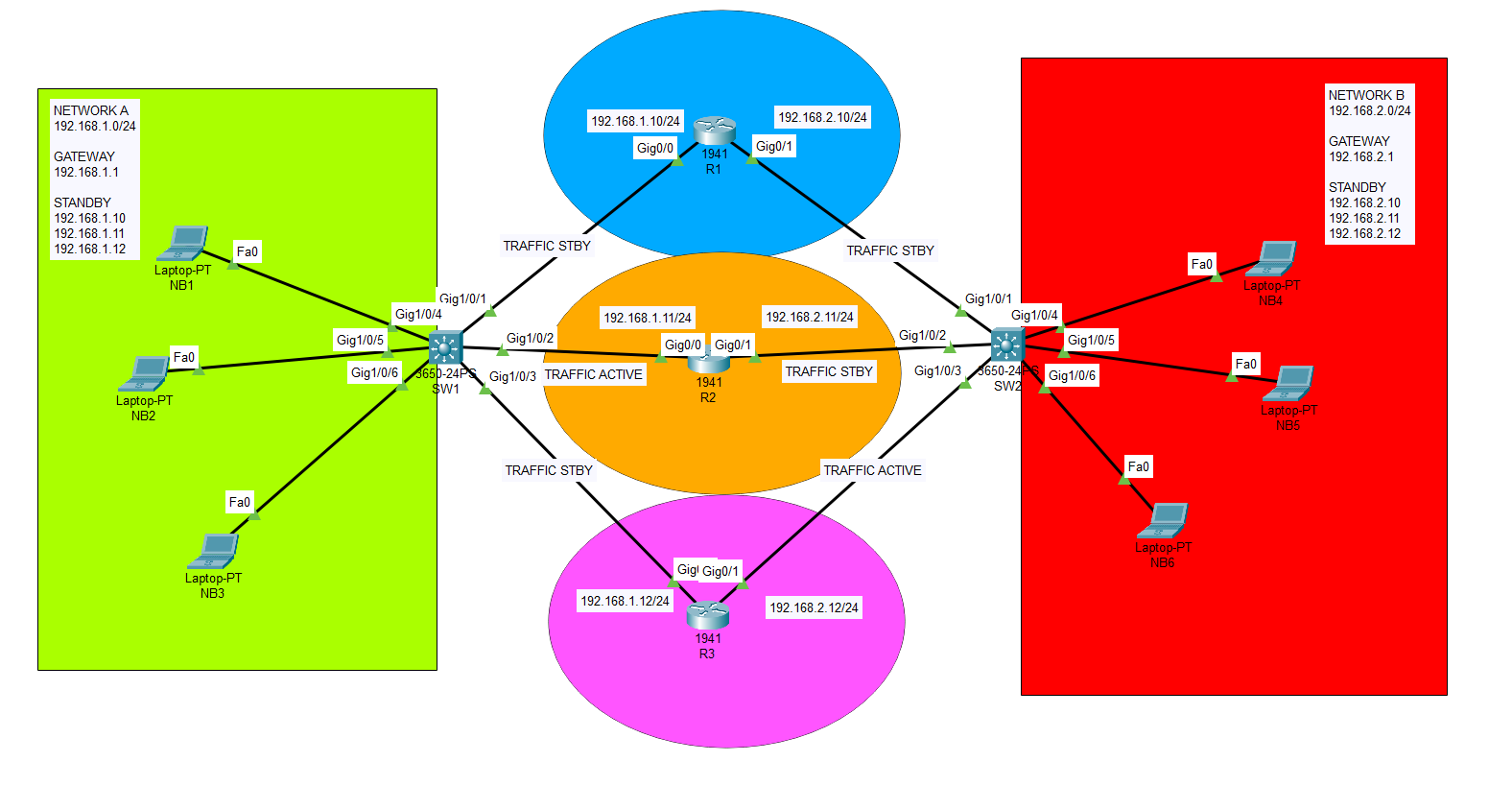
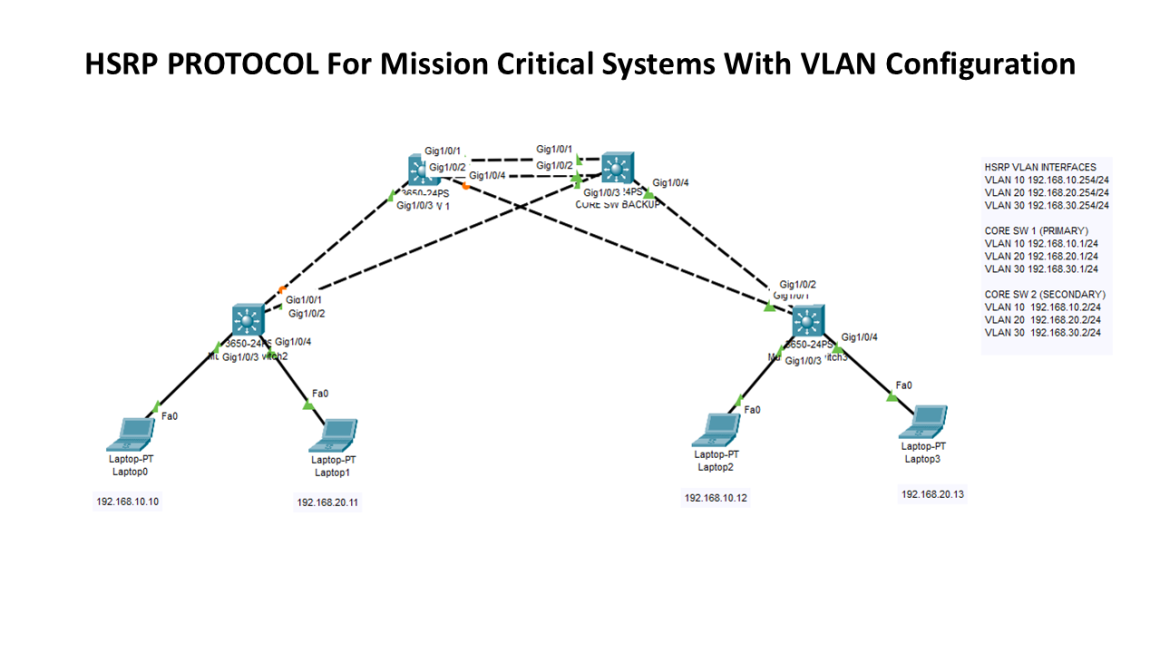
Mission Critical Systems L3 Core Switch HA
In this lab, we will use HSRP protocol to create high availability for our topology using two core switches as primary and secondary (backup) in case of a failure. By this way, we will avoid single point of failure and eliminate the system downtime. HSRP (Hot Standby Router Protocol) is a redundancy protocol developed by […]
[Hacking Series/Lab 4] –How to launch MAN IN THE MIDDLE Attack? (ARP poisoning)
Disclaimer: These methods and techniques are purely for educational and informational purposes. All attacks were carried out in an offline isolated virtual environment. The use of these techniques in normal life is illegal and the responsibility lies strictly with the reader. DO NOT USE THESE TECHNIQUES IN REAL LIFE ! ARP poisoning and Man-in-the-Middle (MITM) […]
[Hacking Series/Lab 3] –How to launch CDP (LLDP) Attack to a Cisco switch?
Disclaimer: These methods and techniques are purely for educational and informational purposes. All attacks were carried out in an offline isolated virtual environment. The use of these techniques in normal life is illegal and the responsibility lies strictly with the reader. DO NOT USE THESE TECHNIQUES IN REAL LIFE ! CDP Attack (Cisco Discovery Protocol) […]
[Hacking Series/Lab 1] – VLAN Hopping Attack ! This training was created for preventive defensive purposes.
Disclaimer: These methods and techniques are purely for educational and informational purposes. All attacks were carried out in an offline isolated virtual environment. The use of these techniques in normal life is illegal and the responsibility lies strictly with the reader. DO NOT USE THESE TECHNIQUES IN REAL LIFE ! In this training, I will […]
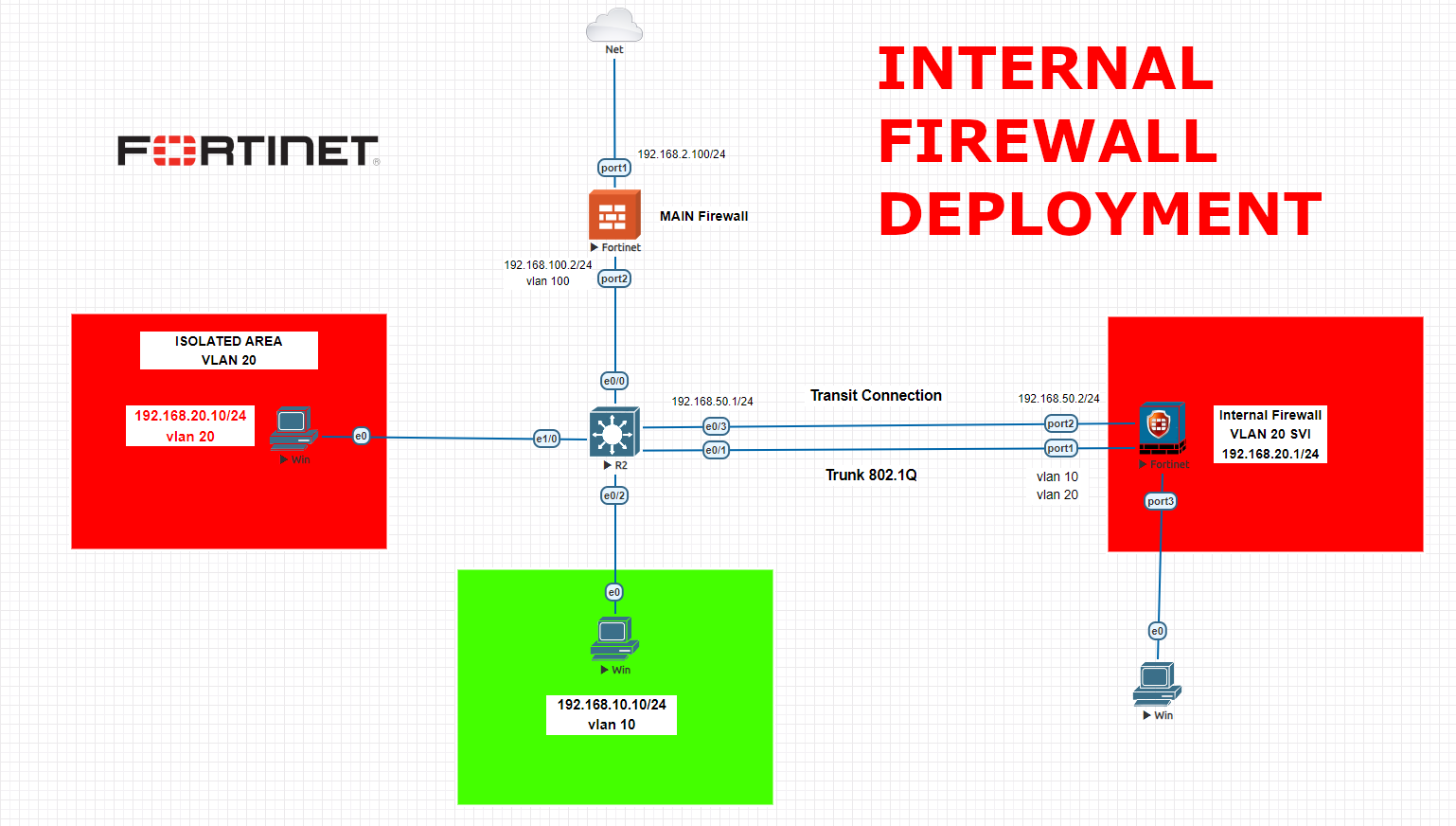
OT/IT Security – Internal Firewall Fortigate Implementation with configurations for your critical networks
An internal firewall, also known as an internal network firewall or a segment firewall, is a security system designed to protect and control traffic between different segments within an organization’s internal network. Unlike a perimeter firewall, which protects the network from external threats, an internal firewall focuses on securing the internal network by regulating the […]
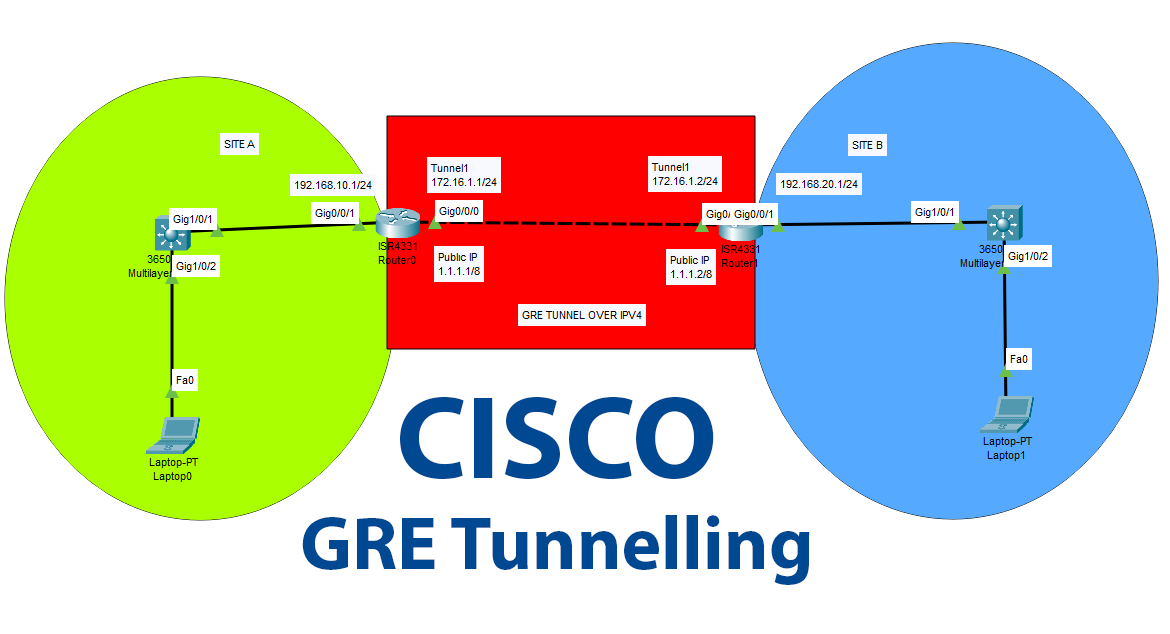
GRE Tunnels between multiple sites
A GRE (Generic Routing Encapsulation) tunnel in Cisco is a method of encapsulating and tunneling network traffic over an IP network. It allows the creation of a virtual point-to-point link between two endpoints, typically routers or switches, across an existing network infrastructure. Here’s how it works: GRE tunnels are often used for various purposes, such […]
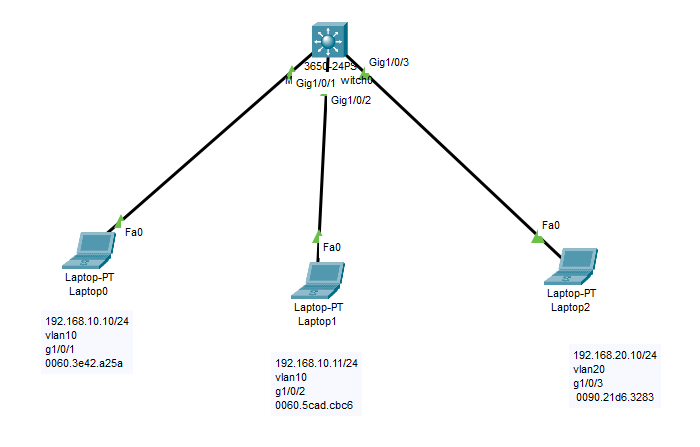
Ethernet MAC Port-security
Today we will implement port security on our Cisco switch. We will bind the MAC address of the NIC device with our related port. So if some changes happen on the physical ports, then new device will be restricted. CISCO SWITCH MAIN CONFIGURATION Switch>enable Switch#configure terminal Enter configuration commands, one per line. End with CNTL/Z. […]
What is HSRP protocol? How to implement on the network?
HSRP, or the Hot Standby Router Protocol, is a Cisco proprietary protocol that enables two or more routers to work together in a group to present the illusion of a single virtual router to hosts on a LAN. The main purpose of HSRP is to establish network redundancy and avoid single points of failure, thus […]

![[Hacking Series/Lab 4] –How to launch MAN IN THE MIDDLE Attack? (ARP poisoning)](https://barisyuksel.com.tr/wp-content/uploads/2024/08/mitm_diagram_topology-1035x653.png)
![[Hacking Series/Lab 3] –How to launch CDP (LLDP) Attack to a Cisco switch?](https://barisyuksel.com.tr/wp-content/uploads/2024/08/cdp_diagram.png)
![[Hacking Series/Lab 1] – VLAN Hopping Attack ! This training was created for preventive defensive purposes.](https://barisyuksel.com.tr/wp-content/uploads/2024/07/vlan-hopping-diagram2.png)