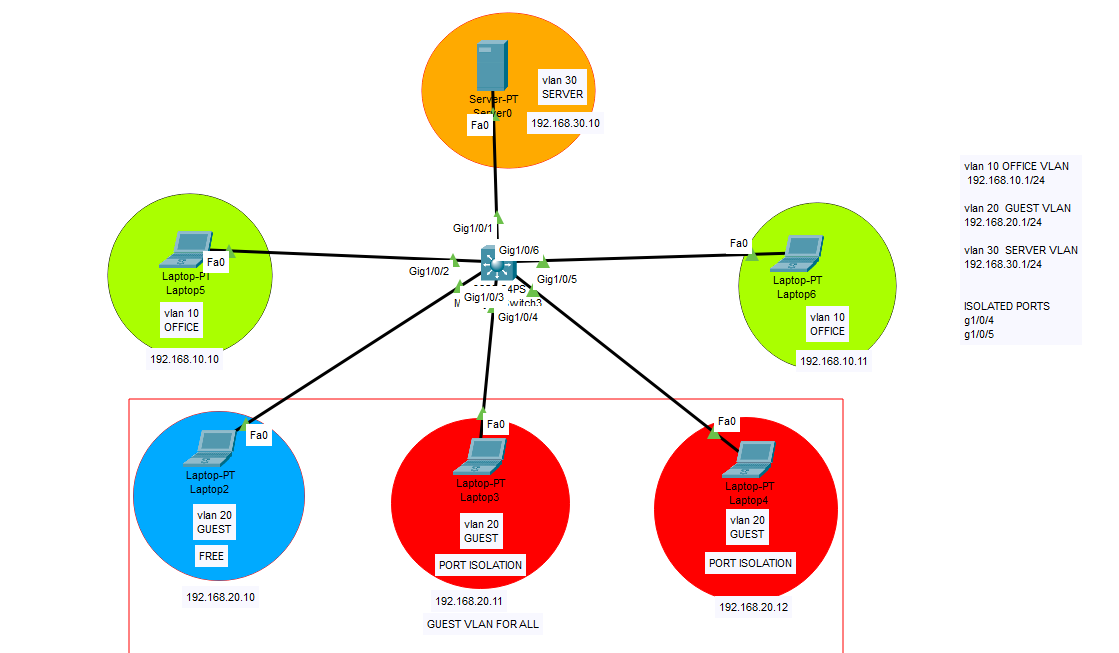
Port Isolation on VLAN subnets
This feature can be used to isolate devices in the same VLAN from each other while allowing them to access external resources (e.g., the internet, a router, or a server). It is often used in guest networks or environments where you don’t want devices in the same VLAN to communicate directly with each other. How […]
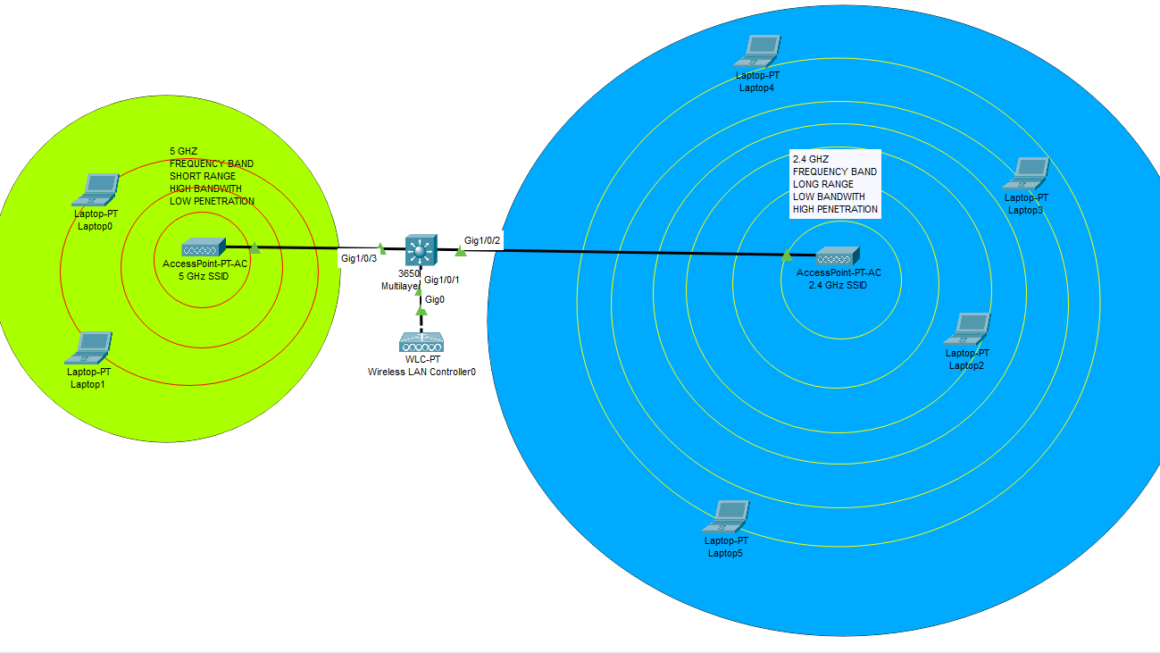
Difference between 2.4 Ghz and 5 Ghz frequency bands on Wifi communication
The 2.4 GHz and 5 GHz wireless networks are wireless communications wireless networks. Each is distinct in advantage and disadvantage depending on application. Feature 2.4 GHz 5 GHz Speed Slower (max ~600 Mbps, depending on Wi-Fi standard) Faster (up to several Gbps, depending on Wi-Fi standard) Range Longer range (penetrates walls and obstacles better) Shorter range (weaker penetration through walls) Interference More interference (crowded band with Bluetooth, microwaves, etc.) […]
Active Directory Installation on Windows Server 2019 [Step-by-step]
In this lab, we will install Active Directory role on Windows Server Data Center 2019 server. We will start with the basics, like installing the OS first then will continue to configure initial steps like setting IP address, disabling firewall and other things. This lab consists of 27 screenshots with explanations so follow all the […]
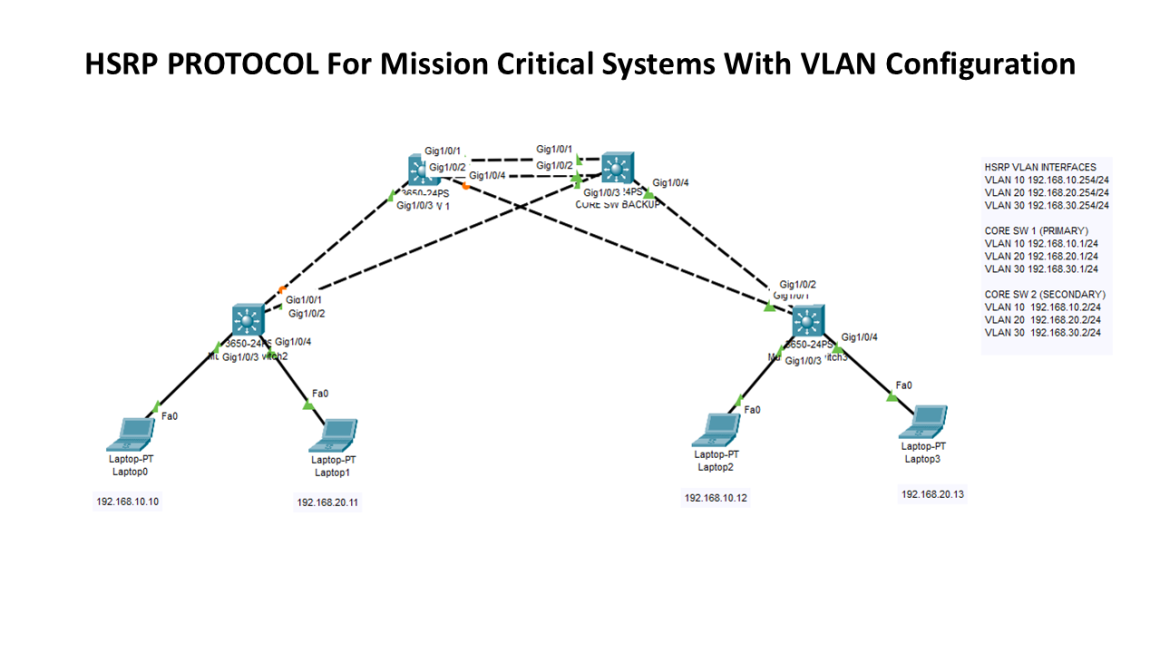
Mission Critical Systems L3 Core Switch HA
In this lab, we will use HSRP protocol to create high availability for our topology using two core switches as primary and secondary (backup) in case of a failure. By this way, we will avoid single point of failure and eliminate the system downtime. HSRP (Hot Standby Router Protocol) is a redundancy protocol developed by […]
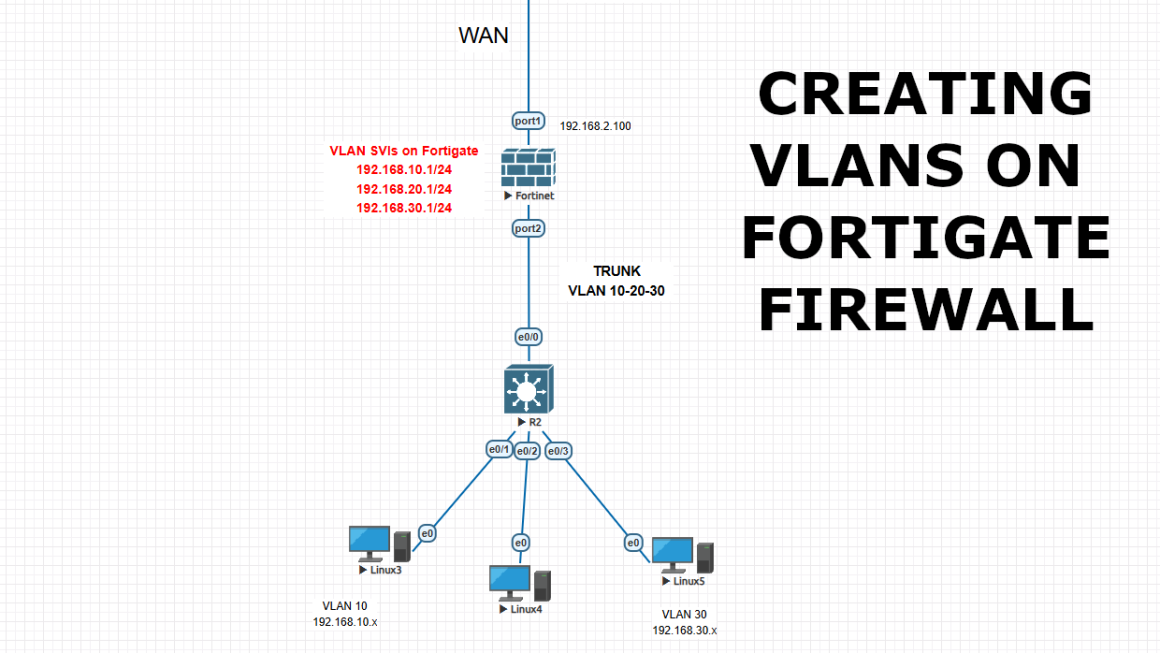
Creating VLANs on Fortigate and Cisco Core L3 switch connection
In this lab, I will show you how to create VLANs on Fortigate firewall instead of creating VLANs on Cisco L3 switch. You can also find the Cisco to Fortigate version in my posts. We will create 3 vlans as VLAN 10 – 192.168.10.1/24 , VLAN 20 – 192.168.20.1/24 , VLAN 30 – 192.168.30.1/24 and […]
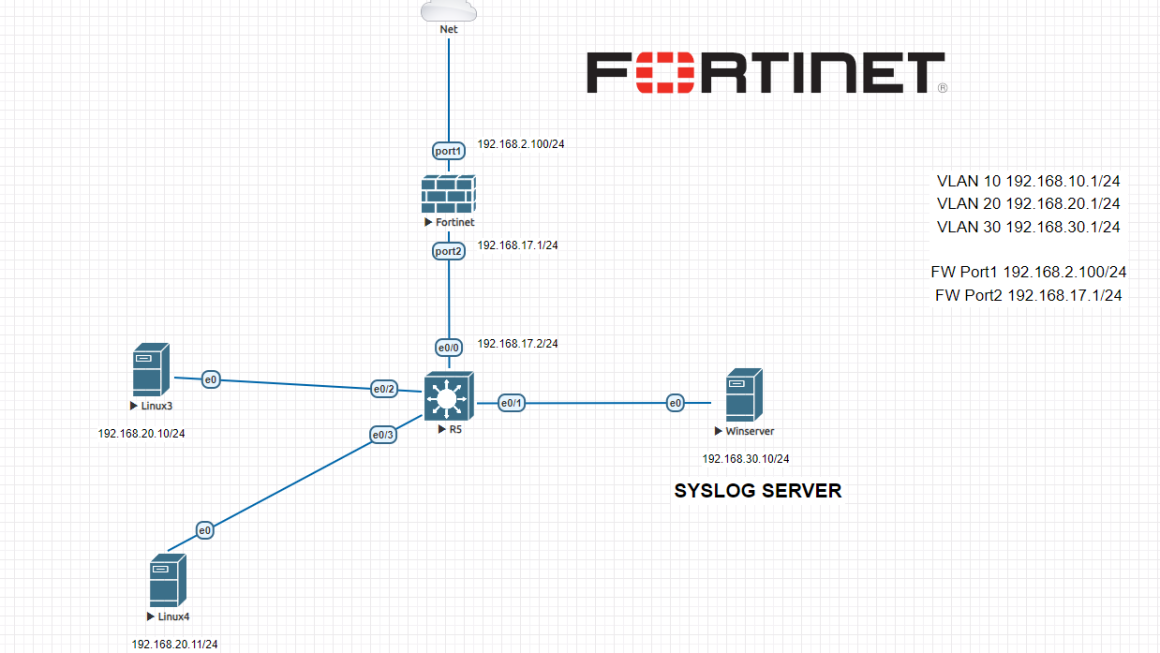
Syslog Integration With Fortigate Firewall
In this lab, we will configure Windows OS based Kiwi Syslog with Fortigate firewall. There are already some enterprise level solutions from Fortigate but this lab is prepared for those who wants to keep their external syslog server on Windows server. There are several syslog application, in this example we choose Kiwi syslog. Also you […]
[Hacking Series/Lab 5] –How to use CAM table overflow for attack? (MAC flooding)
Disclaimer: These methods and techniques are purely for educational and informational purposes. All attacks were carried out in an offline isolated virtual environment. The use of these techniques in normal life is illegal and the responsibility lies strictly with the reader. DO NOT USE THESE TECHNIQUES IN REAL LIFE ! A CAM table attack, also […]
[Hacking Series/Lab 4] –How to launch MAN IN THE MIDDLE Attack? (ARP poisoning)
Disclaimer: These methods and techniques are purely for educational and informational purposes. All attacks were carried out in an offline isolated virtual environment. The use of these techniques in normal life is illegal and the responsibility lies strictly with the reader. DO NOT USE THESE TECHNIQUES IN REAL LIFE ! ARP poisoning and Man-in-the-Middle (MITM) […]
[Hacking Series/Lab 3] –How to launch CDP (LLDP) Attack to a Cisco switch?
Disclaimer: These methods and techniques are purely for educational and informational purposes. All attacks were carried out in an offline isolated virtual environment. The use of these techniques in normal life is illegal and the responsibility lies strictly with the reader. DO NOT USE THESE TECHNIQUES IN REAL LIFE ! CDP Attack (Cisco Discovery Protocol) […]
[Hacking Series/Lab 2] – SNMP Attack ! This training was created for preventive defensive purposes.
Disclaimer: These methods and techniques are purely for educational and informational purposes. All attacks were carried out in an offline isolated virtual environment. The use of these techniques in normal life is illegal and the responsibility lies strictly with the reader. DO NOT USE THESE TECHNIQUES IN REAL LIFE ! An SNMP (Simple Network Management […]
![Active Directory Installation on Windows Server 2019 [Step-by-step]](https://barisyuksel.com.tr/wp-content/uploads/2025/01/active-directory-post-general-e1738016588858-966x653.png)
![[Hacking Series/Lab 5] –How to use CAM table overflow for attack? (MAC flooding)](https://barisyuksel.com.tr/wp-content/uploads/2024/08/macof_general1-966x653.png)
![[Hacking Series/Lab 4] –How to launch MAN IN THE MIDDLE Attack? (ARP poisoning)](https://barisyuksel.com.tr/wp-content/uploads/2024/08/mitm_diagram_topology-1035x653.png)
![[Hacking Series/Lab 3] –How to launch CDP (LLDP) Attack to a Cisco switch?](https://barisyuksel.com.tr/wp-content/uploads/2024/08/cdp_diagram.png)
![[Hacking Series/Lab 2] – SNMP Attack ! This training was created for preventive defensive purposes.](https://barisyuksel.com.tr/wp-content/uploads/2024/07/snmp_attack_diagram1.png)