[Hacking Series/Lab 5] –How to use CAM table overflow for attack? (MAC flooding)
Disclaimer: These methods and techniques are purely for educational and informational purposes. All attacks were carried out in an offline isolated virtual environment. The use of these techniques in normal life is illegal and the responsibility lies strictly with the reader. DO NOT USE THESE TECHNIQUES IN REAL LIFE ! A CAM table attack, also […]
[Hacking Series/Lab 4] –How to launch MAN IN THE MIDDLE Attack? (ARP poisoning)
Disclaimer: These methods and techniques are purely for educational and informational purposes. All attacks were carried out in an offline isolated virtual environment. The use of these techniques in normal life is illegal and the responsibility lies strictly with the reader. DO NOT USE THESE TECHNIQUES IN REAL LIFE ! ARP poisoning and Man-in-the-Middle (MITM) […]
[Hacking Series/Lab 3] –How to launch CDP (LLDP) Attack to a Cisco switch?
Disclaimer: These methods and techniques are purely for educational and informational purposes. All attacks were carried out in an offline isolated virtual environment. The use of these techniques in normal life is illegal and the responsibility lies strictly with the reader. DO NOT USE THESE TECHNIQUES IN REAL LIFE ! CDP Attack (Cisco Discovery Protocol) […]
[Hacking Series/Lab 2] – SNMP Attack ! This training was created for preventive defensive purposes.
Disclaimer: These methods and techniques are purely for educational and informational purposes. All attacks were carried out in an offline isolated virtual environment. The use of these techniques in normal life is illegal and the responsibility lies strictly with the reader. DO NOT USE THESE TECHNIQUES IN REAL LIFE ! An SNMP (Simple Network Management […]
[Hacking Series/Lab 1] – VLAN Hopping Attack ! This training was created for preventive defensive purposes.
Disclaimer: These methods and techniques are purely for educational and informational purposes. All attacks were carried out in an offline isolated virtual environment. The use of these techniques in normal life is illegal and the responsibility lies strictly with the reader. DO NOT USE THESE TECHNIQUES IN REAL LIFE ! In this training, I will […]
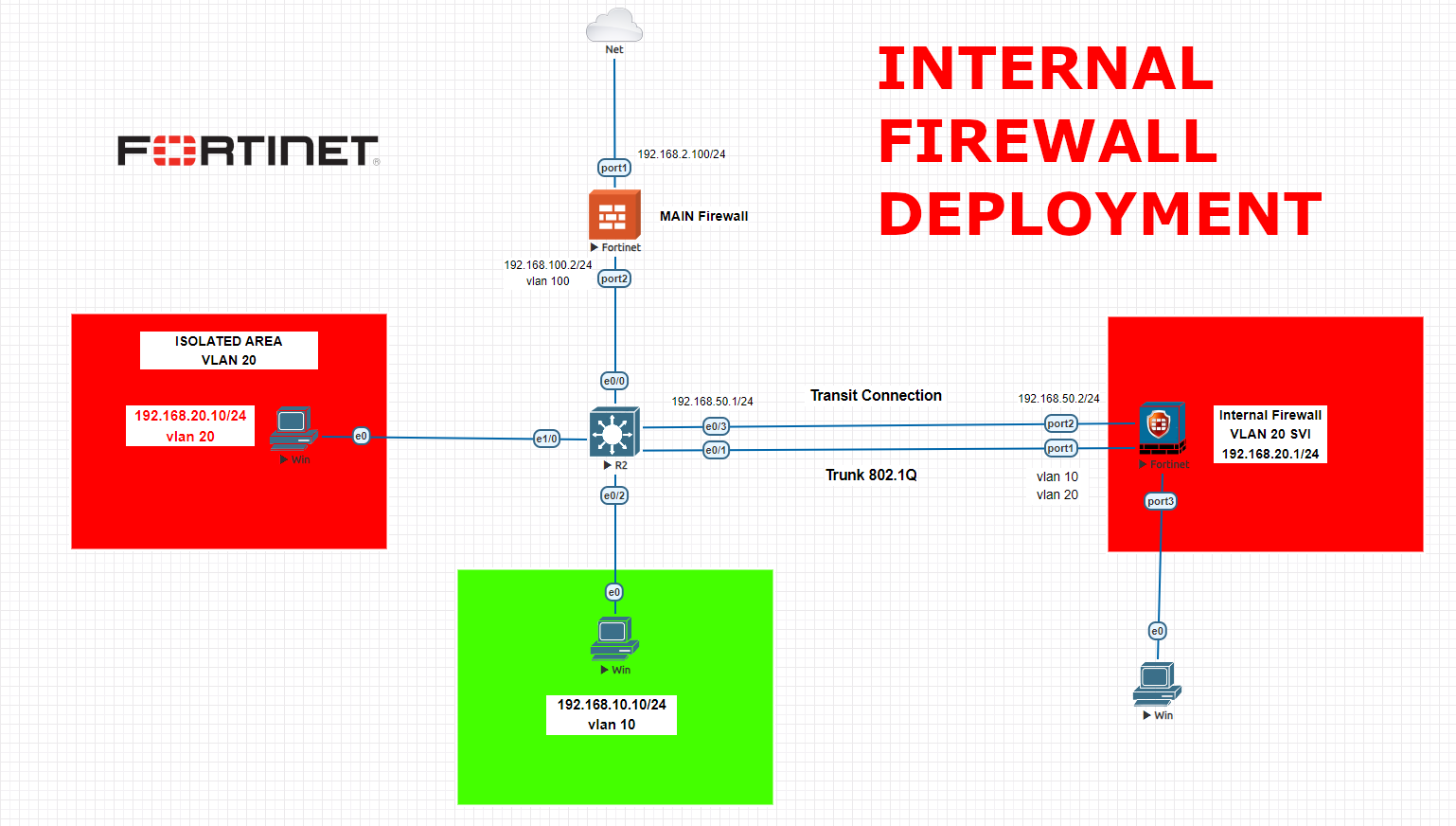
OT/IT Security – Internal Firewall Fortigate Implementation with configurations for your critical networks
An internal firewall, also known as an internal network firewall or a segment firewall, is a security system designed to protect and control traffic between different segments within an organization’s internal network. Unlike a perimeter firewall, which protects the network from external threats, an internal firewall focuses on securing the internal network by regulating the […]
Extended ACL list for enterprise network system. Download
In this simulation you can find all necessary configuration. You can download .pkt Cisco Package Tracer file and open it on your computer. There are 5 VLAN configured and 1 extended ACL implemented on whole VLANs. Basically, hit CLI tab on the switch which you want to check then enter “show running-configuration” command to see […]
![[Hacking Series/Lab 5] –How to use CAM table overflow for attack? (MAC flooding)](https://barisyuksel.com.tr/wp-content/uploads/2024/08/macof_general1-966x653.png)
![[Hacking Series/Lab 4] –How to launch MAN IN THE MIDDLE Attack? (ARP poisoning)](https://barisyuksel.com.tr/wp-content/uploads/2024/08/mitm_diagram_topology-1035x653.png)
![[Hacking Series/Lab 3] –How to launch CDP (LLDP) Attack to a Cisco switch?](https://barisyuksel.com.tr/wp-content/uploads/2024/08/cdp_diagram.png)
![[Hacking Series/Lab 2] – SNMP Attack ! This training was created for preventive defensive purposes.](https://barisyuksel.com.tr/wp-content/uploads/2024/07/snmp_attack_diagram1.png)
![[Hacking Series/Lab 1] – VLAN Hopping Attack ! This training was created for preventive defensive purposes.](https://barisyuksel.com.tr/wp-content/uploads/2024/07/vlan-hopping-diagram2.png)