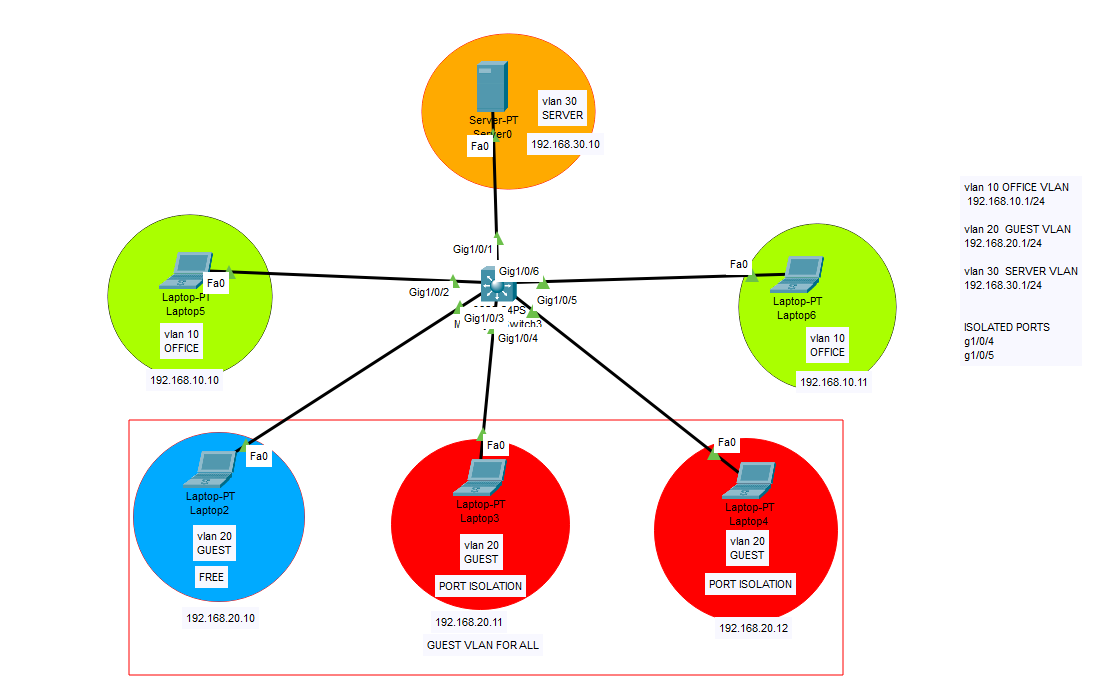
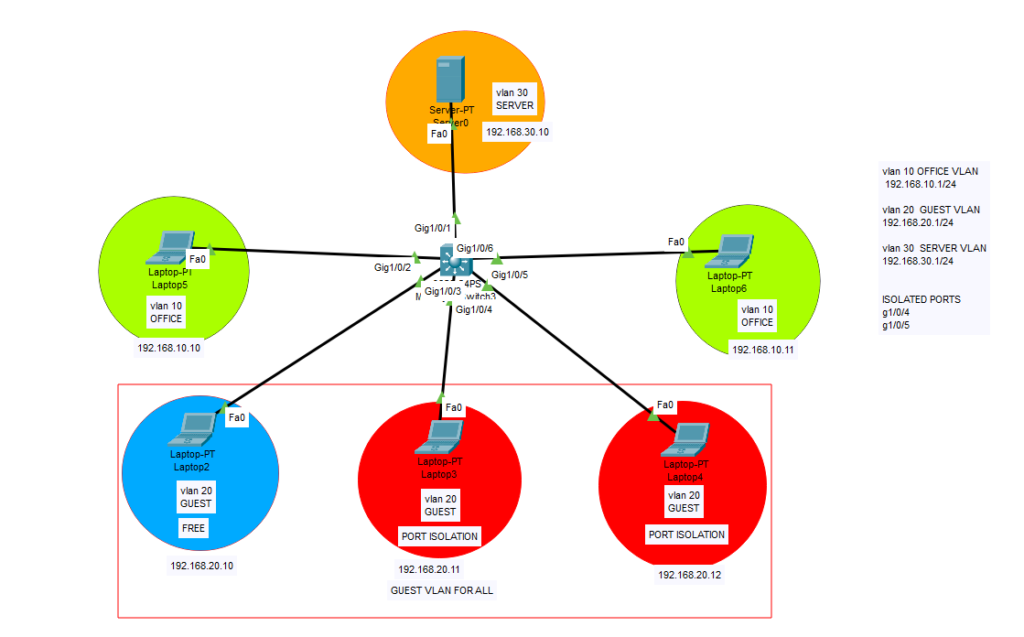
This feature can be used to isolate devices in the same VLAN from each other while allowing them to access external resources (e.g., the internet, a router, or a server). It is often used in guest networks or environments where you don’t want devices in the same VLAN to communicate directly with each other.
How It Works:
- When port isolation is enabled on a VLAN, devices on isolated ports will not be able to communicate with each other, but they can still communicate with the promiscuous port (usually the router or gateway).
- The promiscuous port can communicate with all devices, but the isolated ports cannot communicate with each other.
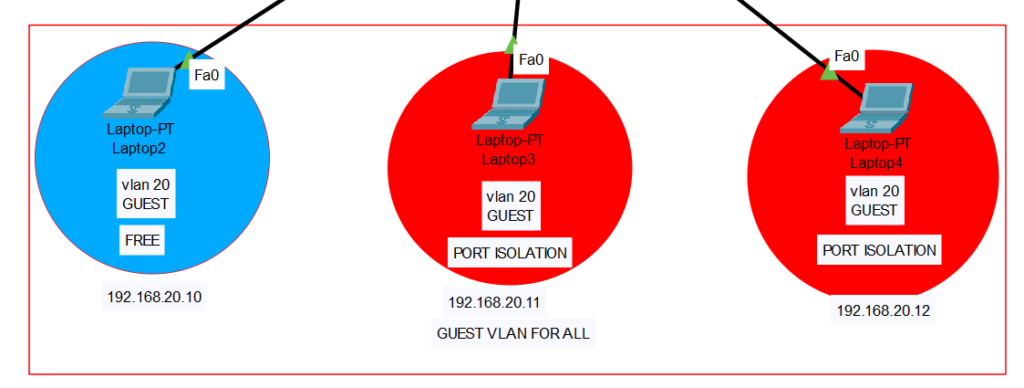
In this lab, we have 3 different VLANs. VLAN 10 as office, VLAN 20 as guest, VLAN 30 as server. On our example, we dont want 2 guest clients to communicate with each other in the same vlan (same subnet) so we use “switchport protected” command to disable them to communicate with other clients in Guest vlan. But they can communicate with other VLAN clients. Normally I would use this command for all Guest vlan ports, but wanted to show you that it can be specific to some dedicated ports as well. So after the configuration, our 2 clients 192.168.20.11 and 192.168.20.12 on dedicated ports, cannot communicate with each other clients in same subnet but they can reach to other vlan clients.
Switch Configuration
Switch>en
Switch#show run
Building configuration…
Current configuration : 2038 bytes
!
version 16.3.2
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname Switch
!
no ip cef
ip routing
!
no ipv6 cef
spanning-tree mode pvst
!
!
interface GigabitEthernet1/0/1
switchport access vlan 30
switchport mode access
!
interface GigabitEthernet1/0/2
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/0/3
switchport access vlan 20
switchport mode access
!
interface GigabitEthernet1/0/4
switchport access vlan 20
switchport mode access
switchport protected
!
interface GigabitEthernet1/0/5
switchport access vlan 20
switchport mode access
switchport protected
!
interface GigabitEthernet1/0/6
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/0/7
!
interface GigabitEthernet1/0/8
!
interface GigabitEthernet1/0/9
!
interface GigabitEthernet1/0/10
!
interface GigabitEthernet1/0/11
!
interface GigabitEthernet1/0/12
!
interface GigabitEthernet1/0/13
!
interface GigabitEthernet1/0/14
!
interface GigabitEthernet1/0/15
!
interface GigabitEthernet1/0/16
!
interface GigabitEthernet1/0/17
!
interface GigabitEthernet1/0/18
!
interface GigabitEthernet1/0/19
!
interface GigabitEthernet1/0/20
!
interface GigabitEthernet1/0/21
!
interface GigabitEthernet1/0/22
!
interface GigabitEthernet1/0/23
!
interface GigabitEthernet1/0/24
!
interface GigabitEthernet1/1/1
!
interface GigabitEthernet1/1/2
!
interface GigabitEthernet1/1/3
!
interface GigabitEthernet1/1/4
!
interface Vlan1
no ip address
shutdown
!
interface Vlan10
description OFFICE VLAN
mac-address 0001.428a.4e01
ip address 192.168.10.1 255.255.255.0
!
interface Vlan20
description GUEST VLAN
mac-address 0001.428a.4e02
ip address 192.168.20.1 255.255.255.0
!
interface Vlan30
description SERVER VLAN
mac-address 0001.428a.4e03
ip address 192.168.30.1 255.255.255.0
!
ip classless
!
ip flow-export version 9
!
line con 0
line aux 0
!
line vty 0 4
login
end
Switch#
Happy networking,
If you have any further questions feel free to contact with me.