In this lab, we will configure Windows OS based Kiwi Syslog with Fortigate firewall. There are already some enterprise level solutions from Fortigate but this lab is prepared for those who wants to keep their external syslog server on Windows server. There are several syslog application, in this example we choose Kiwi syslog. Also you can do the same integration with Linux based OS app Rsyslog.
In default, you wont be able to see your forward traffic logs and local traffic logs due to default log settings on Fortigate. Therefore you need to change your log settings both from IPV4 policy itself and from the console with few commands. We will set log severity to “information” also will enable local traffic if it is needed. Otherwise you cannot see any logs on the left log section. Then we will send the logs out of Fortigate to Syslog.
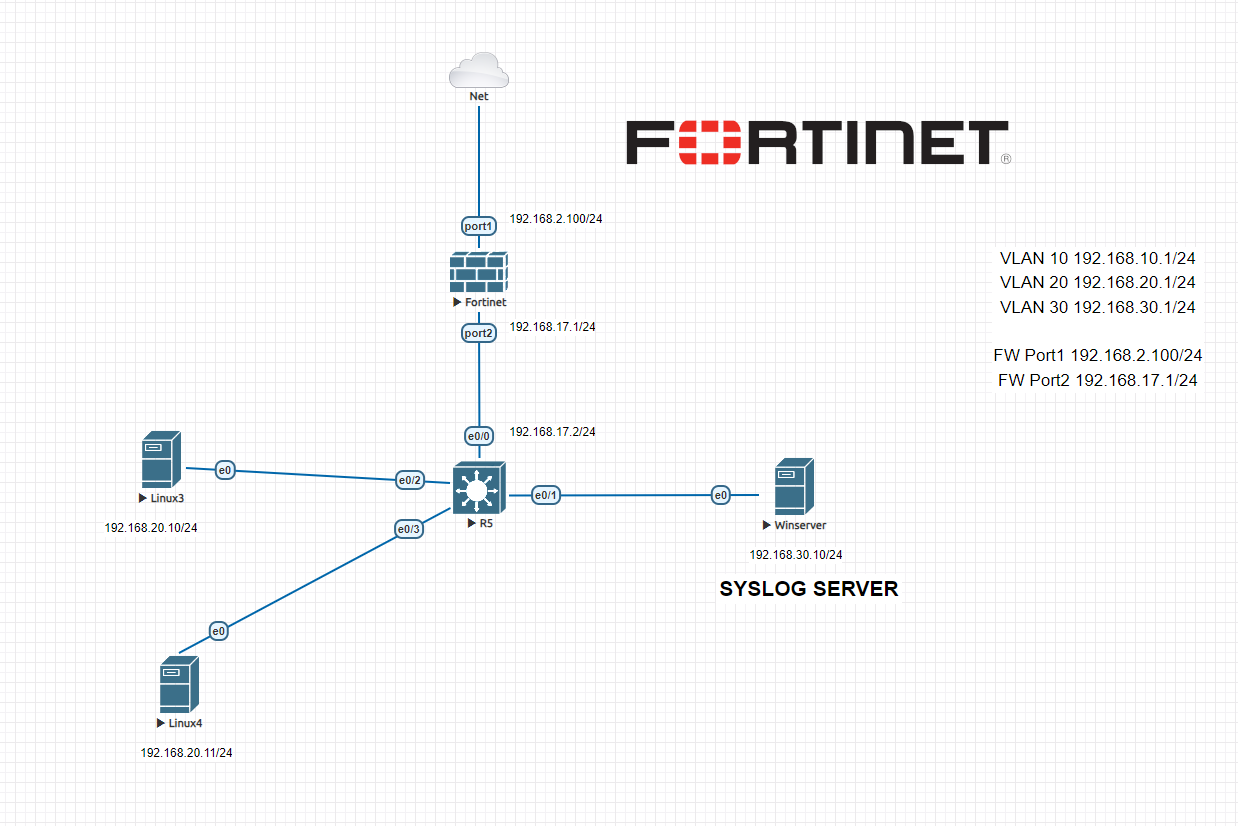
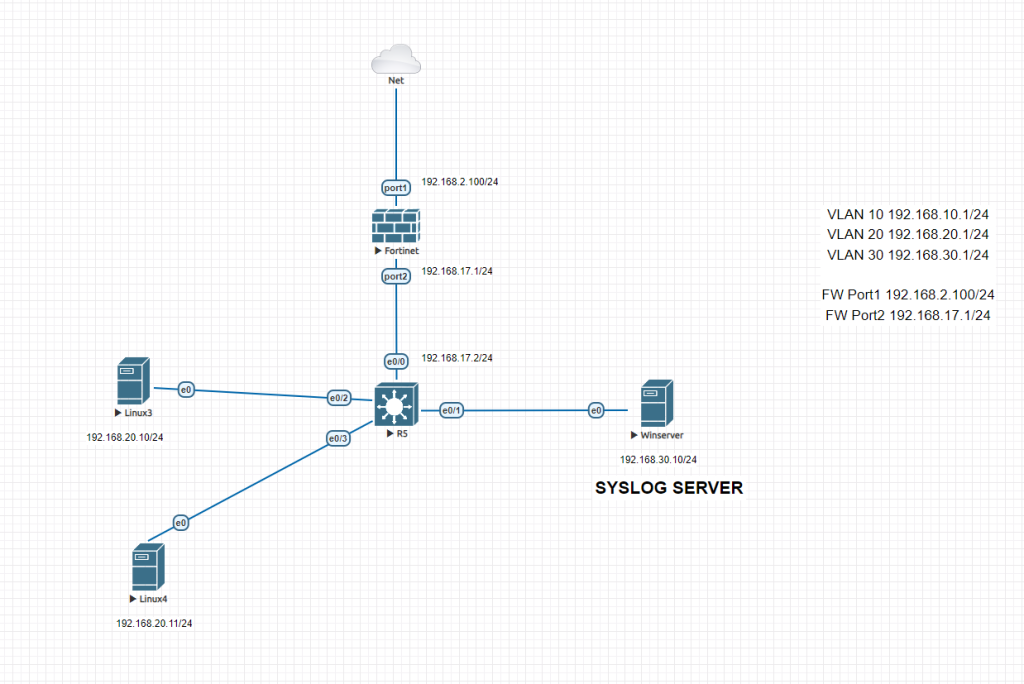
TOPOLOGY
LOG SETTINGS ON FORTIGATE FIREWALL
Step 1
This policy may vary to your settings. On this example I have only 1 policy for internet access from LAN to WAN.
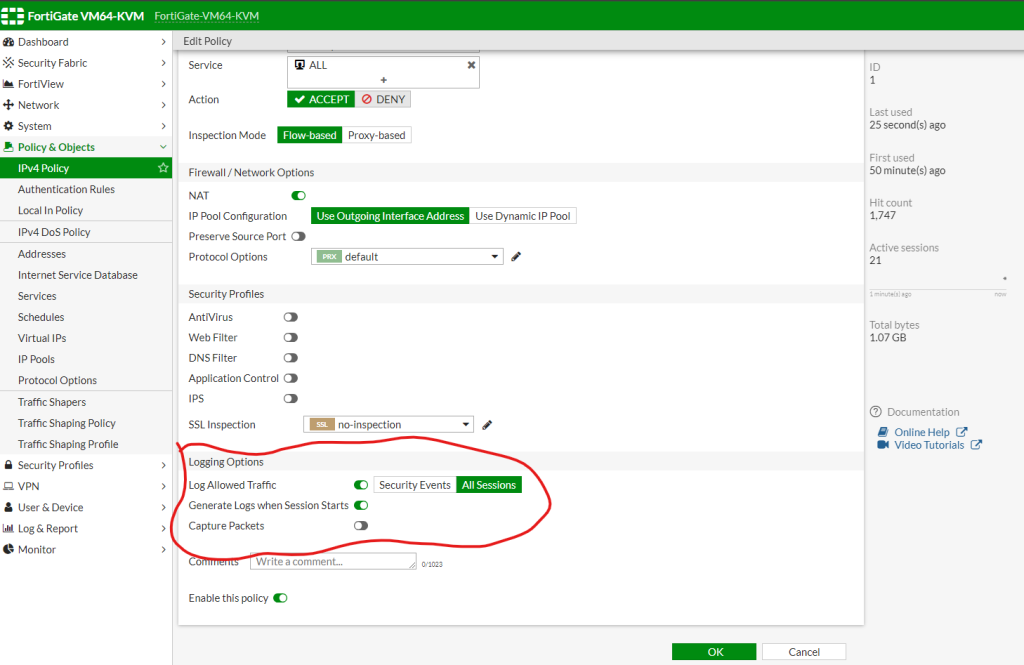
Step 2
# config log memory filter
(filter) # show full-configuration
# config log memory filterset severity warning
set forward-traffic enable
set local-traffic disable
set multicast-traffic enable
set sniffer-traffic enable
set anomaly enable
set voip enable
set dns enable
set ssh enable
set ssl enable
set cifs enable
set filter ”
set filter-type include
end
Change severity level from warning to information. Also enable local traffic logging if it is needed.
#config log memory filter
set severity information
set local-traffic enable
end
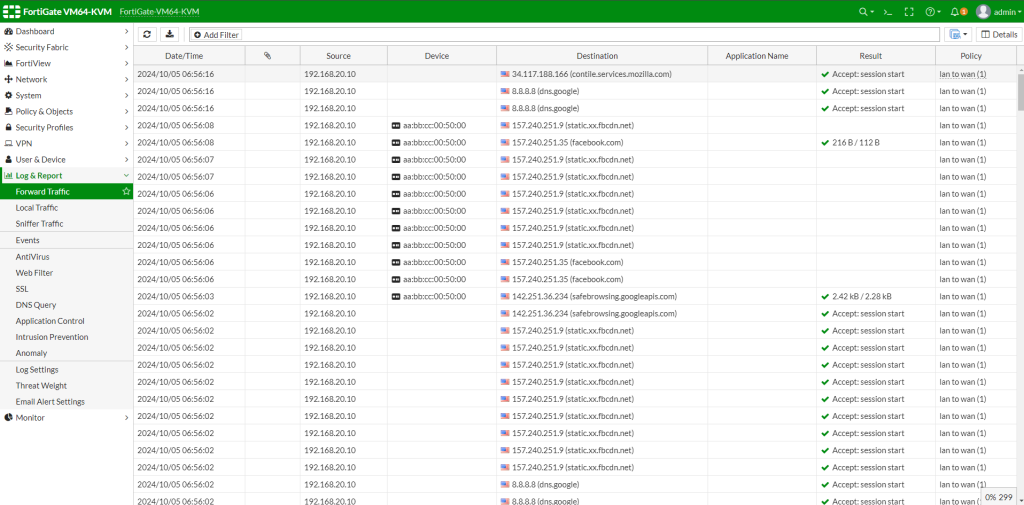
Checking the logs on the firewall
Forward traffic log
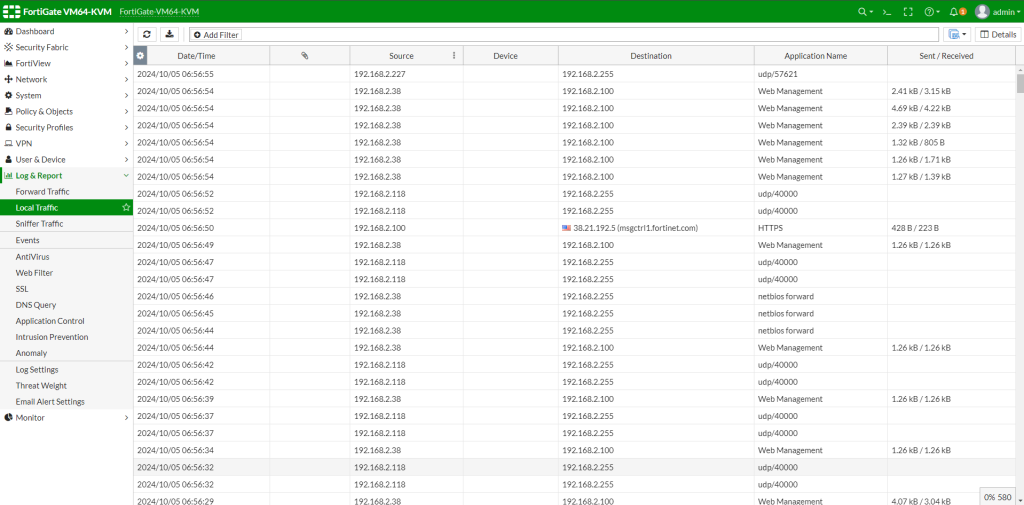
Local traffic logs
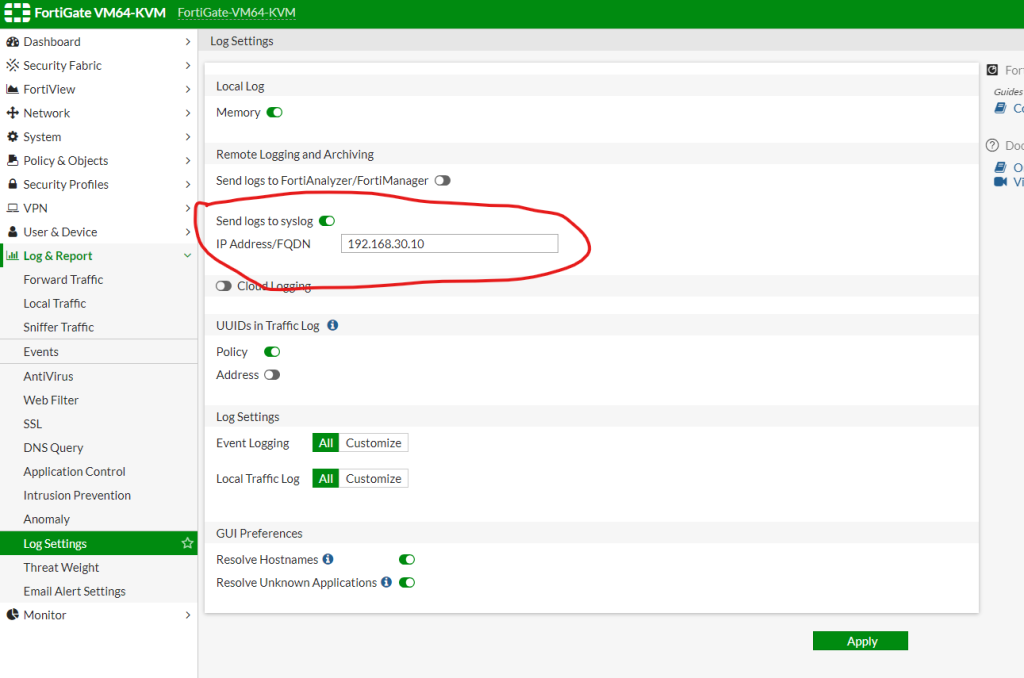
Now we will change the SYSLOG server settings from the firewall.
We will enable this section and type our SYSLOG IP address. Then hit Apply.
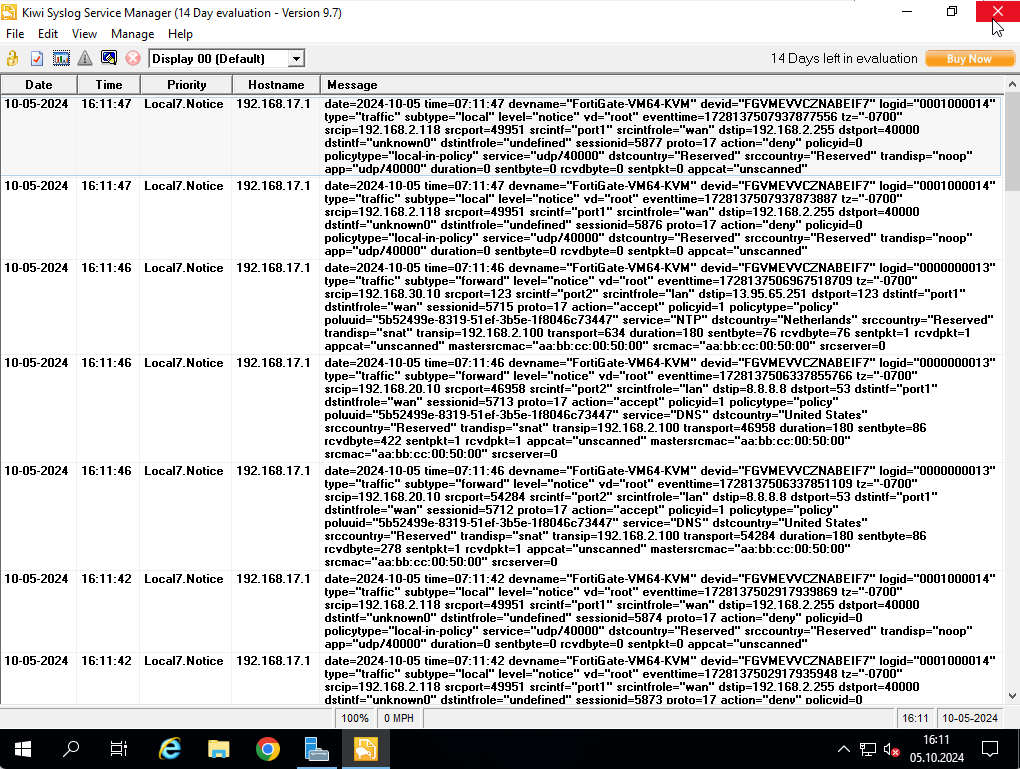
Now on the syslog server side, you will immediately see all the logs. There will be lots of logs due to our severity level is set to information. You can adjust it as you wish according to your need.
Here below you can find the output from syslog server.
Happy networking 🙂