Disclaimer: These methods and techniques are purely for educational and informational purposes. All attacks were carried out in an offline isolated virtual environment. The use of these techniques in normal life is illegal and the responsibility lies strictly with the reader.
DO NOT USE THESE TECHNIQUES IN REAL LIFE !
A CAM table attack, also known as a MAC flooding attack, targets the CAM (Content Addressable Memory) table of a network switch, particularly Cisco switches. The CAM table stores the mapping between MAC addresses and switch port interfaces. This mapping allows the switch to know where to forward Ethernet frames.
Here’s how a CAM table attack works:
- Flooding the CAM Table:
- The attacker sends a large number of Ethernet frames with different, often randomly generated, source MAC addresses.
- The switch tries to store each MAC address in the CAM table along with the associated port number.
- CAM Table Overflow:
- Since the CAM table has a finite size, it eventually fills up due to the massive influx of unique MAC addresses.
- Once the CAM table is full, the switch can no longer learn and store new MAC addresses.
- Resulting Behavior:
- When the CAM table is full, the switch enters a “fail-open” mode and starts flooding incoming traffic out of all ports, as it can no longer determine the correct port for a particular MAC address.
- This behavior essentially turns the switch into a hub, meaning that all traffic is broadcasted to all ports.
- Consequences:
- Network Disruption: This can cause a significant increase in unnecessary traffic across the network, leading to congestion and possible network degradation.
- Data Interception: Because traffic is sent out of all ports, an attacker connected to any port can potentially intercept and capture sensitive data that wasn’t intended for them.
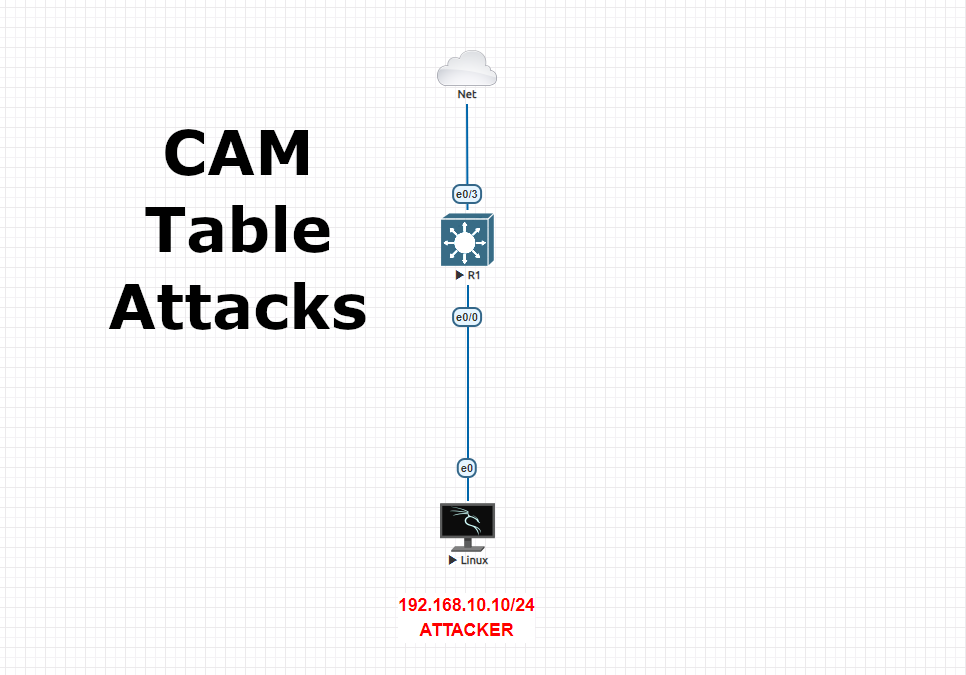
On our topology, we have a Layer3 Cisco switch and a Kali OS connected to that switch via access port. We will use “macof” tool to manipulate the MAC table of Cisco switch as it has limited capacity of MAC memories. In another saying, we will launch a MAC flooding attack.
Switch Configuration
Switch#sh run
Building configuration…Current configuration : 844 bytes
!
! Last configuration change at 19:04:00 UTC Fri Aug 9 2024
!
version 15.1
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
service compress-config
!
hostname Switch
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
!
ip cef
!
!
no ipv6 cef
ipv6 multicast rpf use-bgp
!
spanning-tree mode pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
!
interface Ethernet0/0
switchport access vlan 10
switchport mode access
duplex auto
!
interface Ethernet0/1
duplex auto
!
interface Ethernet0/2
duplex auto
!
interface Ethernet0/3
duplex auto
!
interface Vlan10
ip address 192.168.10.1 255.255.255.0
!
!
no ip http server
!
!
control-plane
!
!
line con 0
logging synchronous
line aux 0
line vty 0 4
!
end
Attack Phase on Kali OS using “macof” tool
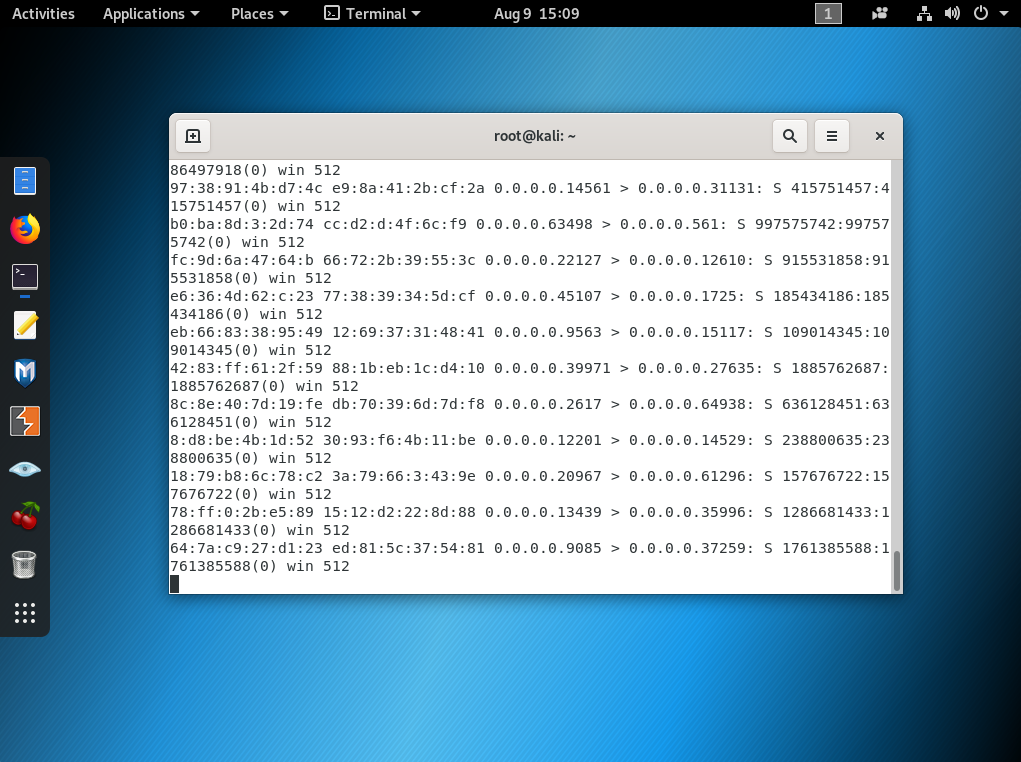

After we launch this attack, it will populate the MAC address table on the switch aggressively, so switch wont be able to operate anymore. This will cause an interruption in the network.
Switch side
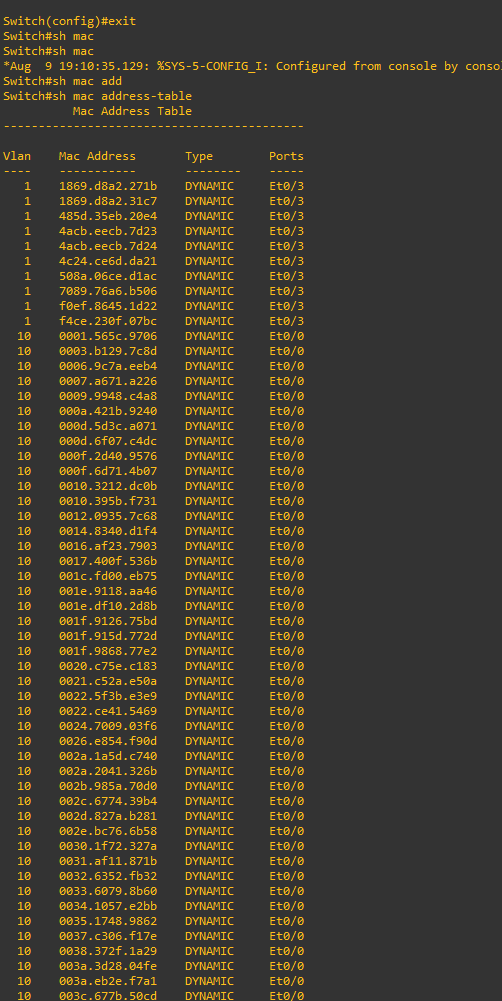
How to prevent this attack?
There are some countermeasures that can be applied to secure access ports. For all access ports, you can implement below codes;
switchport port-security maximum 2
You will limit 2 MAC addresses on this access port.
switchport port-security mac-address sticky
MAC addresses will stick to that specific port and wont change after timeout.
switchport port-security violation shutdown
This is the rule which will shut down the port if it recognizes any flooding attack.
Please feel free to contact me if you have further questions.
Happy networking 🙂