On Cisco networking devices, a syslog server refers to a system or application that collects, stores, and manages log messages generated by the Cisco devices. These log messages contain valuable information about the operation, performance, and events occurring on the network equipment. The syslog server helps network administrators and engineers to monitor, troubleshoot, and analyze the network’s health, security, and performance.
Cisco devices, such as routers, switches, and firewalls, generate various types of syslog messages that provide insights into activities such as system startup, configuration changes, interface status changes, security events, hardware failures, and more. These messages are categorized into severity levels, ranging from informational to critical, to indicate the importance of the event.
By configuring a syslog server on Cisco devices, administrators can direct these log messages to a central location. This has several advantages:
- Centralized Logging: Instead of checking logs on individual devices, administrators can monitor all logs from a single location, simplifying troubleshooting and analysis.
- Long-Term Storage: Log messages can be stored on the syslog server for an extended period, allowing historical analysis and compliance with regulatory requirements.
- Alerts and Notifications: Administrators can set up alerts and notifications based on specific syslog events. This helps in responding promptly to critical issues.
- Security Analysis: Syslog messages can aid in detecting security breaches, unauthorized access attempts, and other potentially malicious activities.
- Capacity Planning: Monitoring syslog messages can help administrators identify trends and patterns, assisting in capacity planning and resource allocation.
Remember that proper syslog configuration also involves specifying the severity levels of messages that should be sent to the syslog server, setting up logging facilities, and potentially adding timestamps to the log messages. The exact configuration steps might vary depending on the specific Cisco device and its operating system version.
| Severity Level | Name | Description |
| 0 | Emergency | Router unusable |
| 1 | Alert | Immediate action required |
| 2 | Critical | Condition critical |
| 3 | Error | Error condition |
| 4 | Warning | Warning condition |
| 5 | Notification | Normal but important event |
| 6 | Informational | Informational messages |
| 7 | Debugging | Debug message |
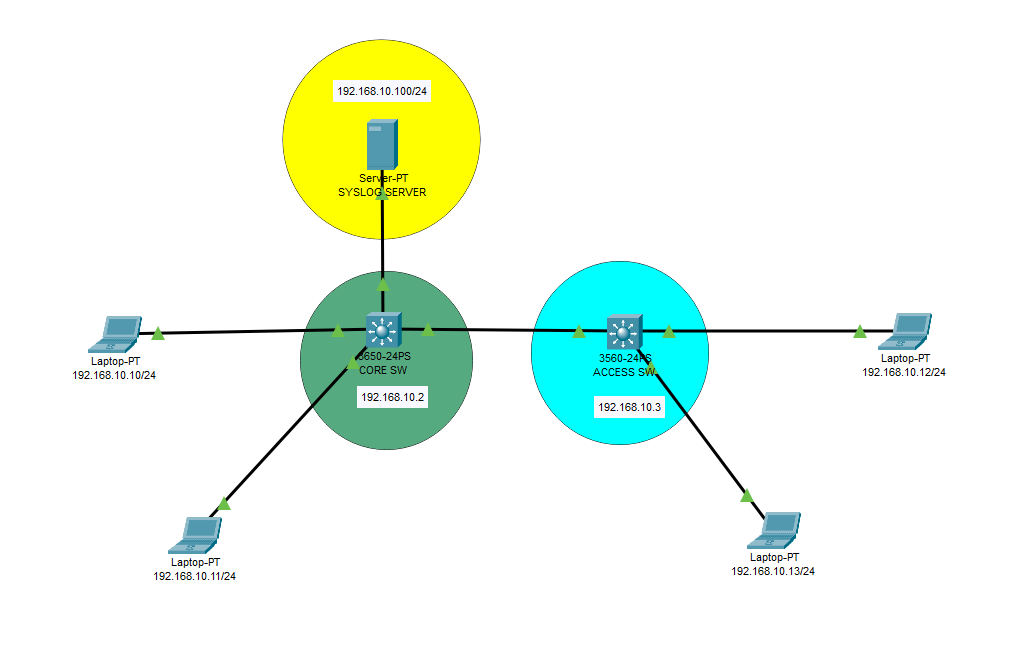
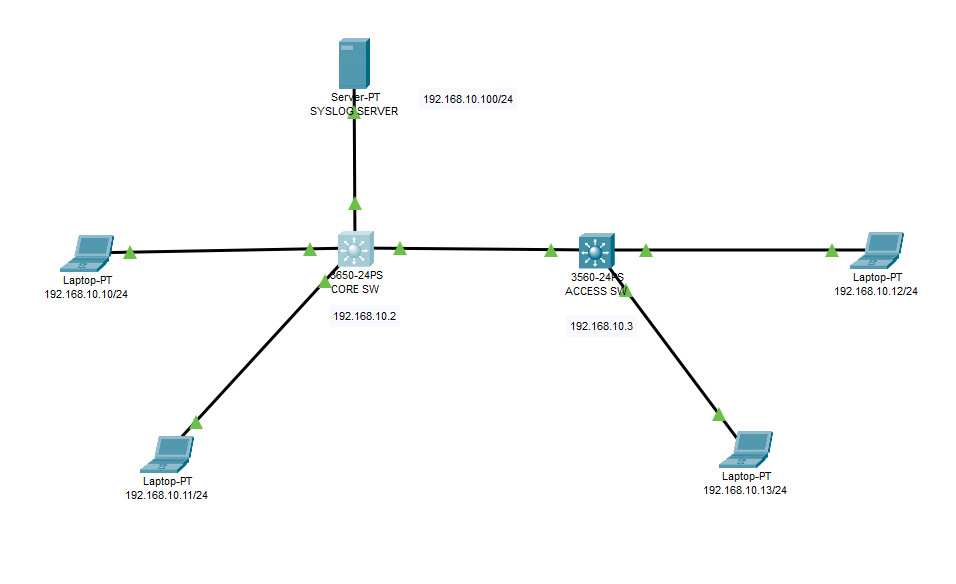
On this topology, syslog server is configured on 192.168.10.100/24. We will activate syslog messages and send them to syslog server. Lets start with Core Switch configuration, then proceed the same configuration on access switch.
SYSLOG CONFIGURATION FOR CORE SWITCH
Switch>enable Switch#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Switch(config)#hostname CORESW CORESW(config)#service timestamps log datetime msec CORESW(config)#logging host 192.168.10.100 CORESW(config)#logging trap debugging CORESW(config)#logging on CORESW(config)#int vlan 1 CORESW(config-if)#ip address 192.168.10.2 255.255.255.0 CORESW(config-if)#no shutdown CORESW(config-if)#exit CORESW(config)#ip routing CORESW(config)#do wr
SYSLOG CONFIGURATION FOR ACCESS SWITCH
Switch>enable Switch#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Switch(config)#hostname ACCESW ACCESW(config)#interface vlan 1 ACCESW(config-if)#ip address 192.168.10.3 255.255.255.0 ACCESW(config-if)#no shutdown ACCESW(config-if)#exit ACCESW(config)#logging on ACCESW(config)#logging host 192.168.10.100 ACCESW(config)#logging trap debugging ACCESW(config)#do wr ACCESW(config)#service timestamp log datetime msec ACCESW(config)#do wr Building configuration... [OK] ACCESW(config)#
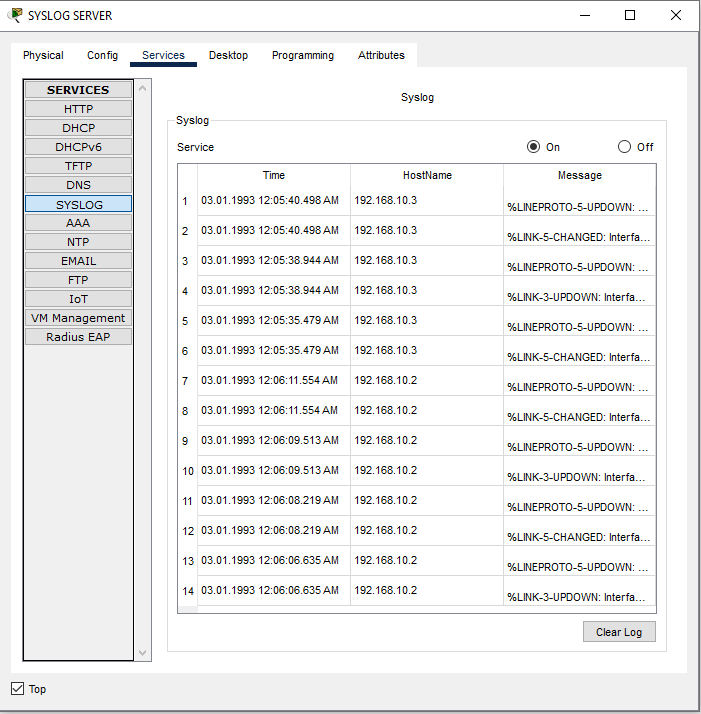
After completing switch configurations, we will configure our Syslog Server. Here in this example we will use Cisco Package Tracer server’s syslog center. But in general, a specific Syslog Software is needed to collect all these logs on a specific server. (like Solarwind etc.)
Create some interactions like unplugging ethernet cables from the switch and plug it on again. Afterwards you will realize that there are logs on the syslog server as you can see below. And you will see the specific IP address under the Hostname section which addresses your switches.
You can download this simulation from the below link.
Do not hesitate to contact me if you have further questions.
Happy networking 🙂