Disclaimer: These methods and techniques are purely for educational and informational purposes. All attacks were carried out in an offline isolated virtual environment. The use of these techniques in normal life is illegal and the responsibility lies strictly with the reader.
DO NOT USE THESE TECHNIQUES IN REAL LIFE !
ARP poisoning and Man-in-the-Middle (MITM) attacks are two related concepts in the realm of network security. Here’s a detailed explanation of each:
ARP Poisoning
Address Resolution Protocol (ARP) is used to map IP addresses to MAC (Media Access Control) addresses, which are used for communication on a local network. ARP poisoning (or ARP spoofing) is a technique by which an attacker sends fake ARP messages to a local network. The goal is to associate the attacker’s MAC address with the IP address of another device (such as the default gateway), effectively causing any traffic meant for that IP address to be sent to the attacker instead.
Steps in ARP Poisoning:
- Broadcast ARP Requests: The attacker sends out ARP requests or replies with the spoofed IP address of a target.
- Cache Poisoning: The devices on the network update their ARP cache with the incorrect MAC address associated with the IP address.
- Intercept Traffic: The attacker now receives traffic meant for the spoofed IP address, allowing them to intercept, modify, or drop packets.
Man-in-the-Middle (MITM) Attack
A MITM attack occurs when an attacker intercepts communication between two parties, allowing them to eavesdrop, manipulate, or alter the communication without either party knowing.
Types of MITM Attacks:
- Passive Attack: The attacker silently listens to the communication without altering any data.
- Active Attack: The attacker actively intercepts and modifies the communication. This can include injecting malicious code, altering messages, or redirecting traffic.
Connection Between ARP Poisoning and MITM
ARP poisoning is often used as a precursor to a MITM attack in a local network. By poisoning the ARP cache of devices, an attacker can place themselves between the communication of two devices (e.g., a client and a server), thus becoming a “man in the middle.”
Example Scenario:
- ARP Poisoning: An attacker sends ARP messages to a victim’s machine, associating their MAC address with the IP address of the default gateway.
- Traffic Interception: The victim’s machine now sends all its traffic to the attacker’s machine, thinking it is the gateway.
- MITM Attack: The attacker can now intercept, monitor, and potentially modify the traffic between the victim and the intended gateway.
Briefing About The Attack and Preparation
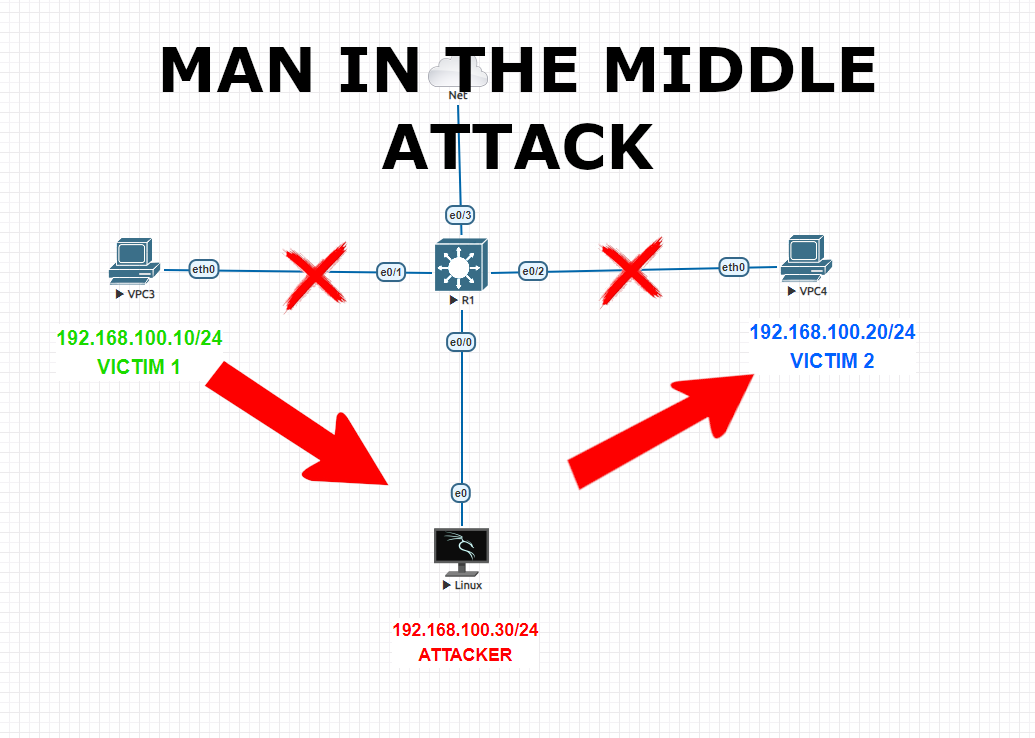
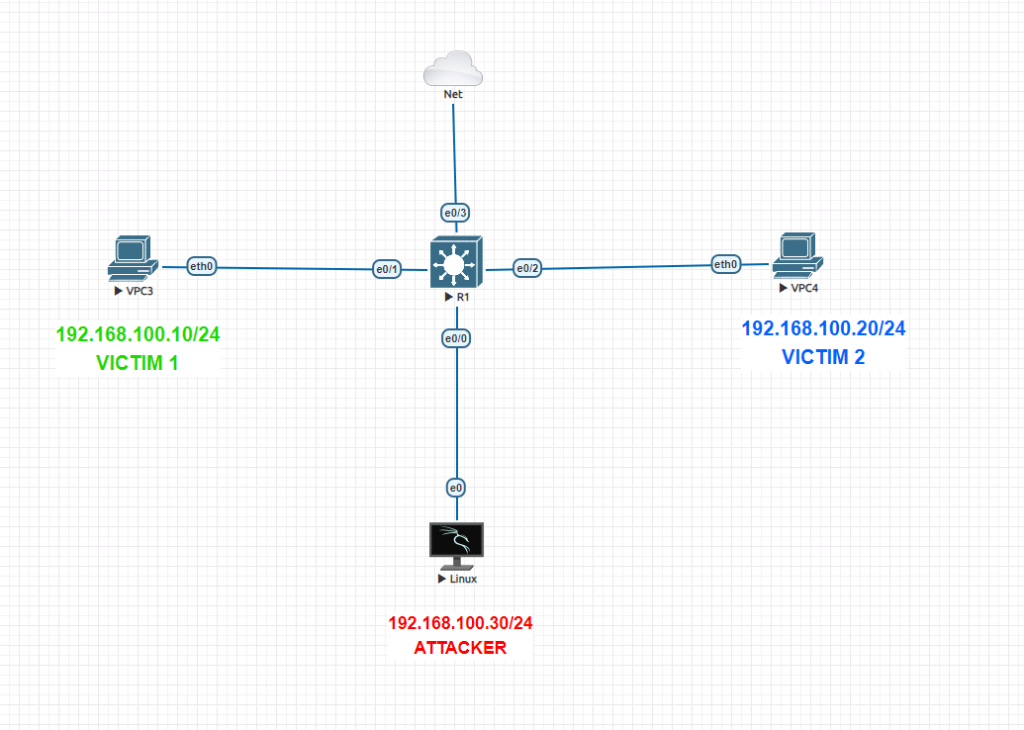
In this lab, there are 2 clients and 1 attacker in the same subnet 172.16.10.0/24
We will manipulate ARP tables on both clients through our attacker client using ‘ettercap‘ . Upon we launch ettercap, ARP tables will be manipulated and Victim 1 will see Attacker’s MAC address instead of Victim 2’s MAC address and same for Victim 2.
We will start pinging each other clients via terminal to create the ARP entries first.
VICTIM 1
VPCS> ping 192.168.100.20
84 bytes from 192.168.100.20 icmp_seq=1 ttl=64 time=0.311 ms
84 bytes from 192.168.100.20 icmp_seq=2 ttl=64 time=0.571 ms
84 bytes from 192.168.100.20 icmp_seq=3 ttl=64 time=0.656 ms
84 bytes from 192.168.100.20 icmp_seq=4 ttl=64 time=0.462 ms
84 bytes from 192.168.100.20 icmp_seq=5 ttl=64 time=0.538 ms
VPCS> ping 192.168.100.30
84 bytes from 192.168.100.30 icmp_seq=1 ttl=64 time=1.006 ms
84 bytes from 192.168.100.30 icmp_seq=2 ttl=64 time=0.642 ms
84 bytes from 192.168.100.30 icmp_seq=3 ttl=64 time=0.610 ms
84 bytes from 192.168.100.30 icmp_seq=4 ttl=64 time=0.578 ms
84 bytes from 192.168.100.30 icmp_seq=5 ttl=64 time=0.641 ms
VPCS> show arp
00:50:79:66:68:04 192.168.100.20 expires in 103 seconds
00:50:00:00:02:00 192.168.100.30 expires in 116 seconds
VPCS>
VICTIM 2
VPCS> ping 192.168.100.10
84 bytes from 192.168.100.10 icmp_seq=1 ttl=64 time=0.699 ms
84 bytes from 192.168.100.10 icmp_seq=2 ttl=64 time=0.487 ms
84 bytes from 192.168.100.10 icmp_seq=3 ttl=64 time=0.430 ms
84 bytes from 192.168.100.10 icmp_seq=4 ttl=64 time=0.412 ms
84 bytes from 192.168.100.10 icmp_seq=5 ttl=64 time=0.502 ms
VPCS> ping 192.168.100.30
84 bytes from 192.168.100.30 icmp_seq=1 ttl=64 time=0.569 ms
84 bytes from 192.168.100.30 icmp_seq=2 ttl=64 time=0.590 ms
84 bytes from 192.168.100.30 icmp_seq=3 ttl=64 time=0.677 ms
84 bytes from 192.168.100.30 icmp_seq=4 ttl=64 time=0.593 ms
84 bytes from 192.168.100.30 icmp_seq=5 ttl=64 time=0.498 ms
VPCS> show arp
00:50:79:66:68:03 192.168.100.10 expires in 32 seconds
00:50:00:00:02:00 192.168.100.30 expires in 118 seconds
VPCS>
Now we will launch ettercap attack to poison ARP tables.
1-)Start ettercap from terminal via ‘sudo ettercap -G’ to see the graphical user interface
2-)Then click on Hosts > Host List then Scan the network.
3-)Now after scanning it will populate the list with these 2 victim clients.
4-)Then add the targets accordingly.
5-)Click on Mitm > Arp Poisoning and check the Sniff remote connections and click OK.
6-)This attack will poison the client ARP tables and will change our attackers MAC with other victim’s MAC. This is just an example, you can also set another machines on the network like switch or router to manipulate the traffic. In this way, victim will send its packages instead of destination network device and it will assume that it is reaching to mentioned destination.
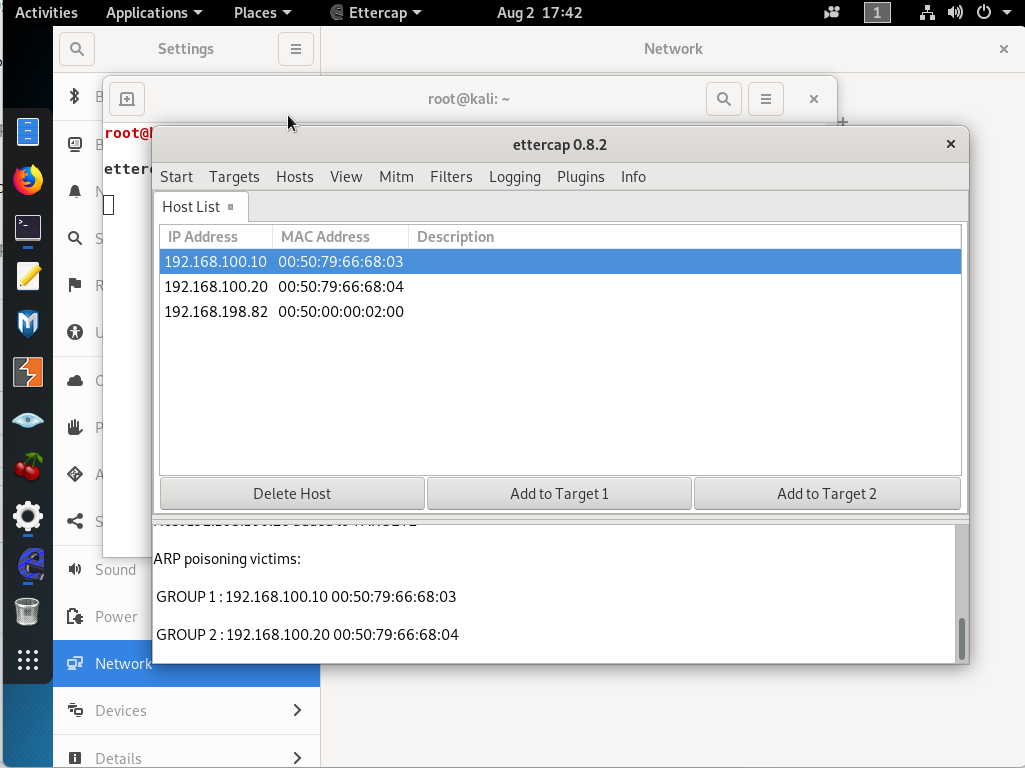
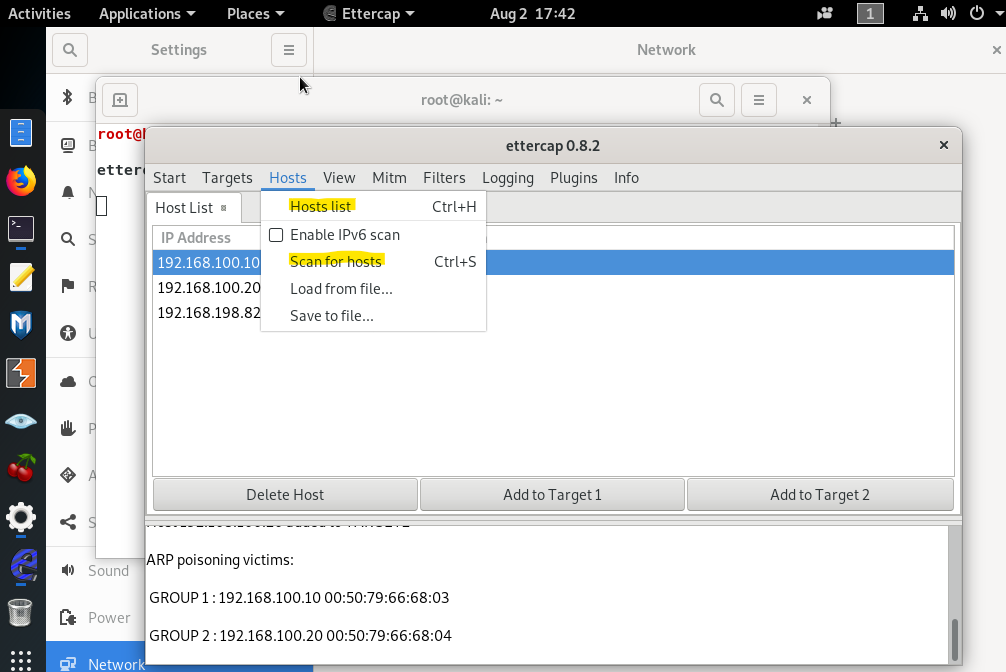
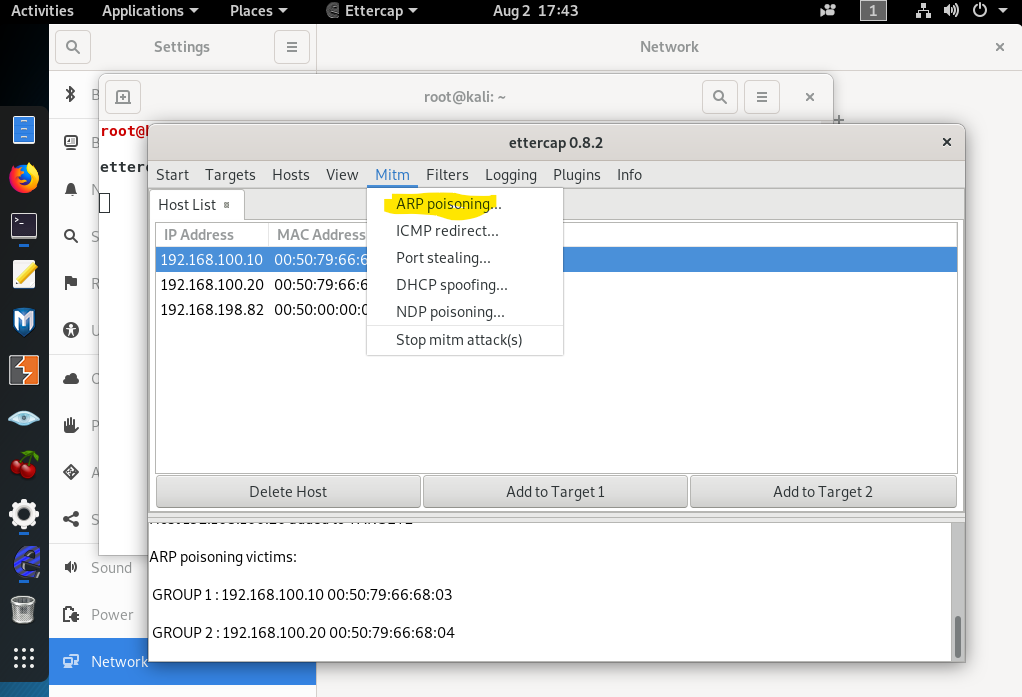
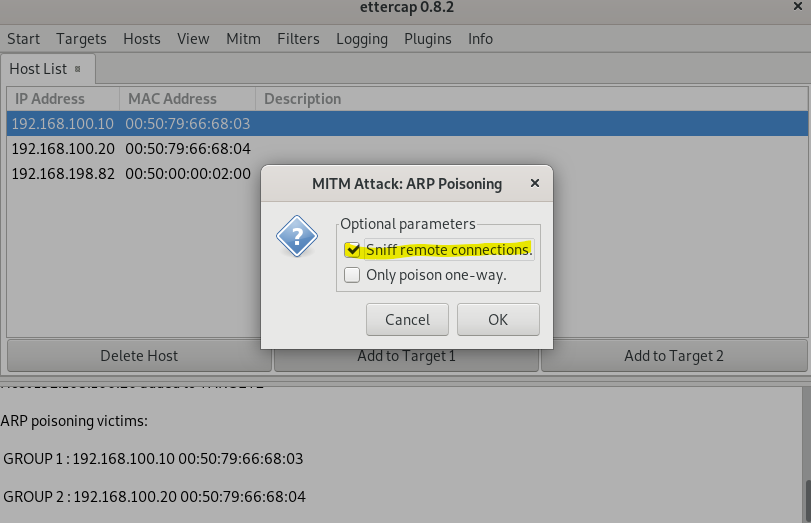
After the attack, you will realize on the client side MAC table has been poisoned and changed.
As in the below example
VPCS> show arp
00:50:79:66:68:03 192.168.100.10 expires in 32 seconds
00:50:79:66:68:03 192.168.100.30 expires in 118 seconds
How To Prevent This Attack?
There are few things which need to be done on the switch side as follow.
Switch# ip dhcp snooping
Switch# ip dhcp snooping vlan XX
Switch# ip arp inspection vlan XX
On the connected port of DHCP server, on the switch side (Lets assume that DHCP server is connected on G1/0/1:
Switch# configure terminal
Switch# interface g1/0/1
Switch# ip dhcp snooping trust
Switch# ip arp inspection trust
Please feel free to contact me if you have any questions.
Happy networking 🙂