Disclaimer: These methods and techniques are purely for educational and informational purposes. All attacks were carried out in an offline isolated virtual environment. The use of these techniques in normal life is illegal and the responsibility lies strictly with the reader.
DO NOT USE THESE TECHNIQUES IN REAL LIFE !
CDP Attack (Cisco Discovery Protocol)
A CDP attack exploits the Cisco Discovery Protocol, which is used by Cisco devices to share information about themselves, such as IP address, software version, and capabilities. Since CDP is a Layer 2 protocol and operates in plain text, it can be easily intercepted by an attacker who has access to the network. An attacker can use the information gathered from CDP to plan further attacks, such as:
- Reconnaissance: Gather information about the network devices, including their model, software version, and IP addresses, to plan targeted attacks.
- Denial of Service (DoS): By sending crafted CDP packets, an attacker can potentially crash or disrupt the operation of network devices that mishandle the unexpected or malformed packets.
- Network Mapping: CDP provides detailed information about the network topology, which can be used to identify critical devices and potential weak points.
LLDP Attack (Vendor-free Open Standard Term)
LLDP is a vendor-neutral protocol similar to CDP, used for network device discovery. It is also used to advertise device information and capabilities. LLDP attacks are similar to CDP attacks, but LLDP is not limited to Cisco devices and can be found in multi-vendor environments.
Potential LLDP attack scenarios include:
- Information Gathering: Similar to CDP, LLDP can provide detailed information about network devices, which can be useful for an attacker in planning subsequent attacks.
- Denial of Service (DoS): By sending malicious LLDP packets, an attacker can potentially exploit vulnerabilities in the protocol implementation of the receiving devices, causing disruptions.
- Network Topology Discovery: Attackers can use LLDP to discover the network topology and identify key devices for further exploitation.
ATTACK BRIEFING AND PREPARATION
In this lab, we will use CDP packages to the switch where we are connected. With this DDOS kind of attack, switch will have enormous numbers of packages then it wont be able to operate normally. This will cause a corruption in the network for a while.
First we will prepare necessary VLANs, subnets and end users. Then we will set Kali OS with necessary IP configurations. In this attack method, we will use Yersinia tool to send CDP packages. We will create 2 vlans as VLAN10 and VLAN20 with 10.0 and 20.0 networks.
Switch Configuration
Switch>en
Switch#sh run
Building configuration…
Current configuration : 899 bytes
!
version 15.1
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
service compress-config
!
hostname Switch
!
boot-start-marker
boot-end-marker
!
no aaa new-model
!
ip cef
!
no ipv6 cef
ipv6 multicast rpf use-bgp
!
spanning-tree mode pvst
spanning-tree extend system-id
!
!
vlan internal allocation policy ascending
!
!
interface Ethernet0/0
switchport access vlan 10
switchport mode access
duplex auto
!
interface Ethernet0/1
switchport access vlan 20
switchport mode access
duplex auto
!
interface Ethernet0/2
duplex auto
!
interface Ethernet0/3
duplex auto
!
interface Vlan10
ip address 192.168.10.1 255.255.255.0
!
interface Vlan20
ip address 192.168.20.1 255.255.255.0
!
no ip http server
!
control-plane
!
!
line con 0
logging synchronous
line aux 0
line vty 0 4
login
!
end
Switch#
CDP Packages Before The Attack
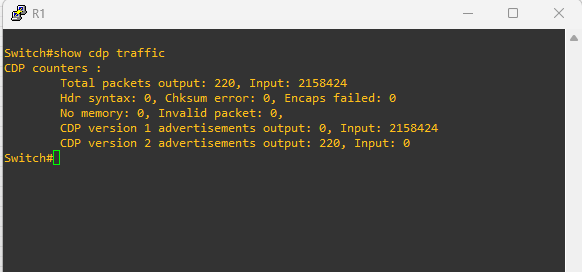
Switch#show cdp traffic
CDP counters :
Total packets output: 208, Input: 0
Hdr syntax: 0, Chksum error: 0, Encaps failed: 0
No memory: 0, Invalid packet: 0,
CDP version 1 advertisements output: 0, Input: 0
CDP version 2 advertisements output: 208, Input: 0
Switch#show cdp neighbor
Capability Codes: R – Router, T – Trans Bridge, B – Source Route Bridge
S – Switch, H – Host, I – IGMP, r – Repeater, P – Phone,
D – Remote, C – CVTA, M – Two-port Mac Relay
Device ID Local Intrfce Holdtme Capability Platform Port ID
Switch#
Attack Phase (Yersinia)
Launch Yersinia through terminal via ‘sudo yersinia -G’ this will open up a graphical user interface. Then choose CDP, then select CDP flooding as below. Then start the attack.
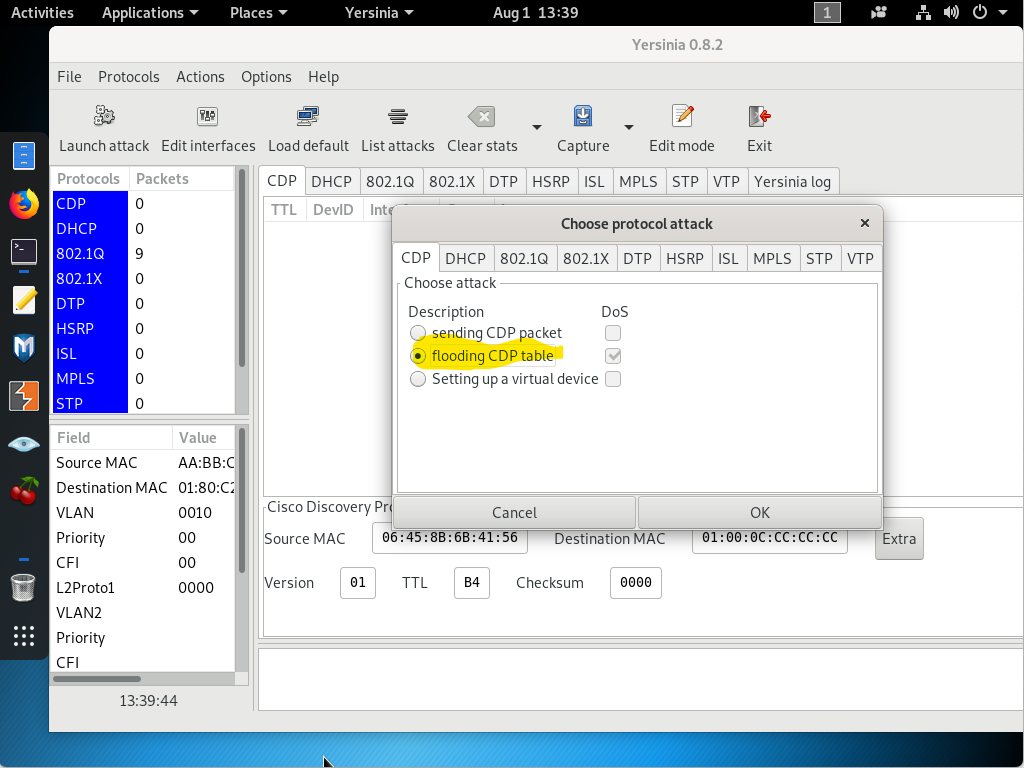
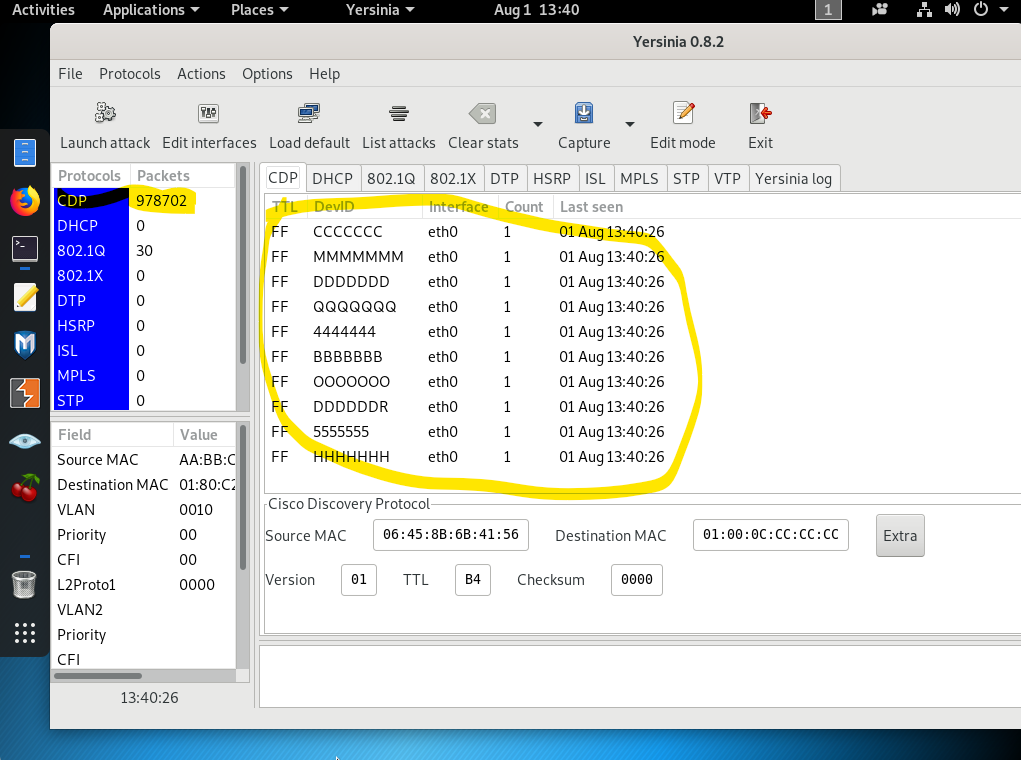
As you can easily recognize, on the switch side Incoming CDP packets are way more than expected and it wont stop unless you stop the attack or switch fails.
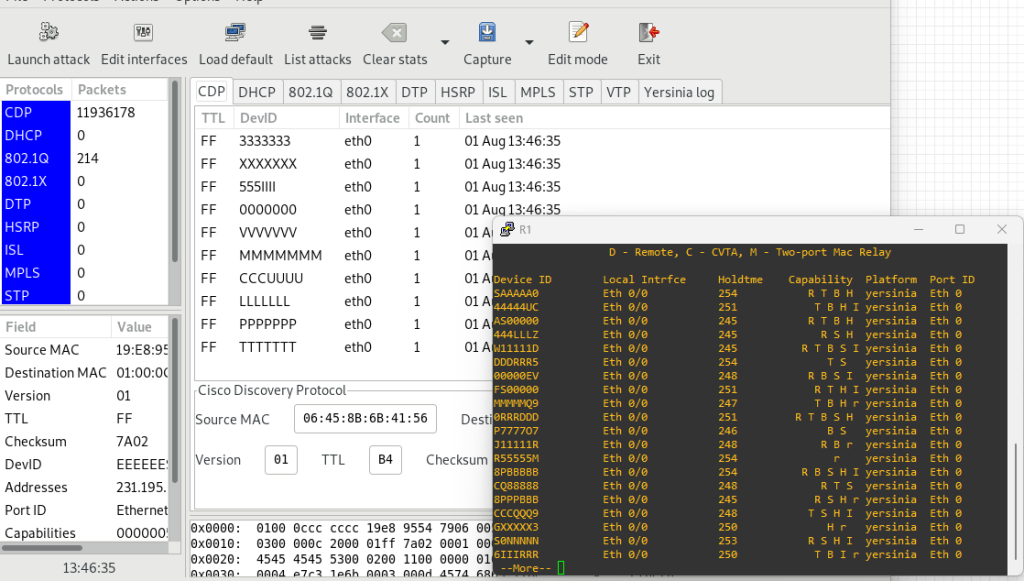
Also you can see the entries via using ‘show cdp neighbors’ command as below. Unless you stop the attack, switch OS wont be able to determine whether this cdp packages are valid or not. Once you stop the attack, switch will eliminate fake packages.
How To Prevent This Attack?
There are some easy countermeasures that you can set.
Set below command except the trunk (802.1q) ports for each interface. This will disable CDP packages input and output.
‘no cdp enable’
This basic command will prevent CDP attacks on access ports of Cisco switch.
Please do not hesitate to contact me if you have any questions.
Happy networking 🙂